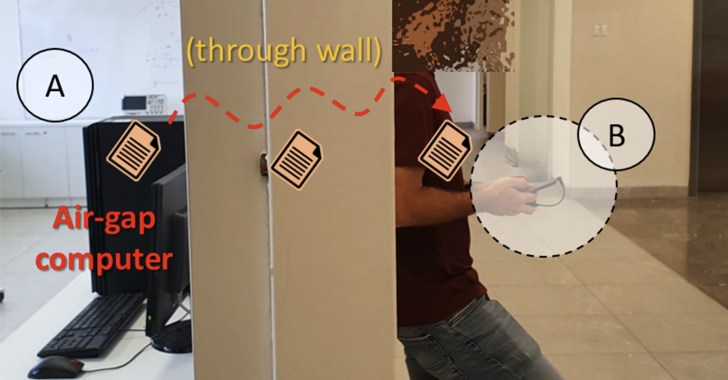
An unconventional knowledge exfiltration technique leverages a beforehand undocumented covert channel to leak delicate info from air-gapped programs.
“The knowledge emanates from the air-gapped laptop over the air to a distance of two m and extra and may be picked up by a close-by insider or spy with a cell phone or laptop computer,” Dr. Mordechai Guri, the top of R&D within the Cyber Safety Analysis Heart within the Ben Gurion College of the Negev in Israel and the top of Offensive-Defensive Cyber Analysis Lab, stated in a new paper shared with The Hacker Information.
The mechanism, dubbed COVID-bit, leverages malware planted on the machine to generate electromagnetic radiation within the 0-60 kHz frequency band that is subsequently transmitted and picked up by a stealthy receiving machine in shut bodily proximity.
This, in flip, is made attainable by exploiting the dynamic energy consumption of contemporary computer systems and manipulating the momentary hundreds on CPU cores.
COVID-bit is the newest method devised by Dr. Guri this yr, after SATAn, GAIROSCOPE, and ETHERLED, that are designed to leap over air-gaps and harvest confidential knowledge.
Air-gapped networks, regardless of their excessive stage of isolation, may be compromised by varied methods comparable to contaminated USB drives, provide chain assaults, and even rogue insiders.
Exfiltrating the info after breaching the community, nevertheless, is a problem because of the lack of web connectivity, necessitating that attackers concoct particular strategies to ship the data.
The COVID-bit is one such covert channel that is utilized by the malware to transmit info by profiting from the electromagnetic emissions from a element referred to as switched-mode energy provide (SMPS) and utilizing a mechanism referred to as frequency-shift keying (FSK) to encode the binary knowledge.
“By regulating the workload of the CPU, it’s attainable to control its energy consumption and therefore management the momentary switching frequency of the SMPS,” Dr. Guri explains.
“The electromagnetic radiation generated by this intentional course of may be obtained from a distance utilizing acceptable antennas” that value as little as $1 and may be related to a telephone’s 3.5 mm audio jack to seize the low-frequency indicators at a bandwidth of 1,000 bps.
The emanations are then demodulated to extract the info. The assault can be evasive in that the malicious code does not require elevated privileges and may be executed from inside a digital machine.
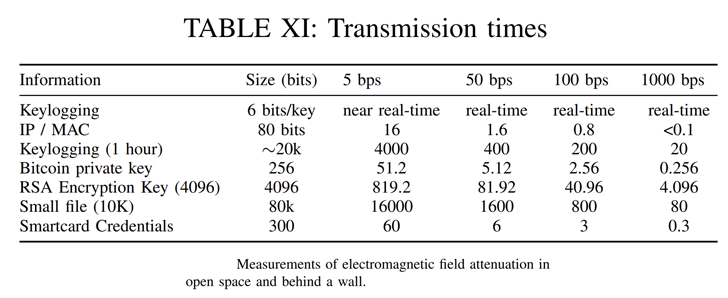
An analysis of the info transmissions reveals that keystrokes may be exfiltrated in close to real-time, with IP and MAC addresses taking anyplace between lower than 0.1 seconds to 16 seconds, relying on the bitrate.
Countermeasures towards the proposed covert channel embrace finishing up dynamic opcode evaluation to flag threats, provoke random workloads on the CPU processors when anomalous exercise is detected, and monitoring or jamming indicators within the 0-60 kHz spectrum.