Amid the ongoing warfare between Russia and Ukraine, authorities, agriculture, and transportation organizations situated in Donetsk, Lugansk, and Crimea have been attacked as a part of an lively marketing campaign that drops a beforehand unseen, modular framework dubbed CommonMagic.
“Though the preliminary vector of compromise is unclear, the main points of the following stage suggest the usage of spear phishing or related strategies,” Kaspersky stated in a brand new report.
The Russian cybersecurity firm, which detected the assaults in October 2022, is monitoring the exercise cluster underneath the title “Dangerous Magic.”
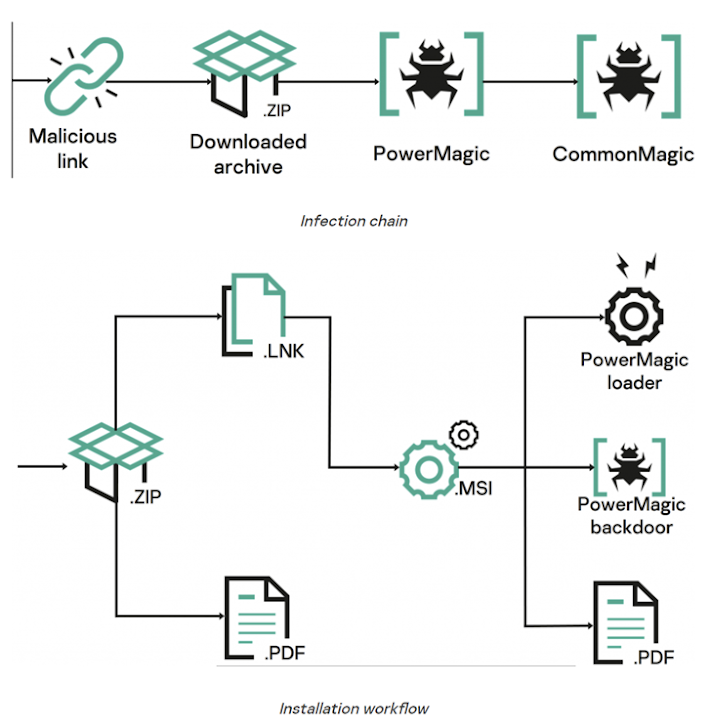
Assault chains entail the usage of booby-trapped URLS pointing to a ZIP archive hosted on a malicious net server. The file, when opened, accommodates a decoy doc and a malicious LNK file that culminates within the deployment of a backdoor named PowerMagic.
Written in PowerShell, PowerMagic establishes contact with a distant server and executes arbitrary instructions, the outcomes of that are exfiltrated to cloud companies like Dropbox and Microsoft OneDrive.
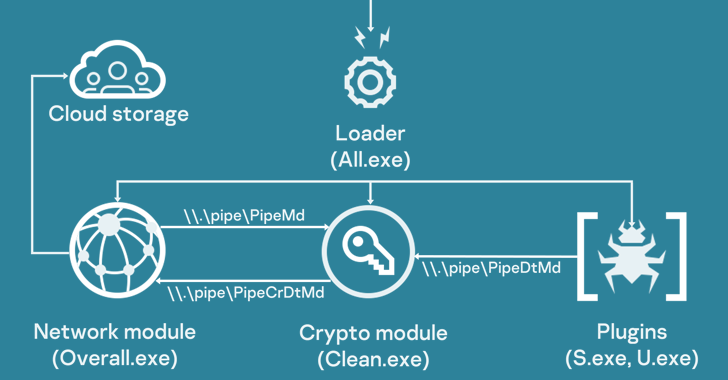
PowerMagic additionally serves as a conduit to ship the CommonMagic framework, a set of executable modules which might be designed to hold out particular duties reminiscent of interacting with the command-and-control (C2) server, encrypting and decrypting C2 visitors, and executing plugins.
Two of the plugins found up to now include capabilities to seize screenshots each three seconds and collect information of curiosity from linked USB units.
Kaspersky stated it discovered no proof linking the operation and its tooling to any recognized menace actor or group.