Microsoft on Monday revealed it took steps to disrupt phishing operations undertaken by a “extremely persistent risk actor” whose goals align carefully with Russian state pursuits.
The corporate is monitoring the espionage-oriented exercise cluster underneath its chemical element-themed moniker SEABORGIUM, which it mentioned overlaps with a hacking group also referred to as Callisto, COLDRIVER, and TA446.
“SEABORGIUM intrusions have additionally been linked to hack-and-leak campaigns, the place stolen and leaked information is used to form narratives in focused international locations,” Microsoft’s risk looking groups mentioned. “Its campaigns contain persistent phishing and credential theft campaigns resulting in intrusions and information theft.”
Assaults launched by the adversarial collective are identified to focus on the identical organizations utilizing constant methodologies utilized over lengthy durations of time, enabling it to infiltrate the victims’ social networks by a mix of impersonation, rapport constructing, and phishing.
Microsoft mentioned it noticed “solely slight deviations of their social engineering approaches and in how they ship the preliminary malicious URL to their targets.”
Major targets embrace protection and intelligence consulting firms, non-governmental organizations (NGOs) and intergovernmental organizations (IGOs), assume tanks, and better schooling entities positioned within the U.S. and the U.Okay., and to a lesser extent within the Baltics, the Nordics, and the Jap Europe.
Extra targets of curiosity encompass former intelligence officers, consultants in Russian affairs, and Russian residents overseas. Greater than 30 organizations and private accounts are estimated to have been on the receiving finish of its campaigns for the reason that begin of 2022.
All of it begins with a reconnaissance of potential people by leveraging pretend personas created on social media platforms like LinkedIn, earlier than establishing contact with them by way of benign e-mail missives originating from newly-registered accounts configured to match the names of the impersonated people.
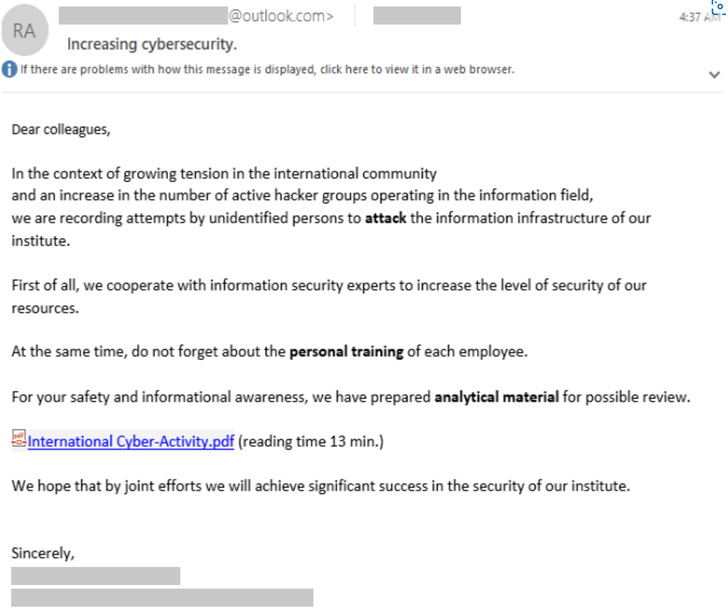
Within the occasion the goal falls sufferer to the social engineering try, the risk actor prompts the assault sequence by sending a weaponized message embedding a booby-trapped PDF doc or a hyperlink to a file hosted on OneDrive.
“SEABORGIUM additionally abuses OneDrive to host PDF information that comprise a hyperlink to the malicious URL,” Microsoft mentioned. “The actors embrace a OneDrive hyperlink within the physique of the e-mail that when clicked directs the consumer to a PDF file hosted inside a SEABORGIUM-controlled OneDrive account.”
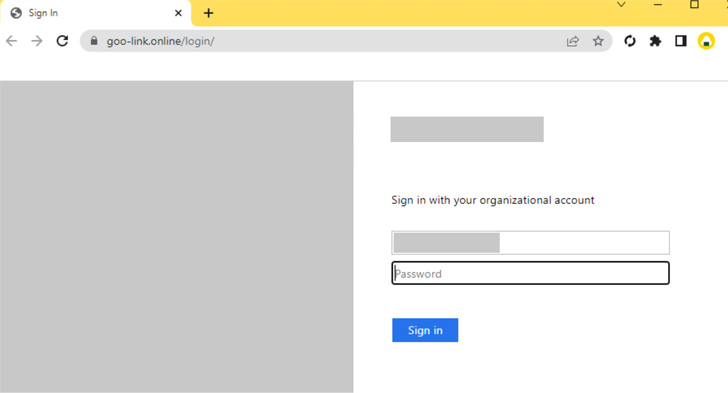
Moreover, the adversary has been discovered to disguise its operational infrastructure by resorting to seemingly innocent open redirects to ship customers to the malicious server, which, in flip, prompts customers to enter their credentials to view the content material.
The final part of assaults entails abusing the stolen credentials to entry the sufferer’s e-mail accounts, benefiting from the unauthorized logins to exfiltrate emails and attachments, arrange e-mail forwarding guidelines to make sure sustained information assortment and different follow-on actions.
“There have been a number of instances the place SEABORGIUM has been noticed utilizing their impersonation accounts to facilitate dialog with particular individuals of curiosity and, because of this, had been included in conversations, typically unwittingly, involving a number of events,” Redmond identified.