A novel Go-based botnet known as Zerobot has been noticed within the wild proliferating by profiting from practically two dozen safety vulnerabilities within the web of issues (IoT) gadgets and different software program.
The botnet “accommodates a number of modules, together with self-replication, assaults for various protocols, and self-propagation,” Fortinet FortiGuard Labs researcher Cara Lin mentioned. “It additionally communicates with its command-and-control server utilizing the WebSocket protocol.”
The marketing campaign, which is claimed to have commenced after November 18, 2022, primarily singles out the Linux working system to realize management of susceptible gadgets.
Zerobot will get its title from a propagation script that is used to retrieve the malicious payload after having access to a number relying on its microarchitecture implementation (e.g., “zero.arm64”).
The malware is designed to focus on a variety of CPU architectures similar to i386, amd64, arm, arm64, mips, mips64, mips64le, mipsle, ppc64, ppc64le, riscv64, and s390x.
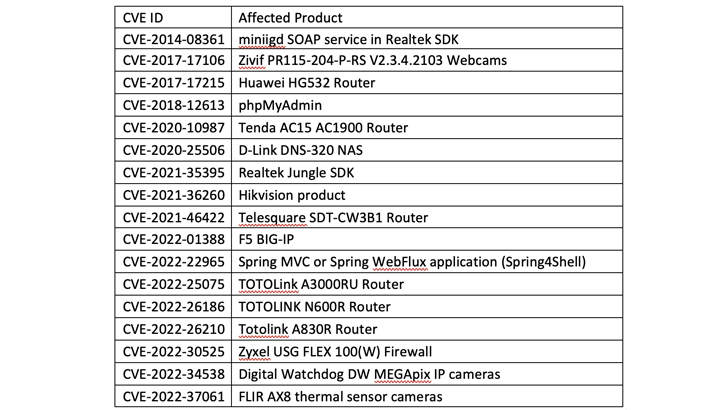
Two variations of Zerobot have been noticed to this point: One used earlier than November 24, 2022, that comes with fundamental capabilities and an up to date variant that features a self-propagating module to breach different endpoints utilizing 21 exploits.
This contains vulnerabilities impacting TOTOLINK routers, Zyxel firewalls, F5 BIG-IP, Hikvision cameras, FLIR AX8 thermal imaging cameras, D-Hyperlink DNS-320 NAS, and Spring Framework, amongst others.
Zerobot, upon initialization within the compromised machine, establishes contact with a distant command-and-control (C2) server and awaits additional directions that enable it to run arbitrary instructions and launch assaults for various community protocols like TCP, UDP, TLS, HTTP, and ICMP.
“Inside a really brief time, it was up to date with string obfuscation, a replica file module, and a propagation exploit module that make[s] it more durable to detect and offers it the next functionality to contaminate extra gadgets,” Lin mentioned.