Microsoft on Wednesday disclosed particulars of a now-patched “excessive severity vulnerability” within the TikTok app for Android that would let attackers take over accounts when victims clicked on a malicious hyperlink.
“Attackers might have leveraged the vulnerability to hijack an account with out customers’ consciousness if a focused consumer merely clicked a specifically crafted hyperlink,” Dimitrios Valsamaras of the Microsoft 365 Defender Analysis Group mentioned in a write-up.
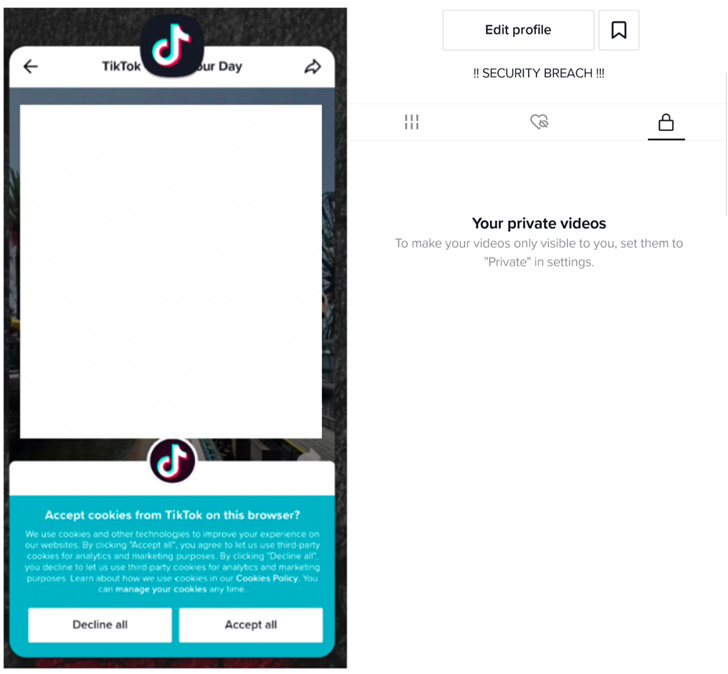
Profitable exploitation of the flaw might have permitted malicious actors to entry and modify customers’ TikTok profiles and delicate data, resulting in the unauthorized publicity of personal movies. Attackers might even have abused the bug to ship messages and add movies on behalf of customers.
The problem, addressed in model 23.7.3, impacts two flavors of its Android app com.ss.android.ugc.trill (for East and Southeast Asian customers) and com.zhiliaoapp.musically (for customers in different nations apart from India, the place it is banned). Mixed, the apps have greater than 1.5 billion installations between them.
Tracked as CVE-2022-28799 (CVSS rating: 8.8), the vulnerability has to do with the app’s dealing with of what is referred to as a deeplink, a particular hyperlink that enables apps to open a particular useful resource inside one other app put in on the system reasonably than directing customers to a web site.
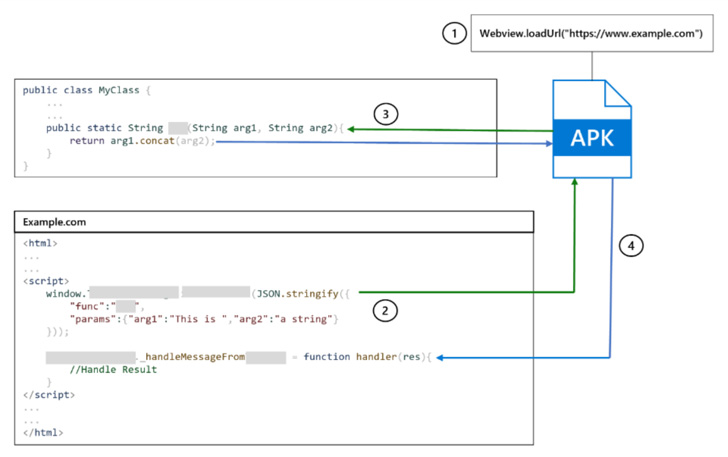
“A crafted URL (unvalidated deeplink) can drive the com.zhiliaoapp.musically WebView to load an arbitrary web site,” in accordance with an advisory for the flaw. “This may increasingly enable an attacker to leverage an hooked up JavaScript interface for the takeover with one click on.”
Put merely, the flaw makes it doable to avoid the apps’s restrictions to reject untrusted hosts and cargo any web site of the attacker’s selection via the Android System WebView, a mechanism to show net content material on different apps.
“The filtering takes place on the server-side and the choice to load or reject a URL relies on the reply acquired from a selected HTTP GET request,” Valsamaras defined, including the static evaluation “indicated that it’s doable to bypass the server-side verify by including two further parameters to the deeplink.”
A consequence of this exploit designed to hijack WebView to load rogue web sites is that it might allow the adversary to invoke over 70 uncovered TikTok endpoints, successfully compromising a consumer’s profile integrity. There is not any proof that the bug has been weaponized within the wild.
“From a programming perspective, utilizing JavaScript interfaces poses vital dangers,” Microsoft famous. “A compromised JavaScript interface can doubtlessly enable attackers to execute code utilizing the appliance’s ID and privileges.”