Microsoft has lastly launched a safety replace that addresses a zero-day
vulnerability that went unpatched for greater than two years. The vulnerability, referred to as DogWalk, seems within the nationwide vulnerability index as CVE-2022-34713. Microsoft has assigned the vulnerability a excessive severity score of seven.8. The corporate’s safety advisory confirms that the vulnerability has been exploited within the wild, prompting the US Cybersecurity and Infrastructure Safety Company (CISA) so as to add the vulnerability to its
identified exploited vulnerabilities catalog and require federal businesses underneath its jurisdiction to use Microsoft’s patch by August thirtieth.
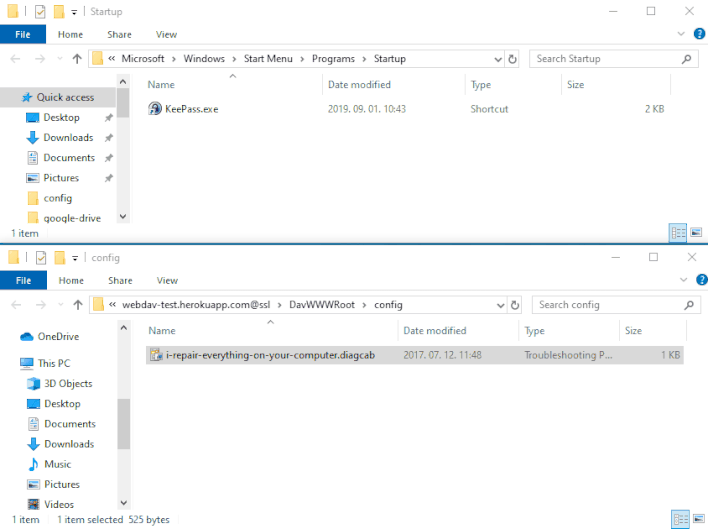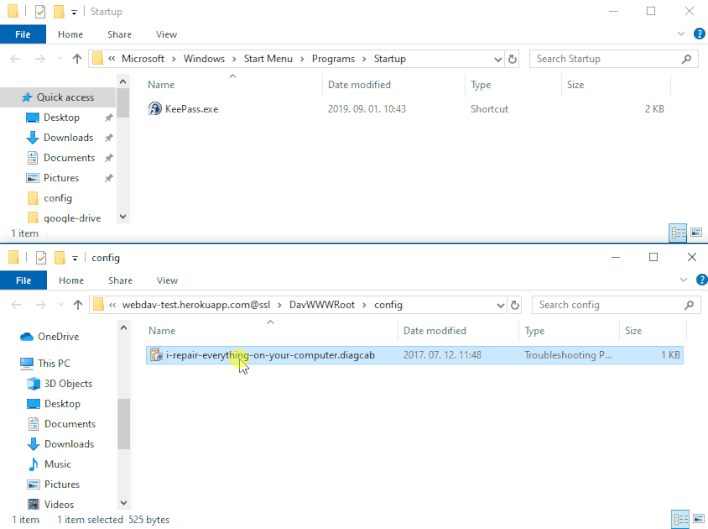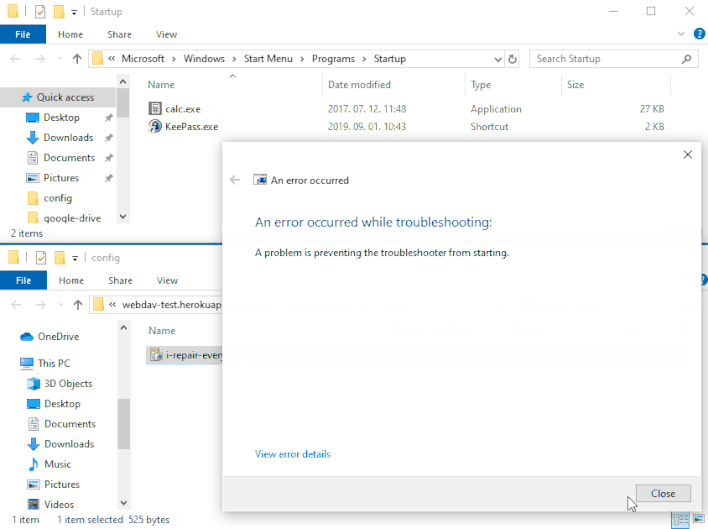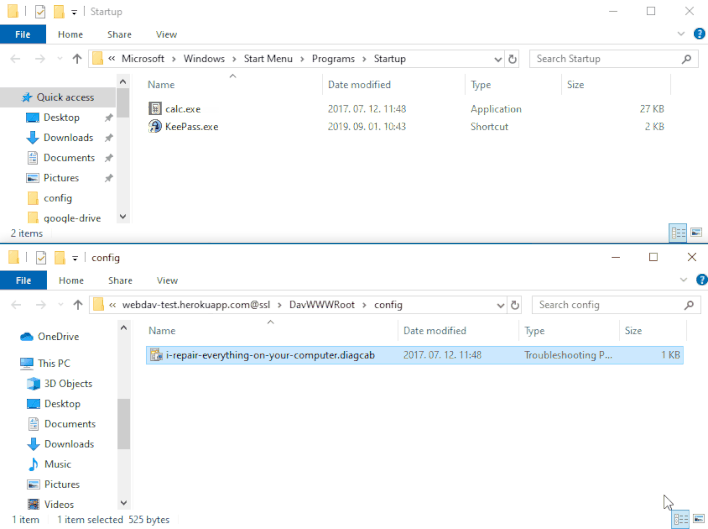
The DogWalk vulnerability was first found and reported to Microsoft close to the tip of 2019 by safety researcher Imre Rad. Nevertheless, on the time, Microsoft didn’t take into account the researcher’s findings to be indicative of a vulnerability that wanted patching. Nevertheless, Microsoft later modified its tune after additional exploits of the vulnerability grew to become identified. The vulnerability in query exists within the Microsoft Assist Diagnostic Software (MSDT). This instrument can obtain additional diagnostic directions by loading information with the .diagcab file extension. As a safety measure, MSDT gained’t execute .diagcab packages except they’ve been signed with a legitimate code signing certificates.
Nevertheless, Imre Rad found that when initially opened by MSDT, .diagcab packages can save any file to any location on a machine. This happens earlier than MSDT performs the signature examine to resolve whether or not to execute the bundle. As proven within the demonstration above, a risk actor can exploit this habits by distributing a .diagcab bundle that locations a malicious executable within the Home windows Startup folder. As soon as this malicious executable is in place, Home windows will mechanically run the executable upon subsequent startup. This vulnerability permits an attacker to bypass Home windows’ signature verification examine by tricking unsuspecting victims into double-clicking on a .diagcab file, normally by social engineering.
Home windows customers ought to set up Microsoft’s August ninth Patch Tuesday replace to deal with this vulnerability.
Prime Picture Credit score: Johann on Pexels