Telecommunications and IT service suppliers within the Center East and Asia are being focused by a beforehand undocumented Chinese language-speaking menace group dubbed WIP19.
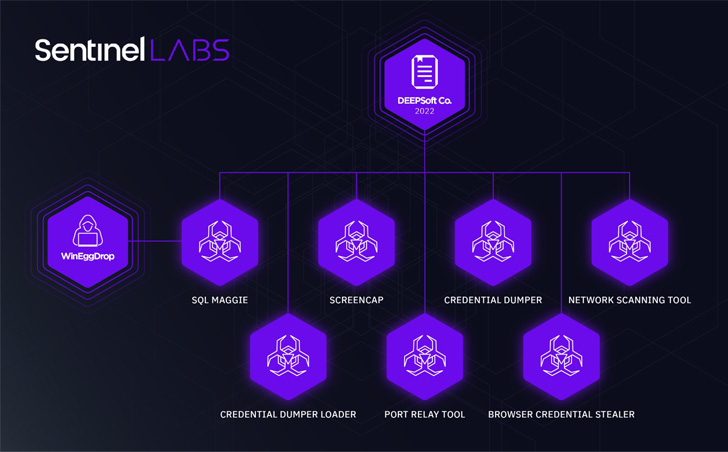
The espionage-related assaults are characterised by way of a stolen digital certificates issued by a Korean firm known as DEEPSoft to signal malicious artifacts deployed throughout the an infection chain to evade detection.
“Nearly all operations carried out by the menace actor have been accomplished in a ‘hands-on keyboard’ vogue, throughout an interactive session with compromised machines,” SentinelOne researchers Joey Chen and Amitai Ben Shushan Ehrlich mentioned in a report this week.
“This meant the attacker gave up on a steady [command-and-control] channel in alternate for stealth.”
WIP, quick for work-in-progress, is the moniker assigned by SentinelOne to rising or hitherto unattributed exercise clusters, related to the UNC####, DEV-####, and TAG-## designations given by Mandiant, Microsoft, and Recorded Future.
The cybersecurity agency additionally famous that choose parts of the malicious elements employed by WIP19 have been authored by a Chinese language-speaking malware writer dubbed WinEggDrop, who has been lively since 2014.
WIP19 is alleged to share hyperlinks to a different group codenamed Operation Shadow Power owing to overlaps in the usage of WinEggDrop-authored malware, stolen certificates, and tactical overlaps.
That mentioned, SentinelOne famous, “it’s unclear whether or not it is a new iteration of operation ‘Shadow Power’ or just a special actor using related TTPs.”
Intrusions mounted by the adversarial collective depend on a bespoke toolset that features a mixture of a credential dumper, community scanner, browser stealer, keystroke logger and display recorder (ScreenCap), and an implant often known as SQLMaggie.
SQLMaggie was additionally the topic of an in-depth evaluation by German cybersecurity firm DCSO CyTec earlier this month, calling out its means to interrupt into Microsoft SQL servers and leverage the entry to run arbitrary instructions by way of SQL queries.
An evaluation of telemetry knowledge additional revealed the presence of SQLMaggie in 285 servers unfold throughout 42 international locations, mainly South Korea, India, Vietnam, China, Taiwan, Russia, Thailand, Germany, Iran, and the U.S.
The truth that the assaults are precision focused and low in quantity, to not point out have singled out the telecom sector, signifies that the first motive behind the marketing campaign could also be to collect intelligence.
The findings are one more indication of how China-aligned hacking teams are without delay sprawling and fluid owing to the reuse of the malware amongst a number of menace actors.
“WIP19 is an instance of the better breadth of Chinese language espionage exercise skilled in essential infrastructure industries,” SentineOne researchers mentioned.
“The existence of dependable quartermasters and customary builders allows a panorama of hard-to-identify menace teams which can be utilizing related tooling, making menace clusters tough to differentiate from the defenders standpoint.”