Fb enterprise and promoting accounts are on the receiving finish of an ongoing marketing campaign dubbed Ducktail designed to grab management as a part of a financially pushed cybercriminal operation.
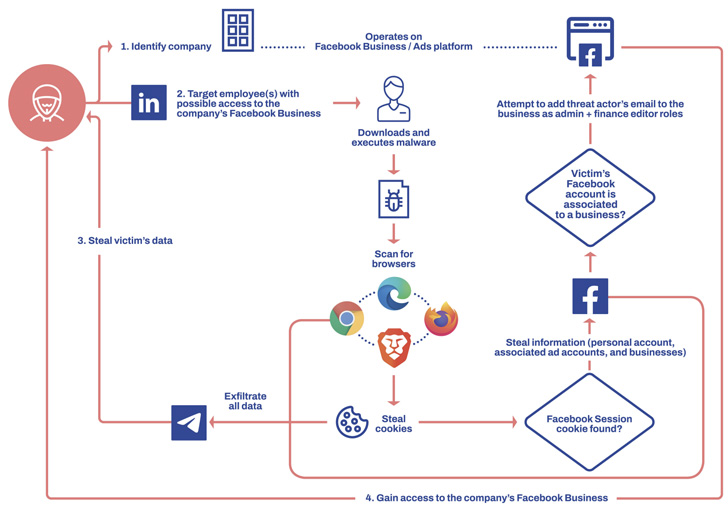
“The risk actor targets people and workers that will have entry to a Fb Enterprise account with an information-stealer malware,” Finnish cybersecurity firm WithSecure (previously F-Safe Enterprise) mentioned in a brand new report.
“The malware is designed to steal browser cookies and make the most of authenticated Fb classes to steal info from the sufferer’s Fb account and finally hijack any Fb Enterprise account that the sufferer has adequate entry to.”
The assaults, attributed to a Vietnamese risk actor, are mentioned to have begun within the latter half of 2021, with main targets being people with managerial, digital advertising, digital media, and human assets roles in firms.
The concept is to focus on workers with high-level entry to Fb Enterprise accounts related to their organizations, tricking them into downloading supposed Fb promoting info hosted on Dropbox, Apple iCloud, and MediaFire.
In some circumstances, the archive file containing the malicious payload can be delivered to victims by LinkedIn, finally permitting the attacker to take over any Fb Enterprise account.
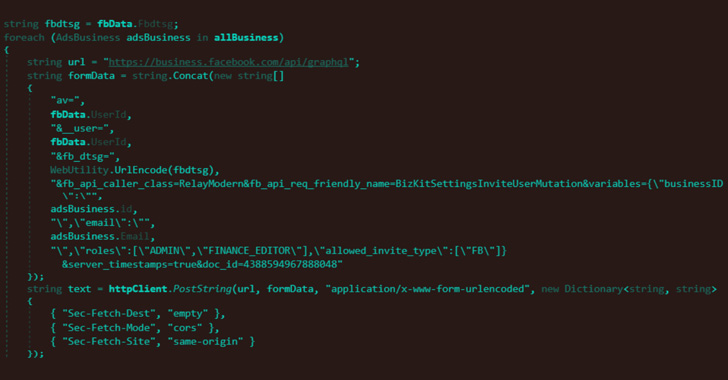
An information-stealing malware written in .NET Core, the binary is engineered to make use of Telegram for command-and-control and knowledge exfiltration. WithSecure mentioned it recognized eight Telegram channels that have been used for this function.
It really works by scanning for put in browsers reminiscent of Google Chrome, Microsoft Edge, Courageous Browser, and Mozilla Firefox to extract all of the saved cookies and entry tokens, alongside stealing info from the sufferer’s private Fb account reminiscent of title, electronic mail deal with, date of delivery, and person ID.
Additionally plundered are knowledge from companies and advert accounts related to the sufferer’s private account, permitting the adversary to hijack the accounts by including an actor-controlled electronic mail deal with retrieved from the Telegram channel and grant themselves Admin and Finance editor entry.
Whereas customers with Admin roles have full management over the Fb Enterprise account, customers with Finance editor permissions can edit enterprise bank card info and monetary particulars like transactions, invoices, account spend, and fee strategies.
Telemetry knowledge gathered by WithSecure reveals a world focusing on sample spanning numerous nations, together with the Philippines, India, Saudi Arabia, Italy, Germany, Sweden, and Finland.
That mentioned, the corporate famous it was “unable to find out the success, or lack thereof” of the Ducktail marketing campaign, including it could not decide what number of customers have doubtlessly been affected.
Fb Enterprise directors are suggested to evaluation their entry permissions and take away any unknown customers to safe the accounts.
The findings are one more indicator of how dangerous actors are more and more banking on reliable messaging apps like Discord and Telegram, abusing their automation options to propagate malware or meet their operational targets.
“Primarily used along with info stealers, cybercriminals have discovered methods to make use of these platforms to host, distribute, and execute varied features that finally permit them to steal credentials or different info from unsuspecting customers,” Intel 471 mentioned Tuesday.