ACM.101 Configuring community and host firewalls on residence and enterprise networks to permit SSH to an AWS IP tackle
This can be a continuation of my sequence on Automating Cybersecurity Metrics.
Within the final publish, we deployed an EC2 occasion configured with an EIP on AWS.
In case you’ve carried out that, now you may also prohibit SSH out of your native community to your EIP on AWS and disallow connections to unauthorized IP addresses and disallow unauthorized hosts in your native community from utilizing SSH. I’m going to exhibit this with PFSense however no matter community firewall you utilize ought to have related choices.
You’ll be able to set up the free open supply PFSense software program by yourself {hardware} or purchase a pre-installed equipment from Netgate. Among the Netgate home equipment have completely different options you should use corresponding to a number of ports which you can configure with completely different community guidelines and VLANS.
In my case, I take advantage of completely different ports on the firewall for various functions. I’m going to permit the port related to the community I take advantage of for improvement to entry the EIP I simply created on port 22.
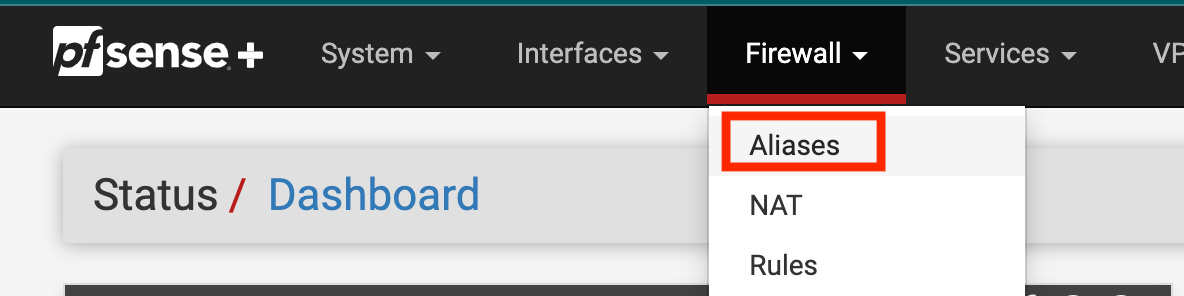
Create an Alias
Step one I’ll do is create an alias. I can create an alias that factors to different issues in my community configuration like IP addresses, networks, and domains. On this case I’m going to create an alias for a gaggle of IP addresses that units on my developer community can entry through SSH.
On the backside of the record of Aliases click on Add.
Copy the EIP within the AWS console.
Add the alias with the suitable info:
Create a Firewall Rule
Subsequent I’m going to create a rule to my WAN interface enable entry for SSH to these IP addresses.
You will note a listing of interfaces in your firewall on the high:
Interfaces
If you wish to see what these interfaces are mapped to click on Interfaces > Assignments. They might be assigned to the ports in your {hardware} or VLANS relying on how your firewall is configured.
For instance, your firewall could have a WAN interface (uncovered to the Web) a LAN interface (your personal community) and one other interface (presumably referred to as OPT) that you should use for firewall administration. You might also configure your firewall to have separate VLANs so you may segregate your Web of Insecure Issues and visitor community (or insecure roommate) community out of your improvement community.
In my case, I’ve a WAN interface and I’ll must specify that visitors from my improvement interface or VLAN can ship visitors on port 22 to the Web. I’ll additionally want to permit that rule on my improvement interface.
PFSense additionally has one thing name “Floating” which may apply to all of your Interfaces. Watch out with that one — particularly if you’re utilizing VLANs. A misconfiguration can enable an attacker to bypass VLAN controls. Nevertheless it ought to be fantastic for blocking visitors throughout all interfaces.
Create a rule for SSH from LAN community to EIP Alias on WAN Interface
Click on on the WAN interface. Click on ^ Add (with the up arrow) so as to add a rule.
Be sure you don’t click on the Add button with the down arrow. There’s a default rule that blocks all visitors — ensure you don’t delete it! That rule applies in any case the foundations that enable visitors. In case you delete it you’ve primarily enable something and also you wasted cash in your firewall.
Depart the highest because the default.
Observe that I don't use IPv6 not as a result of I can’t or it’s insecure however as a result of it’s simply extra complexity than I would like. I'm not working out of IP addresses and that may be the one motive to make use of IPv6 on an area community. It may be misconfigured and attackers do use it in assaults as a result of folks configure networks with IPv6 and don’t know what they're doing.I simply noticed a publish on LinkedIn the place the one approach a penetration tester was in a position to get right into a consumer’s community was by means of an IPv6 misconfiguration. In case you don’t want and and haven’t researched all doable assaults in nice element, you might be most likely simply making a safety threat relatively than including any worth to your community by enabling it.Some distributors have began requiring it to be enabled on working programs however issues ought to nonetheless work simply fantastic with out it. Additionally notice that my steering will change if the day comes the place IPv4 has some huge safety flaw and or is now not possible. In that case, I'd suggest solely utilizing IPv6 and switch off IPv4 to scale back the complexity of what you have to handle.
SSH makes use of the TCP protocol. Don’t add protocols you don’t want. As you may see we’re permitting this visitors on the WAN interface.
Scroll down. Select a supply. For the supply you may enable a singe IP tackle in your native community, or visitors from one in all your community interfaces amongst different choices. Let’s say you wished any host in your LAN (native space community) interface to have the ability to attain your EIP. Select LAN internet.
Develop superior. Our supply IP will probably be connecting TO port 22. The return visitors to the supply host will probably be ephemeral ports as I defined in a previous publish. Permit visitors again to the supply on ephemeral ports.
For the vacation spot, select single host or alias.
Begin typing the identify of your alias after which you may choose it.
For the vacation spot port vary we will select SSH from a listing.
While you select SSH PFSense populates the ports for you.
You might additionally select (different) and enter 22 your self.
Ensure to allow logging. Enter an outline that can present up within the logs. You’ll most likely wish to add -WAN to the tip of the outline so you recognize the visitors is coming from the WAN interface while you have a look at your logs.
Click on on superior to see among the different choices.
That is the place we’re entering into among the particulars within the packet headers and protocols I’ve been telling you about in different posts. For instance, we may get granular about which TCP protocol flags to permit if we wished. We’re not going to do this right here.
Click on Save:
Click on Apply Adjustments:
Create a rule for SSH from LAN community to EIP Alias on LAN Interface
Now click on the 2 packing containers on the proper to repeat the WAN interface rule so we will copy it to the LAN interface.
Now within the copied rule change the interface to the personal interface from which you may be initiating the visitors (corresponding to LAN in case your community cable out of your WiFi system or your laptop computer is plugged into that port.) Change the log description to say -LAN as a substitute of -WAN.
Save and apply the copied rule.
Now make certain your EC2 occasion is began and check out to connect with it utilizing the strategies in our prior publish.
In case you are solely utilizing a network-based firewall and never utilizing a host-based firewall, that ought to work. Ensure your EC2 occasion is began and you might be utilizing the AWS networking we deployed in prior posts that enable your particular IP tackle to connect with your developer VM.
View your firewall logs
By the way in which, if you wish to see all of the visitors scanning your community from the minute you join your router or firewall too it, examine the logs. On PFSense click on the field with traces highlighted under in your WAN interface.
In my case, I’ve weeded out a variety of noise so I can’t actually present you all of the rogue visitors until I am going change my firewall logs however by default you will note visitors from all over scanning your community and in search of safety vulnerabilities.
Even firewalls have vulnerabilities at instances. Seek for the identify of your firewall or mode in Google together with “vulnerability” or “breach” or “malware” to see if you will discover examples the place attackers have damaged into the actual kind of system you personal. Ensure your firewalls and routers are stored updated with the most recent firmware and software program patches.
Host-Primarily based Firewalls
I’m additionally utilizing a host-based firewall on my Mac referred to as Little Snitch. It pops up and alerts me when something connects so I can enable or deny it. (You’ll be able to configure it to not show ever alert. I’m only a community geek and prefer to see all my connections and particularly new ones.)
In case you’re utilizing Linux you should use the IPTables firewall.
Home windows has its personal firewall constructed into the working system.
Apparently Chromebooks have a firewall as nicely.
Why do I take advantage of a host-based firewall and a network-based firewall? Let’s say some malware will get onto my native machine and is ready to bypass and even flip off my native firewall. Then my community firewall could catch it.
Alternatively if my community primarily based firewall is misconfigured or compromised, hopefully my localhost firewall will catch it. I even wrote about how you possibly can use a number of firewalls with completely different capabilities and for extra visitors inspection to ensure every system is correctly doing its job on this publish: Watching the Community Watchers.
The primary time I hook up with this IP I get a warning. I can select to permit it as soon as, on a regular basis, or till I logout or restart.
As soon as I enable the visitors, I can hook up with my EC2 occasion related to that IP tackle.
Success. Subsequent I’ll present you how one can prohibit entry to GitHub out of your AWS EC2 occasion with the related EIP.
Comply with for updates.
Teri Radichel
In case you preferred this story please clap and observe:
Medium: Teri Radichel or Electronic mail Record: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests companies through LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2022
All of the posts on this sequence:
____________________________________________
Writer:
Cybersecurity for Executives within the Age of Cloud on Amazon
Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration check or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Assets by Teri Radichel: Cybersecurity and Cloud safety lessons, articles, white papers, displays, and podcasts