Microsoft is now taking steps to forestall Distant Desktop Protocol (RDP) brute-force assaults as a part of the most recent builds for the Home windows 11 working system in an try to lift the safety baseline to satisfy the evolving risk panorama.
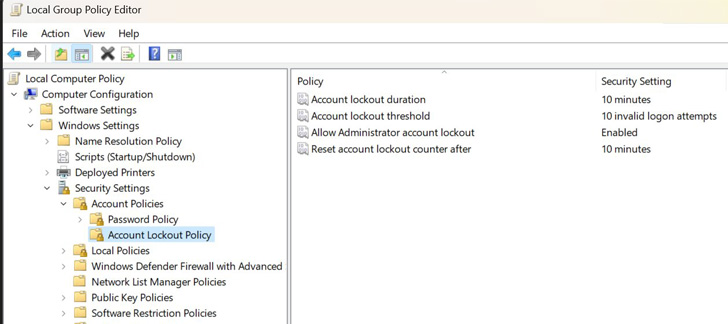
To that finish, the default coverage for Home windows 11 builds – notably, Insider Preview builds 22528.1000 and newer – will mechanically lock accounts for 10 minutes after 10 invalid sign-in makes an attempt.
“Win11 builds now have a DEFAULT account lockout coverage to mitigate RDP and different brute-force password vectors,” David Weston, Microsoft’s vice chairman for OS safety and enterprise, mentioned in a sequence of tweets final week. “This method could be very generally utilized in Human Operated Ransomware and different assaults — this management will make brute forcing a lot more durable which is superior!”
It is price declaring that whereas this account lockout setting is already included in Home windows 10, it is not enabled by default.
The function, which follows the corporate’s determination to resume blocking of Visible Fundamental Software (VBA) macros for Workplace paperwork, can also be anticipated to be backported to older variations of Home windows and Home windows Server.
Other than malicious macros, brute-forced RDP entry has lengthy been one of many most widespread strategies utilized by risk actors to achieve unauthorized entry to Home windows techniques.
LockBit, which is likely one of the most energetic ransomware gangs of 2022, is thought to usually depend on RDP for preliminary foothold and follow-on actions. Different households seen utilizing the identical mechanism embody Conti, Hive, PYSA, Crysis, SamSam, and Dharma.
In implementing this new threshold, the target is to considerably diminish the effectiveness of the RDP assault vector and forestall intrusions that depend on password-guessing and compromised credentials.
“Brute-forcing RDP is the commonest technique utilized by risk actors making an attempt to achieve entry to Home windows techniques and execute malware, ” Zscaler famous final 12 months.
“Risk actors scan for […] publicly open RDP ports to conduct distributed brute-force assaults. Programs that use weak credentials are simple targets, and, as soon as compromised, attackers promote entry to the hacked techniques on the darkish net to different cybercriminals.”
That mentioned, Microsoft, in its documentation, warns of potential denial-of-service (DoS) assaults that might be orchestrated by abusing the Account lockout threshold coverage setting.
“A malicious consumer may programmatically try a sequence of password assaults towards all customers within the group,” the corporate notes. “If the variety of makes an attempt is bigger than the worth of Account lockout threshold, the attacker may probably lock each account.”