Entities positioned in East and Southeast Asia in addition to Ukraine have been focused at the very least since 2020 by a beforehand undocumented subgroup of APT41, a prolific Chinese language superior persistent menace (APT).
Cybersecurity agency Development Micro, which christened the espionage crew Earth Longzhi, stated the actor’s long-running marketing campaign may be break up into two based mostly on the toolset deployed to assault its victims.
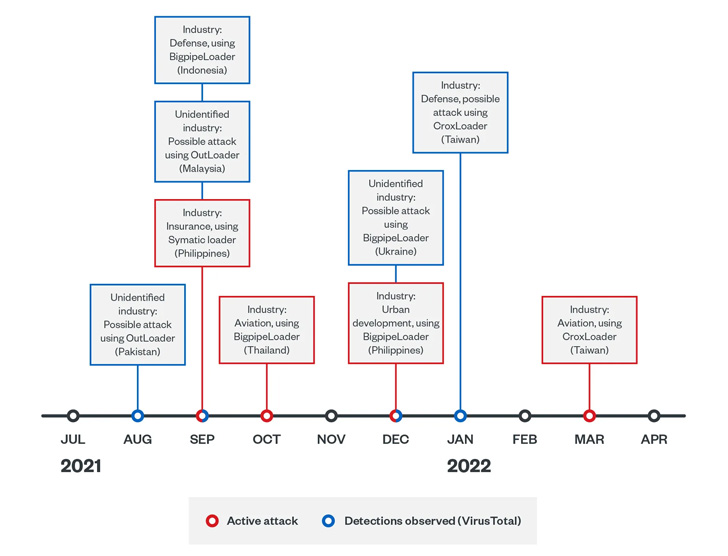
The primary wave from Might 2020 to February 2021 is alleged to have focused authorities, infrastructure, and healthcare industries in Taiwan and the banking sector in China, whereas the succeeding set of intrusions from August 2021 to June 2022 infiltrated high-profile victims in Ukraine and several other international locations in Asia.
This included protection, aviation, insurance coverage, and concrete improvement industries in Taiwan, China, Thailand, Malaysia, Indonesia, Pakistan, and Ukraine.
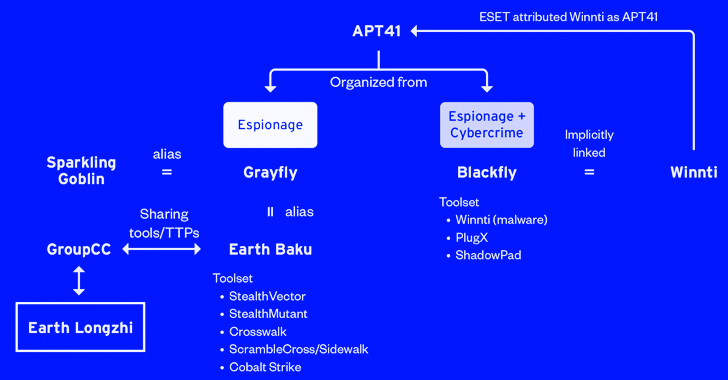
The victimology patterns and the focused sectors overlap with assaults mounted by a definite sister group of APT41 (aka Winnti) often called Earth Baku, the Japanese cybersecurity firm added.
A few of Earth Baku’s malicious cyber actions have been tied to teams referred to as by different cybersecurity companies ESET and Symantec underneath the names SparklingGoblin and Grayfly, respectively.
“SparklingGoblin’s Ways, Strategies and Procedures (TTPs) partially overlap with APT41 TTPs,” ESET researcher Mathieu Tartare beforehand advised The Hacker Information. “Grayfly’s definition given by Symantec appears to (at the very least partially) overlap with SparklingGoblin.”
Now Earth Longzhi provides to a different piece within the APT41 assault puzzle, what with the actor additionally sharing hyperlinks to a 3rd subgroup dubbed GroupCC (aka APT17, Aurora Panda, or Bronze Keystone).
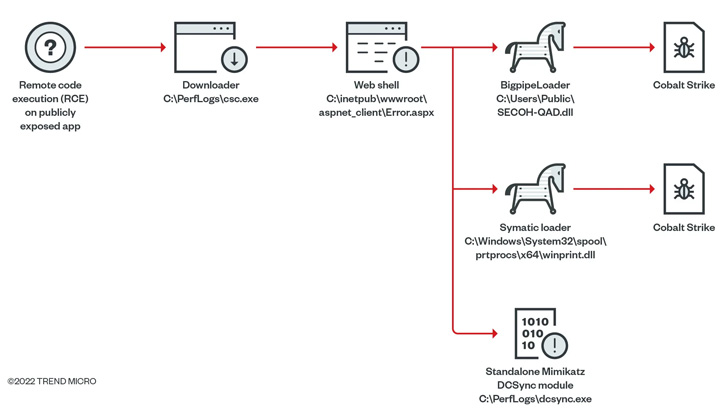
Assaults orchestrated by the hacker group leverage spear-phishing emails because the preliminary entry vector. These messages are recognized to embed password-protected archives or hyperlinks to recordsdata hosted on Google Drive that, when opened, launches a Cobalt Strike loader dubbed CroxLoader.
In some instances, the group has been noticed weaponizing distant code execution flaws in publicly uncovered purposes to ship an internet shell able to dropping a next-stage loader known as Symatic that is engineered to deploy Cobalt Strike.
Additionally put to make use of as a part of its post-exploitation actions is an “multi functional device,” which mixes a number of publicly accessible and customized features in a single package deal and is believed to have been accessible since September 2014.
The second sequence of assaults initiated by Earth Longzhi observe the same sample, the principle distinction being the usage of totally different Cobalt Strike loaders named CroxLoader, BigpipeLoader, and OutLoader to drop the crimson group framework on contaminated hosts.
The latest assaults additional stand out for the usage of bespoke instruments that may disable safety software program, dump credentials utilizing a modified model of Mimikatz, and leverage flaws within the Home windows Print Spooler element (i.e., PrintNightmare) to escalate privileges.
What’s extra, incapacitating the put in safety options is pulled off by a technique referred to as convey your individual susceptible driver (BYOVD), which entails the exploitation of a recognized flaw within the RTCore64.sys driver (CVE-2019-16098).
That is carried out utilizing ProcBurner, a device for killing particular working processes, whereas one other customized malware referred to as AVBurner is used to unregister the endpoint detection and response (EDR) system by eradicating course of creation callbacks – a mechanism that was detailed by a safety researcher who goes by the alias brsn in August 2020.
It is value noting the outdated model of the RTCore64.sys driver, which nonetheless has a sound digital signature, has been put to make use of by a number of menace actors like BlackByte and OldGremlin over the previous few months.
“[Earth Longzhi’s] goal sectors are in industries pertinent to Asia-Pacific international locations’ nationwide safety and economies,” the researchers stated. “The actions in these campaigns present that the group is educated on crimson group operations.”
“The group makes use of social engineering methods to unfold its malware and deploy personalized hack instruments to bypass the safety of safety merchandise and steal delicate knowledge from compromised machines.”