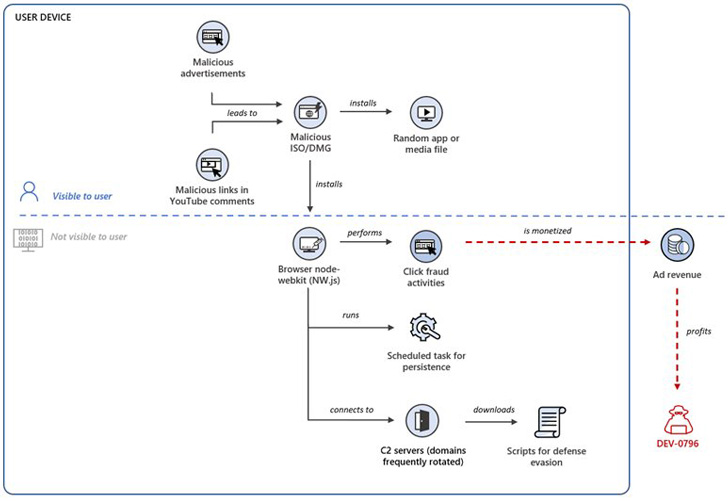
Microsoft stated it is monitoring an ongoing large-scale click on fraud marketing campaign focusing on players by way of stealthily deployed browser extensions on compromised techniques.
“[The] attackers monetize clicks generated by a browser node-webkit or malicious browser extension secretly put in on units,” Microsoft Safety Intelligence stated in a sequence of tweets over the weekend.
The tech large’s cybersecurity division is monitoring the growing menace cluster underneath the title DEV-0796.
Connect chains mounted by the adversary begin with an ISO file that is downloaded onto a sufferer’s machine upon clicking on a malicious advert or feedback on YouTube. The ISO file, when opened, is designed to put in a browser node-webkit (aka NW.js) or rogue browser extension.
It is price noting that the ISO file masquerades as hacks and cheats for the Krunker first-person shooter recreation. Cheats are applications that assist players achieve an added benefit past the obtainable capabilities throughout gameplay.
Additionally used within the assaults are DMG recordsdata, that are Apple Disk Picture recordsdata primarily used to distribute software program on macOS, indicating that the menace actors are focusing on a number of working techniques.
The findings arrive as Kaspersky disclosed particulars of one other marketing campaign that lures players in search of cheats on YouTube into downloading self-propagating malware able to putting in crypto miners and different data stealers.
“Malware and undesirable software program distributed as cheat applications stand out as a specific menace to players’ safety, particularly for individuals who are eager on common recreation sequence,” the Russian cybersecurity agency stated in a latest report.