A gaggle of teachers from the New Jersey Institute of Expertise (NJIT) has warned of a novel approach that may very well be used to defeat anonymity protections and establish a singular web site customer.
“An attacker who has full or partial management over an internet site can study whether or not a selected goal (i.e., a singular particular person) is searching the web site,” the researchers stated. “The attacker is aware of this goal solely by way of a public identifier, resembling an electronic mail tackle or a Twitter deal with.”
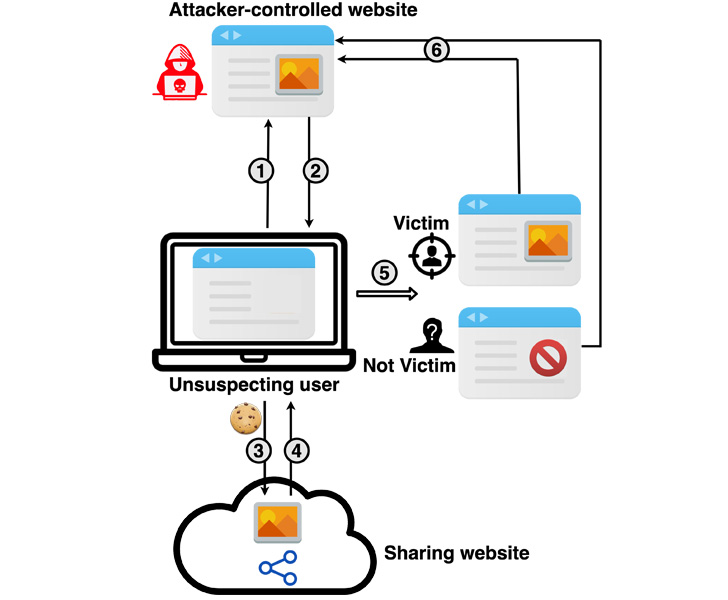
The cache-based focused de-anonymization assault is a cross-site leak that includes the adversary leveraging a service resembling Google Drive, Dropbox, or YouTube to privately share a useful resource (e.g., picture, video, or a YouTube playlist) with the goal, adopted by embedding the shared useful resource into the assault web site.
This may be achieved by, say, privately sharing the useful resource with the goal utilizing the sufferer’s electronic mail tackle or the suitable username related to the service after which inserting the leaky useful resource utilizing an <iframe> HTML tag.
Within the subsequent step, the attacker tips the sufferer into visiting the malicious web site and clicking on the aforementioned content material, inflicting the shared useful resource to be loaded as a pop-under window (versus a pop-up) or a browser tab — a way that is been utilized by advertisers to sneakily load advertisements.
This exploit web page, because it’s rendered by the goal’s browser, is used to find out if the customer can entry the shared useful resource, profitable entry indicating that the customer is certainly the meant goal.
The assault, in a nutshell, goals to unmask the customers of an internet site below the attacker’s management by connecting the checklist of accounts tied to these people with their social media accounts or electronic mail addresses by way of a bit of shared content material.
In a hypothetical situation, a foul actor may share a video hosted on Google Drive with a goal’s electronic mail tackle, and observe it up by inserting this video within the lure web site. Thus when guests land on the portal, a profitable loading of the video may very well be used as a yardstick to deduce if their sufferer is one amongst them.
The assaults, that are sensible to use throughout desktop and cellular techniques with a number of CPU microarchitectures and totally different net browsers, are made doable via a cache-based facet channel that is used to glean if the shared useful resource has been loaded and subsequently distinguish between focused and non-targeted customers.
Put in a different way, the thought is to look at the refined timing variations that come up when the shared useful resource is being accessed by the 2 units of customers, which, in flip, happens resulting from variations within the time it takes to return an applicable response from the online server relying on the consumer’s authorization standing.
The assaults additionally keep in mind a second set of variations on the client-side that occurs when the online browser renders the related content material or error web page primarily based on the response obtained.
“There are two foremost causes for variations within the noticed facet channel leakages between focused and non-targeted customers – a server-side timing distinction and a client-side rendering distinction,” the researchers stated.
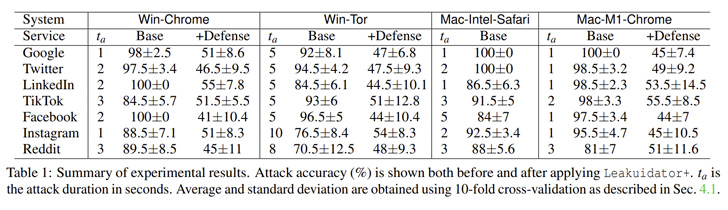
Whereas hottest platforms resembling these from Google, Fb, Instagram, LinkedIn, Twitter, and TikTok have been discovered prone, one notable service that is proof against the assault is Apple iCloud.
It is price stating the de-anonymization methodology banks on the prerequisite that the focused consumer is already logged in to the service. As mitigations, the researchers have launched a browser extension known as Leakuidator+ that is out there for Chrome, Firefox, and Tor browsers.
To counter the timing and rendering facet channels, web site house owners are really useful to design net servers to return their responses in fixed time, regardless of whether or not the consumer is provisioned to entry the shared useful resource, and make their error pages as related as doable to the content material pages to attenuate the attacker-observable variations.
“For instance, if a certified consumer was going to be proven a video, the error web page for the non-targeted consumer must also be made to indicate a video,” the researchers stated, including web sites must also be made to require consumer interplay earlier than rendering content material.
“Realizing the exact id of the one who is at the moment visiting an internet site may be the start line for a spread of nefarious focused actions that may be executed by the operator of that web site.”
The findings arrive weeks after researchers from the College of Hamburg, Germany, demonstrated that cellular units leak figuring out info resembling passwords and previous vacation areas through Wi-Fi probe requests.
In a associated improvement, MIT researchers final month revealed the foundation trigger behind a web site fingerprinting assault as not resulting from indicators generated by cache competition (aka a cache-based facet channel) however reasonably resulting from system interrupts, whereas exhibiting that interrupt-based facet channels can be utilized to mount a robust web site fingerprinting assault.