Cybersecurity researchers have elaborated a novel assault approach that weaponizes programmable logic controllers (PLCs) to realize an preliminary foothold in engineering workstations and subsequently invade the operational know-how (OT) networks.
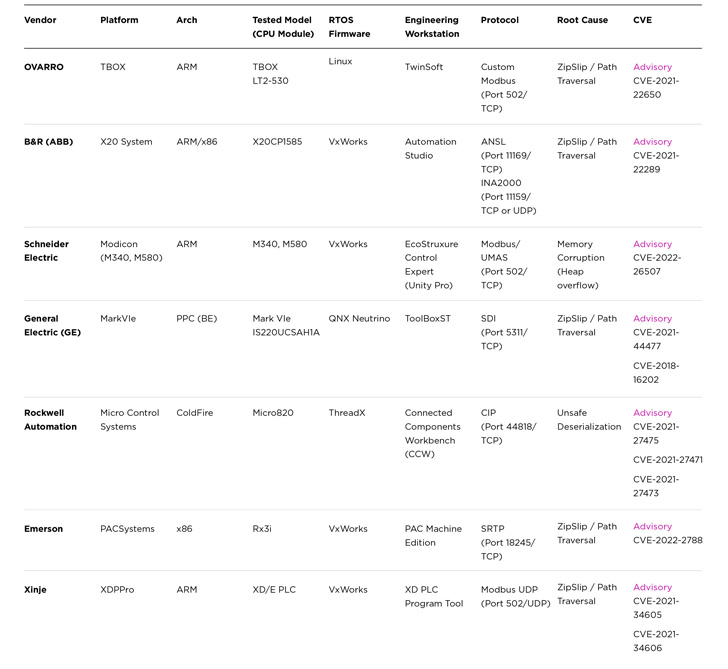
Dubbed “Evil PLC” assault by industrial safety agency Claroty, the difficulty impacts engineering workstation software program from Rockwell Automation, Schneider Electrical, GE, B&R, Xinje, OVARRO, and Emerson.
Programmable logic controllers (PLCs) are an important element of commercial units that management manufacturing processes in crucial infrastructure sectors. PLCs, in addition to orchestrating the automation duties, are additionally configured to begin and cease processes and generate alarms.
It is therefore not shocking that the entrenched entry offered by PLCs have made the machines a spotlight of refined assaults for greater than a decade, ranging from Stuxnet to PIPEDREAM (aka INCONTROLLER), with the purpose of inflicting bodily disruptions.
“These workstation functions are sometimes a bridge between operational know-how networks and company networks,” Claroty mentioned. “An attacker who is ready to compromise and exploit vulnerabilities in an engineering workstation may simply transfer onto the interior community, transfer laterally between methods, and achieve additional entry to different PLCs and delicate methods.”
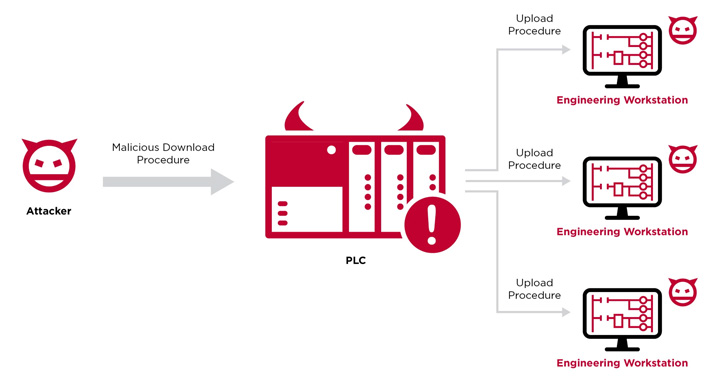
With the Evil PLC assault, the controller acts as a method to an finish, allowing the risk actor to breach a workstation, entry to all the opposite PLCs on the community, and even tamper with the controller logic.
Put in another way, the concept is to “use the PLC as a pivot level to assault the engineers who program and diagnose it and achieve deeper entry to the OT community,” the researchers mentioned.
The entire sequence performs out as follows: An opportunistic adversary intentionally induces a malfunction on an internet-exposed PLC, an motion that prompts an unsuspecting engineer to connect with the contaminated PLC utilizing the engineering workstation software program as a troubleshooting device.
Within the subsequent section, the unhealthy actor leverages the beforehand undiscovered flaws recognized within the platforms to execute malicious code on the workstation when an add operation is carried out by the engineer to retrieve a working copy of the prevailing PLC logic.
“The truth that the PLC shops extra varieties of information which can be utilized by the engineering software program and never the PLC itself” creates a state of affairs whereby the unused information saved on the PLC could be modified to control the engineering software program, the researchers identified.
“Usually, the vulnerabilities exist as a result of the software program totally trusted information coming from the PLC with out performing intensive safety checks.”
In another theoretical assault state of affairs, the Evil PLC technique will also be used as honeypots to lure risk actors into connecting to a decoy PLC, resulting in a compromise of the attacker’s machine.
Claroty additional referred to as out the absence of safety protections within the public-facing industrial management system (ICS) units, thereby making it simpler for risk actors to change their logic by way of rogue obtain procedures.
To mitigate such assaults, it is really useful to restrict bodily and community entry to PLCs to licensed engineers and operators, implement authentication mechanisms to validate the engineering station, monitor OT community visitors for anomalous exercise, and apply patches in a well timed style.