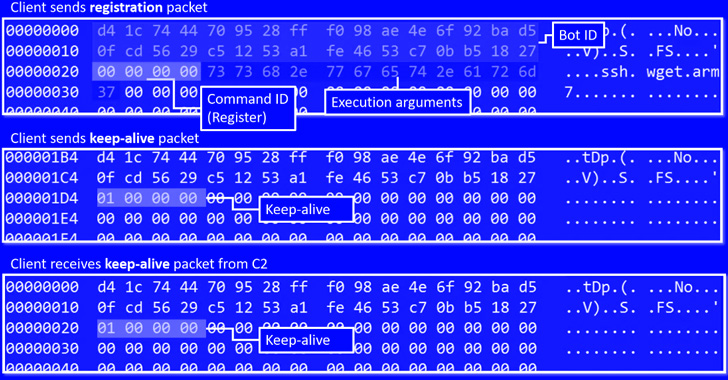
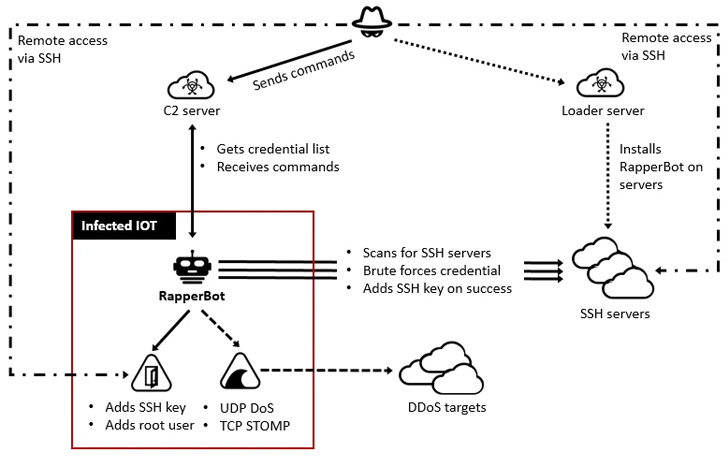
A brand new IoT botnet malware dubbed RapperBot has been noticed quickly evolving its capabilities because it was first found in mid-June 2022.
“This household borrows closely from the unique Mirai supply code, however what separates it from different IoT malware households is its built-in functionality to brute pressure credentials and achieve entry to SSH servers as an alternative of Telnet as applied in Mirai,” Fortinet FortiGuard Labs stated in a report.
The malware, which will get its identify from an embedded URL to a YouTube rap music video in an earlier model, is claimed to have amassed a rising assortment of compromised SSH servers, with over 3,500 distinctive IP addresses used to scan and brute-force their manner into the servers.
RapperBot’s present implementation additionally delineates it from Mirai, permitting it to primarily perform as an SSH brute-force device with restricted capabilities to hold out distributed denial-of-service (DDoS) assaults.
The deviation from conventional Mirai habits is additional evidenced in its try to determine persistence on the compromised host, successfully allowing the risk actor to take care of long-term entry lengthy after the malware has been eliminated or the gadget has been rebooted.
The assaults entail brute-forcing potential targets utilizing an inventory of credentials acquired from a distant server. Upon efficiently breaking right into a susceptible SSH server, the legitimate credentials are exfiltrated again to the command-and-control.
“Since mid-July, RapperBot has switched from self-propagation to sustaining distant entry into the brute-forced SSH servers,” the researchers stated.
The entry is achieved by including the operators’ SSH public key to a particular file known as “~/.ssh/authorized_keys,” allowing the adversary to attach and authenticate to the server utilizing the corresponding non-public non-public key with out having to furnish a password.
“This presents a risk to compromised SSH servers as risk actors can entry them even after SSH credentials have been modified or SSH password authentication is disabled,” the researchers defined.
“Furthermore, because the file is changed, all present approved keys are deleted, which prevents official customers from accessing the SSH server by way of public key authentication.”
The shift additionally permits the malware to take care of its entry to those hacked gadgets by way of SSH, allowing the actor to leverage the foothold to conduct Mirai-styled denial-of-service assaults.
These variations from different IoT malware households have had the side-effect of constructing its main motivations one thing of a thriller, a truth additional sophisticated by the truth that RapperBot’s authors have left little-to-no telltale indicators of their provenance.
The ditching of self-propagation in favor of persistence however, the botnet is claimed to have undergone important adjustments in a brief span of time, chief amongst them being the removing of DDoS assault options from the artifacts at one level, solely to be reintroduced per week later.
The targets of the marketing campaign, in the end, stay nebulous at finest, with no follow-on exercise noticed submit a profitable compromise. What’s clear is that SSH servers with default or guessable credentials are being corralled right into a botnet for some unspecified future function.
To fend off such infections, it is really helpful that customers set robust passwords for gadgets or disable password authentication for SSH the place doable.
“Though this risk closely borrows code from Mirai, it has options that set it aside from its predecessor and its variants,” the researchers stated. “Its skill to persist within the sufferer system provides risk actors the flexibleness to make use of them for any malicious function they want.”