The most recent breach introduced by LastPass is a significant trigger for concern to safety stakeholders. As typically happens, we’re at a safety limbo – on the one hand, as LastPass has famous, customers who adopted LastPass greatest practices could be uncovered to virtually zero to extraordinarily low danger. Nonetheless, to say that password greatest practices will not be adopted is a wild understatement. The truth is that there are only a few organizations during which these practices are actually enforced. This places safety groups within the worst place, the place publicity to compromise is sort of sure, however pinpointing the customers who created this publicity is sort of unimaginable.
To help them all through this difficult time, Browser Safety answer LayerX has launched a free providing of its platform, enabling safety groups to realize visibility into all browsers on which the LastPass extension is put in and mitigate the potential impacts of the LastPass breach on their environments by informing susceptible customers and require them to implement MFA on their accounts and if required, roll out a devoted Grasp Password reset process to get rid of adversaries’ skills to leverage a compromised Grasp Password for malicious entry (To request entry to the free instrument, fill this way)
Recapping LastPass’s Announcement: What Knowledge Do Adversaries Have and What is the Threat?
Per LastPass’s web site, ‘The menace actor was additionally capable of copy a backup of buyer vault knowledge from the encrypted storage container which is saved in a proprietary binary format that accommodates each unencrypted knowledge, akin to web site URLs, in addition to fully-encrypted delicate fields akin to web site usernames and passwords, safe notes, and form-filled knowledge.’
The derived danger is that ‘the menace actor might try to make use of brute drive to guess your grasp password and decrypt the copies of vault knowledge they took. Due to the hashing and encryption strategies we use to guard our prospects, it will be extraordinarily troublesome to try to brute drive guess grasp passwords for these prospects who comply with our password greatest practices.’
Not Implementing LastPass Password Greatest Practices Exposes the Grasp Password to the Vault
The final part about ‘greatest practices’ is probably the most alarming one. Password greatest practices? How many individuals preserve password greatest practices? The practical – but unlucky – reply is: not many. That holds true even within the context of corporate-managed purposes. With regards to private apps, it is not an exaggeration to imagine that password reuse is the norm fairly than the outlier. The danger LastPass’s breach introduces apply to each use instances. Let’s perceive why.
The Precise Threat: Malicious Entry to Company Sources
Let’s divide organizations into two varieties:
Kind A: Organizations the place LastPass is used as a part of the corporate coverage for vaulting passwords to entry corporate-managed apps, both for all customers or in particular departments. In that case, the priority is easy – an adversary that manages to crack or acquire an worker’s LastPass Grasp Password might simply entry the company’s delicate assets.
Kind B: Organizations the place LastPass is used independently by workers (whether or not for private or work use) or by particular teams within the group, with out IT data, for apps of alternative. In that case, the priority is that an adversary who manages to crack or acquire an worker’s LastPass Grasp Password would benefit from customers’ tendency for password reuse and, after compromising the passwords within the vault, will discover one which can be used to entry company apps.
The CISO’s Lifeless Finish: Sure Menace however Extraordinarily Low Mitigation Capabilities
No matter whether or not a company falls into kind A or B, the chance is evident. What intensifies the problem for the CISO on this state of affairs is that whereas there may be excessive likelihood – to not say certainty – that there are workers in her or his setting whose consumer accounts are more likely to turn out to be compromised, the CISO has very restricted capacity to know who these workers are, not to mention take the required steps to mitigate the chance they impose.
LayerX Free Providing: 100% Visibility into LastPass Assault Floor as Effectively as Proactive Safety Measures
LayerX has launched a free instrument that assists safety groups in understanding their group’s publicity to the LastPass breach, maps all of the susceptible customers and purposes, and applies safety mitigations.
LayerX’s instrument is delivered as an enterprise extension to the browser your workers are utilizing and therefore supplies quick visibility into all browser extensions and shopping actions of each consumer. This allows CISOs to realize the next:
- LastPass Utilization Mapping: Finish-to-end visibility into all browsers on which the LastPass extension is put in, no matter whether or not it is a part of the company coverage (kind A) or personally used (kind B). The instrument maps all purposes and net locations whose credentials are saved in LastPass. It must be famous that the visibility challenges for kind B organizations are far more extreme than for kind A and can’t be addressed by any answer apart from LayerX’s instrument.
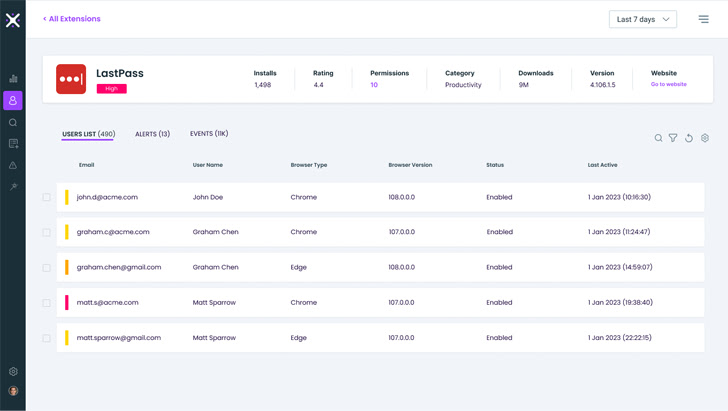 |
| LayerX’s LastPass Report |
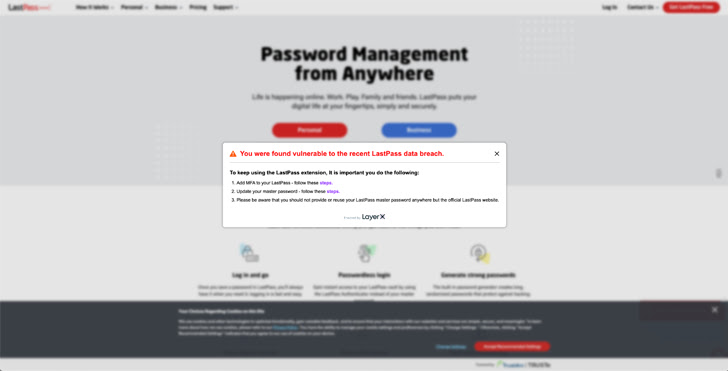 |
| The LayerX notification despatched to susceptible customers |
- Figuring out Customers at Threat: Leveraging this information, safety groups can inform susceptible customers and require them implement MFA on their accounts. They will additionally roll out a devoted Grasp Password reset process to get rid of adversaries’ skills to leverage a compromised Grasp Password for malicious entry.


