In October 2022 I described how you could possibly construct a VLAN router-on-a-stick topology with netlab. With the brand new options added in netlab launch 1.4 we are able to do the identical for VXLAN-enabled VLANs – we’ll construct a lab the place a router-on-a-stick will do VXLAN-to-VXLAN routing.
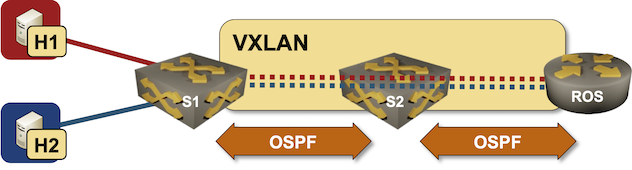
Lab topology
- S1 is a VXLAN-enabled layer-2 change (no IP addresses on crimson or blue VLANs).
- VXLAN is enabled on S2, nevertheless it has no VLANs – it’s a pure IP transport gadget.
- ROS has two VXLAN-enabled VLANs. It has IP addresses on VLAN interfaces, so it may possibly route between the 2 VLANs, leading to connectivity between H1 and H2.
Our lab topology will likely be similar to the VLAN router-on-a-stick topology.
We have now to outline the 2 VLANs and a VRF:
vrfs:
tenant:
vlans:
crimson:
vrf: tenant
blue:
vrf: tenant
We’ll use netlab teams to outline many of the node parameters. Layer-2 switches want VLAN, VXLAN, and OSPF modules. They need to not do any IP forwarding on the VLANs – vlan.mode needs to be set to bridge.
teams:
switches:
members: [ s1, s2 ]
module: [ vlan,vxlan,ospf ]
vlan.mode: bridge
The router wants all of the modules utilized by the layer-2 switches, and the VRF module. It additionally wants IP tackle on VLAN interfaces, so we’ll set vlan.mode to irb:
teams:
routers:
members: [ ros ]
module: [ vlan,vxlan,ospf,vrf ]
vlan.mode: irb
We would like the router to route between VXLAN-enabled VLAN interfaces, so we MUST set the vlan.mode to irb. Setting vlan.mode to route wouldn’t create the VLAN interfaces.
Lastly, we’d like a couple of hosts, the checklist of nodes, and the checklist of hyperlinks:
teams:
hosts:
members: [ h1, h2 ]
gadget: linux
nodes: [ h1, h2, s1, s2, ros ]
hyperlinks:
- h1:
s1:
vlan.entry: crimson
- h2:
s1:
vlan.entry: blue
- s1-s2
- s2-ros
Sadly, the above lab topology wouldn’t work:
- ROS (like S2) has no want for crimson or blue VLANs, so they aren’t added to the node knowledge
- As a result of there’s no crimson or blue VLAN in ROS node knowledge, the VLAN interfaces are usually not created on ROS.
- No VLAN interfaces ==> no routing.
One way or the other we have now to verify the crimson and the blue VLAN are outlined on ROS. We may add them to node knowledge or to the routers group. I made a decision to make use of the latter strategy; you could find the ultimate topology file within the netlab-examples GitHub repository.
teams:
routers:
members: [ ros ]
module: [ vlan,vxlan,ospf,vrf ]
vlans:
crimson:
blue:
Now we’re able to roll. Execute netlab up and begin exploring. Wish to use another gadget as a substitute of Arista cEOS? Add -d gadget to netlab up command, for instance netlab up -d cumulus.
Haven’t put in netlab but? Properly, it is best to; within the meantime, right here’s the Arista cEOS configuration for the VXLAN router-on-a-stick:
Arista cEOS VXLAN router-on-a-stick configuration
vlan 1000
title crimson
!
vlan 1001
title blue
!
vrf occasion tenant
rd 65000:1
!
administration api http-commands
no shutdown
!
administration api gnmi
transport grpc default
!
administration api netconf
transport ssh default
!
interface Ethernet1
description ros -> s2
mac-address 52:dc:ca:fe:05:01
no switchport
ip tackle 10.1.0.5/30
ip ospf community point-to-point
ip ospf space 0.0.0.0
!
interface Loopback0
ip tackle 10.0.0.5/32
ip ospf space 0.0.0.0
!
interface Management0
ip tackle 192.168.121.105/24
no lldp transmit
no lldp obtain
!
interface Vlan1000
description VLAN crimson (1000) -> [h1,s1]
vrf tenant
ip tackle 172.16.0.5/24
ip ospf space 0.0.0.0
!
interface Vlan1001
description VLAN blue (1001) -> [h2,s1]
vrf tenant
ip tackle 172.16.1.5/24
ip ospf space 0.0.0.0
!
interface Vxlan1
vxlan source-interface Loopback0
vxlan udp-port 4789
vxlan vlan 1000 vni 101000
vxlan vlan 1001 vni 101001
vxlan vlan 1000 flood vtep 10.0.0.3
vxlan vlan 1001 flood vtep 10.0.0.3
!
ip routing
ip routing vrf tenant
!
router ospf 1
router-id 10.0.0.5
max-lsa 12000
!
router ospf 100 vrf tenant
router-id 10.0.0.5
interface unnumbered hey masks tx 0.0.0.0
max-lsa 12000
Wish to run this lab by yourself, or attempt it out with completely different gadgets? No downside:

