Through the growth of JFrog Xray’s Secrets and techniques Detection, we examined its capabilities by scanning greater than eight million artifacts in well-liked open-source bundle registries. Equally, for JFrog Xray’s new Container Contextual Evaluation characteristic, we once more examined our detection in a large-scale, real-world use case, each for eliminating bugs and for assessing the real-world viability of our present answer.
Nonetheless, not like the shocking outcomes we acquired in our Secrets and techniques Detection analysis (we found many extra energetic entry tokens than we bargained for), the outcomes of our scans of Docker Hub container photos had been according to what we had been seeing, as safety engineers, for a few years now.
Particularly, when the metric for a susceptible system is solely “bundle X is put in,” we count on most safety alerts to be false positives. And this was precisely the case for the CVEs we detected in container photos on Docker Hub.
On this publish we’ll element our analysis methodology and findings and provide some recommendation for builders and safety professionals seeking to scale back the quantity of CVE false positives.
Exploitable vs. ‘susceptible bundle is put in’
Earlier than diving in, let’s briefly have a look at some instance vulnerabilities to know circumstances the place a CVE report might be thought-about a false optimistic, even when a susceptible element exists.
This isn’t an exhaustive record by any means, nevertheless it does cowl probably the most outstanding causes of CVE false positives.
Library vulnerabilities
 JFrog
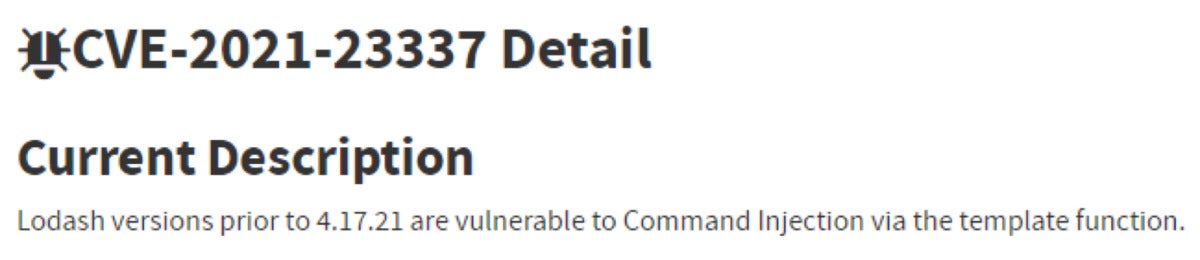
JFrogDoes the truth that a susceptible model of Lodash is put in assure a susceptible system?
No. By definition, we can’t decide whether or not a CVE in a library is exploitable just by noting that the library is put in. It is because a library isn’t a runnable entity; there have to be another code within the system that makes use of the library in a susceptible method.
Within the instance above, even when Lodash is put in, the system might not be susceptible. There have to be some code that calls the susceptible perform, on this case template(), from the susceptible Lodash library. Generally, there are even extra necessities, corresponding to that one of many arguments handed to template() can be attacker-controlled.
Different code-related stipulations might embrace:
- Whether or not a mitigating perform is known as earlier than the susceptible perform.
- Whether or not particular arguments of the susceptible perform are set to particular susceptible values.
Service configuration
 JFrog
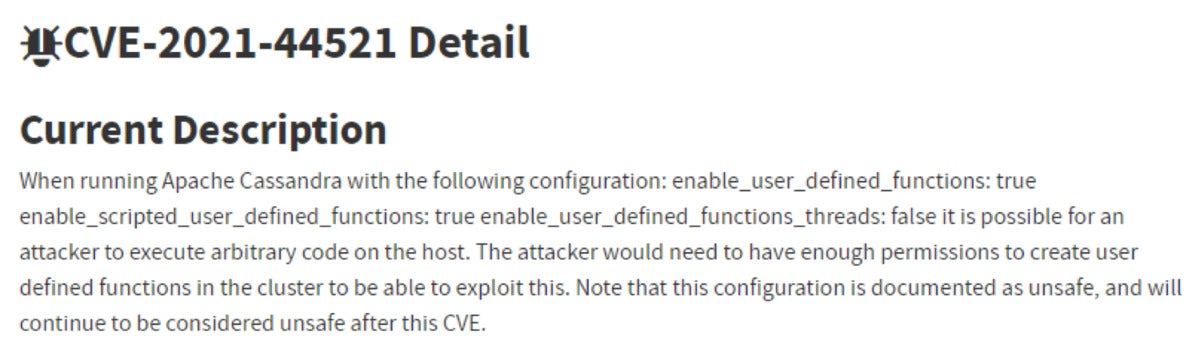
JFrogDoes the truth that a susceptible model of Cassandra is put in assure a susceptible system?
No. In most fashionable service vulnerabilities (particularly ones with extreme influence) the vulnerability solely manifests in non-default configurations of the service. It is because the default and sane configuration is commonly examined probably the most, both by the builders themselves or just by the real-world customers of the service.
Within the instance above, to attain distant code execution (RCE), the Cassandra service have to be configured with three non-default configuration flags (one in all them being fairly uncommon).
Different configuration-related stipulations might embrace:
- Whether or not the element is being run with particular command-line arguments or atmosphere variables.
- Whether or not the susceptible element was compiled with particular construct flags.
Operating atmosphere
 JFrog
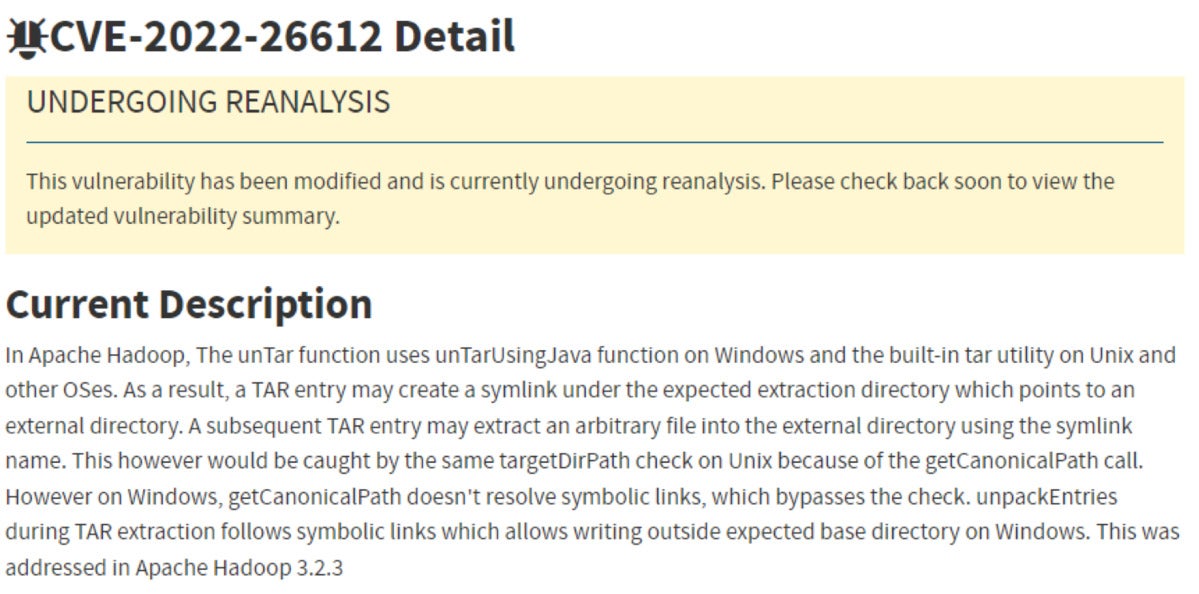
JFrogDoes the truth that a susceptible model of Apache Hadoop is put in assure a susceptible system?
No. Within the instance above, the vulnerability solely manifests in a Microsoft Home windows atmosphere. Due to this fact if the susceptible element is put in in a Linux atmosphere, it can’t be exploited.
Different environment-related stipulations might embrace:
- Whether or not the susceptible element is working in a particular distribution (e.g. Debian)
- Whether or not the susceptible element is compiled for a particular structure (e.g. 32-bit Arm).
- Whether or not a firewall blocks communication to the susceptible service.
Our analysis methodology
On this analysis, we got down to discover what share of vulnerability experiences really point out that the vulnerability is exploitable, when contemplating two reporting strategies:
- Naive. The vulnerability is reported each time a susceptible element is put in within the related (susceptible) model vary. That is how virtually all SCA instruments work right this moment.
- Context-sensitive. The vulnerability is barely reported (or stated to be relevant) if the context of the picture signifies susceptible utilization of the element. This takes under consideration components that had been mentioned within the earlier part (code stipulations, configuration stipulations, working atmosphere).
We’re focused on testing the above in frequent real-world environments, and performing this check on as many environments as doable.
 JFrog
JFrogWe realized that taking a look at Docker Hub’s high “group” photos ought to fulfill each requests, for 2 causes:
- These photos are used extraordinarily continuously. For instance, the highest 25 photos presently have greater than 1 billion downloads.
- Group photos often include each an fascinating element and the code that makes use of the element to some finish, which offers a sensible context. That is not like “official” Docker photos that often include standalone elements which are left unused and of their default configuration. For instance, an Nginx internet server by itself with default configuration would in all probability not be prone to any main CVE, nevertheless it doesn’t present a practical state of affairs.
Based mostly on these components, we arrived on the following methodology:
- Pull Docker Hub’s high 200 group photos, of their “newest” tag.
- Collect from these photos the highest 10 most “well-liked” CVEs (sorted by CVE incidence throughout all photos).
- Run our contextual evaluation on all 200 photos.
- Calculate the proportion of the naive methodology false optimistic price, by dividing “non-applicable occurrences” by “complete occurrences” for every of the highest 10 CVEs.
What had been the highest 10 CVEs?
And so we scanned Docker Hub’s high 200 group photos. The desk under lists the CVEs that appeared within the highest variety of photos.
|
CVE ID |
CVSS |
Brief description |
|
CVE-2022-37434 |
9.8 |
zlib by means of 1.2.12 has a heap-based buffer over-read or buffer overflow in inflate(). Solely purposes that decision inflateGetHeader are affected. |
|
CVE-2022-29458 |
7.1 |
ncurses 6.3 has an out-of-bounds learn and segmentation violation in convert_strings() |
|
CVE-2021-39537 |
8.8 |
ncurses by means of v6.2 nc_captoinfo() has a heap-based buffer overflow |
|
CVE-2022-30636 |
N/A |
Golang x/crypto/acme/autocert: httpTokenCacheKey permits restricted listing traversal on Home windows |
|
CVE-2022-27664 |
7.5 |
Golang web/http earlier than 1.18.6 DoS as a result of an HTTP/2 connection can hold |
|
CVE-2022-32189 |
7.5 |
Golang math/massive earlier than 1.17.13 Float.GobDecode and Rat.GobDecode DoS as a consequence of panic |
|
CVE-2022-28131 |
7.5 |
Golang encoding/xml earlier than 1.17.12 Decoder.Skip DoS as a consequence of stack exhaustion |
|
CVE-2022-30630 |
7.5 |
Golang io/fs earlier than 1.17.12 Glob DoS as a consequence of uncontrolled recursion |
|
CVE-2022-30631 |
7.5 |
Golang compress/gzip earlier than 1.17.12 Reader.Learn DoS as a consequence of uncontrolled recursion |
|
CVE-2022-30632 |
7.5 |
Golang path/filepath earlier than 1.17.12 Glob DoS as a consequence of stack exhaustion |
What number of CVEs had been really exploitable?
We intentionally selected to run the contextual scanners on their most conservative setting — extra on that within the subsequent part.
The contextual scanner for every CVE was outlined as described within the desk under.
|
CVE ID |
Contextual scanner |
|
CVE-2022-37434 |
Test for 1st-party code that calls “inflateGetHeader” and “inflate” |
|
CVE-2022-29458 |
Test for invocations of the ncurses “tic” CLI utility |
|
CVE-2021-39537 |
Test for invocations of the ncurses “cap2info” CLI utility |
|
CVE-2022-30636 |
Test for Home windows OS + 1st-party code that calls “autocert.NewListener” or references “autocert.DirCache” |
|
CVE-2022-27664 |
Test for 1st-party code that calls “ListenAndServeTLS” (HTTP/2 is barely accessible over TLS) |
|
CVE-2022-32189 |
Test for 1st-party code that calls “Rat.GobDecode” or “Float.GobDecode” |
|
CVE-2022-28131 |
Test for 1st-party code that calls “Decoder.Skip” |
|
CVE-2022-30630 |
Test for 1st-party code that calls “fs.Glob” with non-constant enter |
|
CVE-2022-30631 |
Test for 1st-party code that calls “gzip.Reader.Learn” |
|
CVE-2022-30632 |
Test for 1st-party code that calls “filepath.Glob” with non-constant enter |
–
Operating the contextual scanners on all 200 photos gave us the next outcomes, per CVE.
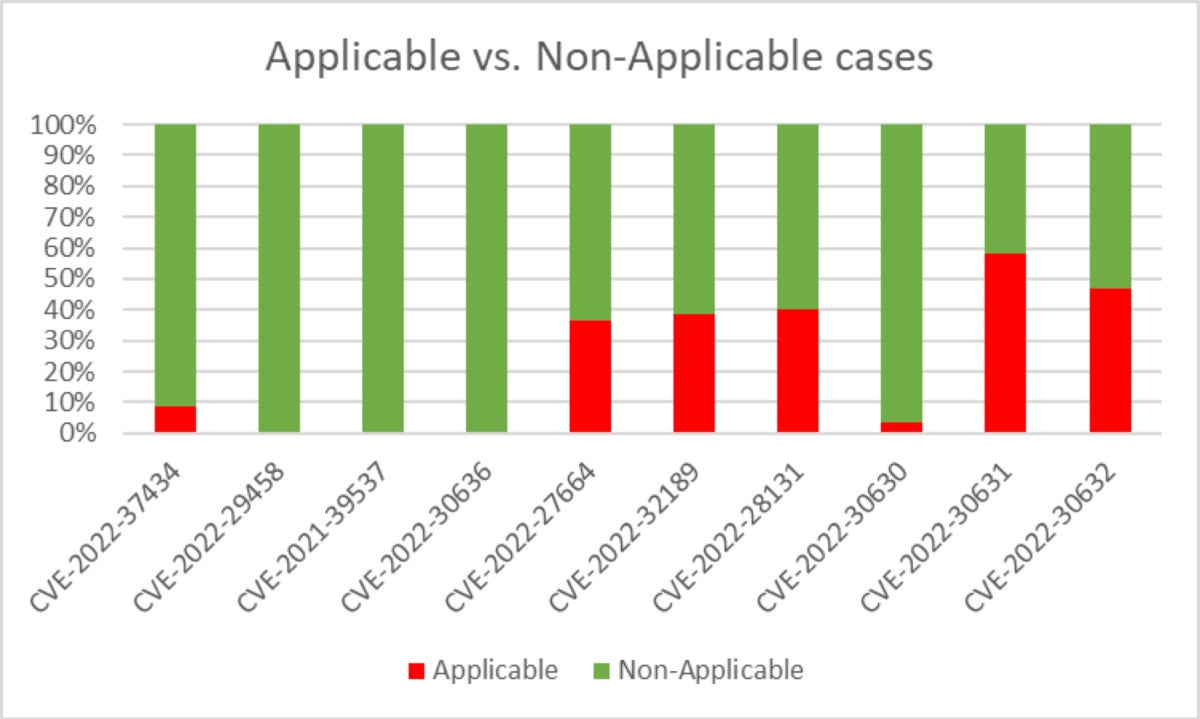 JFrog
JFrogAnd after we tallied the outcomes of all high 10 CVEs collectively, right here’s what we found:
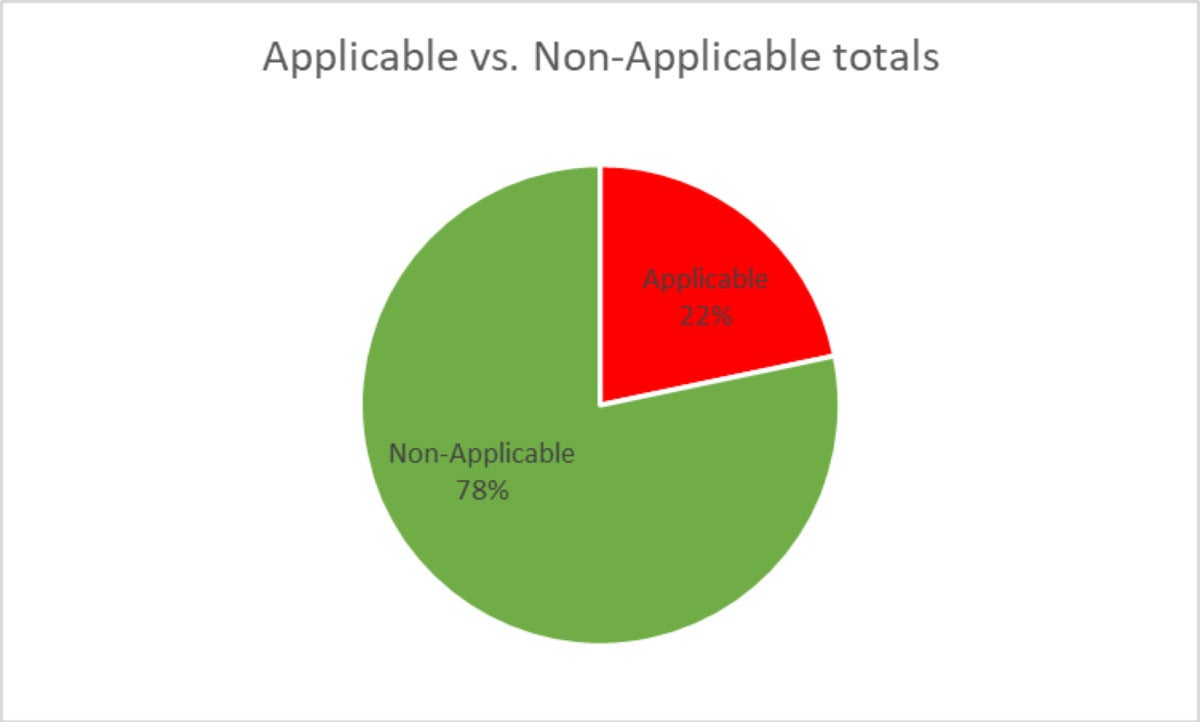 JFrog
JFrog78% of the CVE circumstances had been discovered to be non-applicable!
Trying on the present limits of contextual evaluation
Let’s study CVE-2022-30631, which had an exceptionally excessive applicability price.
CVE-2022-30631 was the one one which crossed 50% applicability. In layman’s phrases, the prerequisite for this CVE to be exploitable is “Golang is used to extract an attacker-controlled gzip archive.” In actuality, the scanner will alert if first-party Golang code tries to extract any gzip archive. It is because guaranteeing whether or not a file is attacker-controlled is a really laborious activity, as a result of multitude of doable sources affecting the file.
When attempting to find out whether or not a variable comes from fixed enter or exterior/attacker enter, this may be achieved for instance by way of information move evaluation. Knowledge move evaluation is carried out by a few of our scanners, detecting CVE-2022-30630, for instance, which had a a lot decrease applicability price.
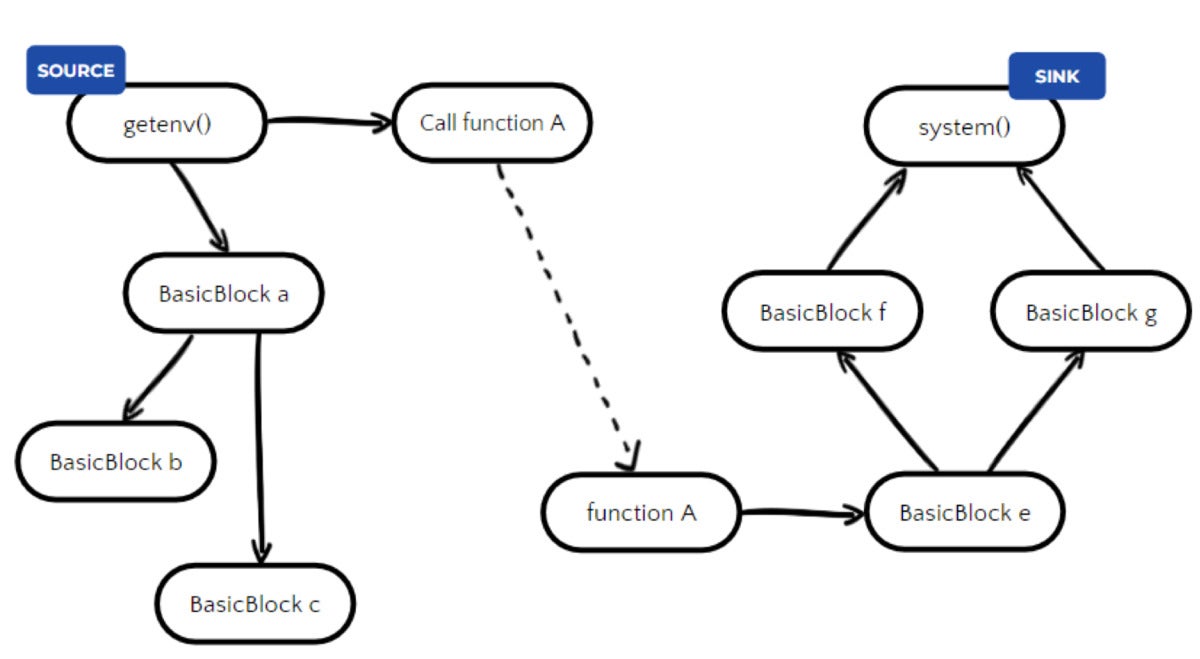 JFrog
JFrogHowever when coping with recordsdata, even when the perform’s file path argument is fixed, there is no such thing as a assure that the file isn’t attacker-controlled, and vice versa. Due to this fact, we count on the real-world applicability of this CVE to be even decrease.
Why 78% is definitely a conservative quantity
From the instance above, we are able to see that some CVEs might have an exaggerated applicability price, that means the real-world applicability could also be even decrease. You will need to talk about why (within the frequent case) it nonetheless is smart to run conservative scanners. There are two causes for this: first, as a result of we choose false positives to false detrimental, and second, due to efficiency concerns.
Choice in direction of false positives and never false negatives
Each know-how has its limitations, and that is doubly true when attempting to unravel computationally infeasible issues corresponding to “can a sure enter be managed by exterior sources.” In sure circumstances (the better ones), we are able to make sure assumptions that make the computation of the answer doable with extraordinarily excessive confidence.
Nonetheless, in different circumstances (the more durable one), the place 100% confidence isn’t assured, we should always do two issues:
- Choose scanners that have a tendency to indicate false positives (in our case, present outcomes as relevant when in actuality they aren’t). That is finished as a result of, on this case, the end result shall be examined by an engineer and evaluated whether or not it’s actually relevant or not. Within the reverse case, the place the vulnerability can be flagged as non-applicable, the engineer will assume it may be ignored, and thus the vulnerability can be left susceptible, which is a way more extreme state of affairs.
- Each time doable, present the boldness price and/or the rationale for low confidence in a particular discovering, in order that even relevant outcomes could be prioritized by safety/devops engineers.
Efficiency concerns
A contextual scanner that’s based mostly on information move evaluation (for instance, a scanner that tries to find out whether or not a particular perform’s argument is coming from attacker-controlled enter or not) will all the time have an choice in its implementation whether or not to supply extra correct outcomes or to run quicker. For instance, probably the most correct kind of contextual scanner should not less than:
- Enable for an infinite name depth when attempting to construct an intra-module information move graph between an attacker-controlled supply and the requested sink.
- Contemplate inter-module calls when constructing the info move graph.
These operations drastically improve the scanner’s run time.
When coping with a large amount of scanned artifacts per minute (as could also be requested from a JFrog Artifactory/Xray occasion) we should obtain a fragile steadiness between the accuracy and the velocity of the contextual scanner.
Even when contemplating the mentioned limitations, 78% continues to be a huge variety of vulnerabilities that may be both de-prioritized or ignored. Moreover, we count on this quantity to turn out to be larger as know-how advances and as much less “relevant by default” CVEs are found.


