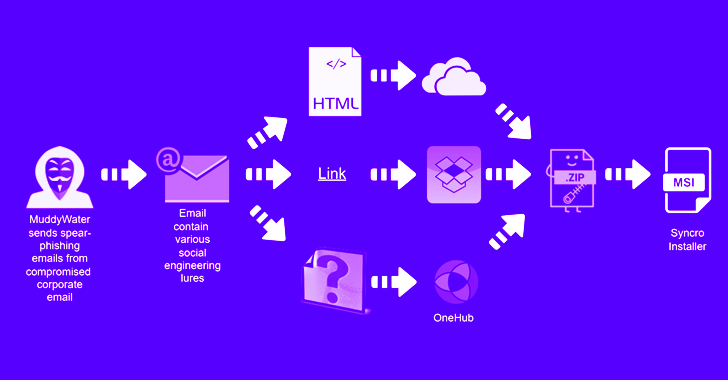
The Iran-linked MuddyWater risk actor has been noticed focusing on a number of nations within the Center East in addition to Central and West Asia as a part of a brand new spear-phishing exercise.
“The marketing campaign has been noticed focusing on Armenia, Azerbaijan, Egypt, Iraq, Israel, Jordan, Oman, Qatar, Tajikistan, and the United Arab Emirates,” Deep Intuition researcher Simon Kenin stated in a technical write-up.
MuddyWater, additionally known as Boggy Serpens, Cobalt Ulster, Earth Vetala, Mercury, Seedworm, Static Kitten, and TEMP.Zagros, is claimed to be a subordinate ingredient inside Iran’s Ministry of Intelligence and Safety (MOIS).
Energetic since at the very least 2017, assaults mounted by the espionage group have usually focused telecommunications, authorities, protection, and oil sectors.
The present intrusion set follows MuddyWater’s long-running modus operandi of utilizing phishing lures that include direct Dropbox hyperlinks or doc attachments with an embedded URL pointing to a ZIP archive file.
It is price mentioning right here that the messages are despatched from already compromised company e mail accounts, that are being provided on the market on the darknet by webmail retailers like Xleet, Odin, Xmina, and Lufix wherever between $8 to $25 per account.
Whereas the archive recordsdata have beforehand harbored installers for legit instruments like ScreenConnect and RemoteUtilities, the actor was noticed switching to Atera Agent in July 2022 in a bid to fly beneath the radar.
However in an extra signal that the marketing campaign is being actively maintained and up to date, the assault ways have been tweaked but once more to ship a special distant administration instrument named Syncro.
The built-in MSP software program affords a option to utterly management a machine, permitting the adversary to conduct reconnaissance, deploy extra backdoors, and even promote entry to different actors.
“A risk actor that has entry to a company machine through such capabilities has practically limitless choices,” Kenin famous.
The findings come as Deep Intuition additionally uncovered new malware parts employed by a Lebanon-based group tracked as Polonium in its assaults aimed completely at Israeli entities.
“Polonium is coordinating its operations with a number of tracked actor teams affiliated with Iran’s Ministry of Intelligence and Safety (MOIS), based mostly on sufferer overlap and the next frequent methods and tooling,” Microsoft famous in June 2022.