A Rust variant of a ransomware pressure generally known as Agenda has been noticed within the wild, making it the newest malware to undertake the cross-platform programming language after BlackCat, Hive, Luna, and RansomExx.
Agenda, attributed to an operator named Qilin, is a ransomware-as-a-service (RaaS) group that has been linked to a spate of assaults primarily concentrating on manufacturing and IT industries throughout completely different international locations.
A earlier model of the ransomware, written in Go and customised for every sufferer, singled out healthcare and schooling sectors in international locations like Indonesia, Saudi Arabia, South Africa, and Thailand.
Agenda, like Royal ransomware, expands on the concept of partial encryption (aka intermittent encryption) by configuring parameters which might be used to find out the share of file content material to be encrypted.
“This tactic is gaining popularity amongst ransomware actors because it lets them encrypt quicker and keep away from detections that closely depend on learn/write file operations,” a bunch of researchers from Pattern Micro mentioned in a report final week.
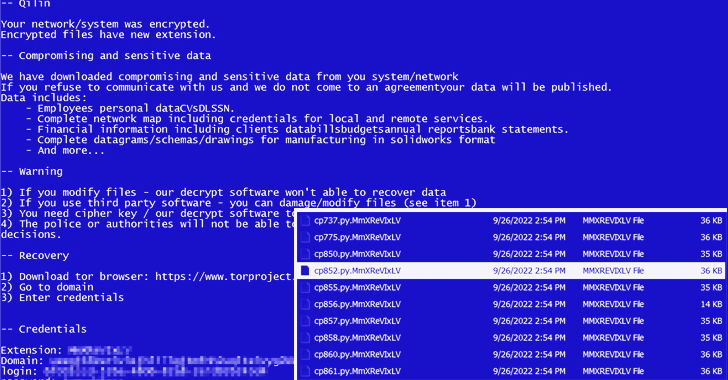
An evaluation of the ransomware binary reveals that encrypted information are given the extension “MmXReVIxLV,” earlier than continuing to drop the ransom observe in each listing.
As well as, the Rust model of Agenda is able to terminating the Home windows AppInfo course of and disabling Consumer Account Management (UAC), the latter of which helps mitigate the impression of malware by requiring administrative entry to launch a program or activity.
“At current, its menace actors look like migrating their ransomware code to Rust as current samples nonetheless lack some options seen within the unique binaries written within the Golang variant of the ransomware,” the researchers famous.
“Rust language is gaining popularity amongst menace actors as it’s tougher to investigate and has a decrease detection fee by antivirus engines.”