Lengthy gone are the times of cheesy touchdown pages that hardly impersonate a model; menace actors are enhancing their social engineering sport nicely sufficient to make anybody imagine it’s the true factor.
Lengthy gone are the times of cheesy touchdown pages that hardly impersonate a model; menace actors are enhancing their social engineering sport nicely sufficient to make anybody imagine it’s the true factor.
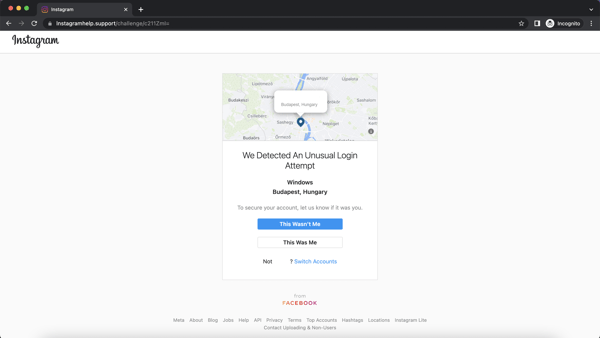
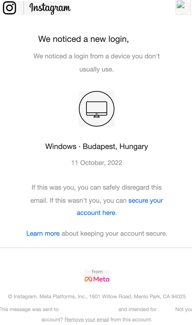
Safety researchers at Armorblox present crucial particulars right into a new Instagram impersonation rip-off with elements of the assault wanting very credible. In accordance with Armorblox, the rip-off focused over 22,000 customers at a single giant academic establishment. The rip-off began with a realistic-looking e mail claiming to be from Instagram assist:
Upon clicking “safe your account right here”, customers are taken to an impersonated Instagram assist web page the place the sufferer can assert that the “uncommon logon” was or wasn’t them.
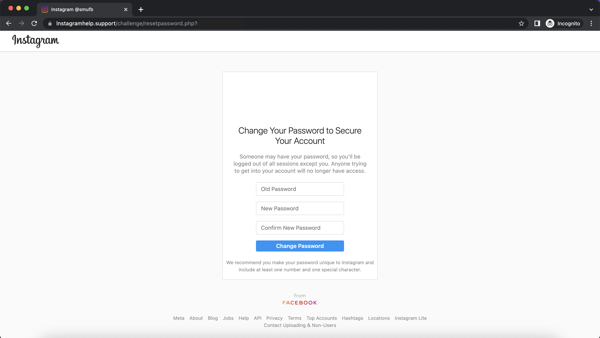
Lastly, victims are taken to a web page to “reset” their password. The one assume on this web page of curiosity to the scammer is the customers “outdated” (learn: present) password, which will likely be used to logon to the victims Instagram account and leverage it to trick followers in a subsequent rip-off.
On the finish of the day, there’s one a part of nearly any phishing assault that doesn’t appear to jibe – the e-mail sender’s area. As a result of menace actors are sometimes utilizing throwaway domains, the occasion of “instagramsupport [dot] web” within the e mail above – which does align with the branding pretty nicely – is fairly spectacular and weird.
Company customers ought to be taught through Safety Consciousness Coaching to be watchful for any sudden emails and scrutinize the sender’s e mail deal with; if it seems flawed, it ought to be thought of suspect and ignored.