A brand new phishing-as-a-service (PhaaS) toolkit dubbed EvilProxy is being marketed on the prison underground as a way for risk actors to bypass two-factor authentication (2FA) protections employed in opposition to on-line companies.
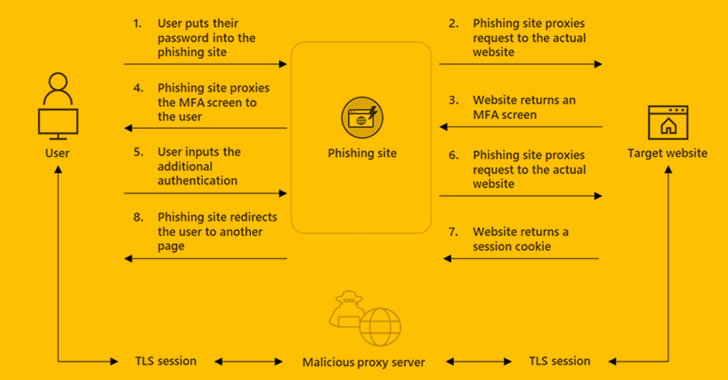
“EvilProxy actors are utilizing reverse proxy and cookie injection strategies to bypass 2FA authentication – proxifying sufferer’s session,” Resecurity researchers mentioned in a Monday write-up.
The platform generates phishing hyperlinks which are nothing however cloned pages designed to compromise person accounts related to Apple iCloud, Fb, GoDaddy, GitHub, Google, Dropbox, Instagram, Microsoft, NPM, PyPI, RubyGems, Twitter, Yahoo, and Yandex, amongst others.
EvilProxy is much like adversary-in-the-middle (AiTM) assaults in that customers work together with a malicious proxy server that acts as a go-between for the goal web site, covertly harvesting the credentials and 2FA passcodes entered within the login pages.
It is supplied on a subscription foundation per service for a time interval of 10, 20, or 31 days, with the package obtainable for $400 a month and accessed over the TOR anonymity community after the fee is organized manually with an operator on Telegram. Assaults in opposition to Google accounts, in distinction, price as much as $600 per thirty days.
“After activation, the operator might be requested to offer SSH credentials to additional deploy a Docker container and a set of scripts,” Resecurity mentioned, including the method mirrors that of one other PhaaS service known as Frappo that got here to mild earlier this 12 months.
Whereas the sale of EvilProxy to potential clients is topic to vetting by the actors, it goes with out saying that the service affords a “cost-effective and scalable answer” to hold out social engineering assaults.
The event is additional a sign that adversaries are upgrading their assault arsenal to orchestrate refined phishing campaigns focusing on customers in a way that may defeat present safety safeguards.
So as to add to the considerations, the focusing on of public-facing code and bundle repositories corresponding to GitHub, NPM, PyPI, and RubyGems means that the operators are additionally aiming to facilitate provide chain assaults through such operations.
Gaining unauthorized entry to accounts and injecting malicious code into extensively used initiatives by trusted builders could be a goldmine for risk actors, considerably widening the impression of the campaigns.
“It is extremely seemingly the actors intention to focus on software program builders and IT engineers to achieve entry to their repositories with the top purpose to hack ‘downstream’ targets,” the researchers mentioned.