Earlier this week, Microsoft confirmed a “new” 0-Day distant code execution vulnerability inside Alternate Servers. Whereas it isn’t essentially new within the household of Proxy-Exploits, essential infrastructure continues to be being attacked now, and tons of of hundreds of servers are doubtlessly weak to this problem, so patch as quickly as potential.
On Wednesday this week, cybersecurity agency GTSC launched a weblog publish titled “New Assault Marketing campaign Utilized A New 0-Day RCE Vulnerability On Microsoft Alternate Server,” which outlined detected exploit requests just like the ProxyShell vulnerability of 2021. Shortly thereafter, Microsoft dove into triage mode and assigned CVE-2022-41040 and CVE-2022-41082, a server-side request forgery and distant code execution vulnerability, respectively. Nonetheless, it was famous that to use both vulnerability, an attacker should have legitimate credentials for a non-admin consumer on the Alternate server.
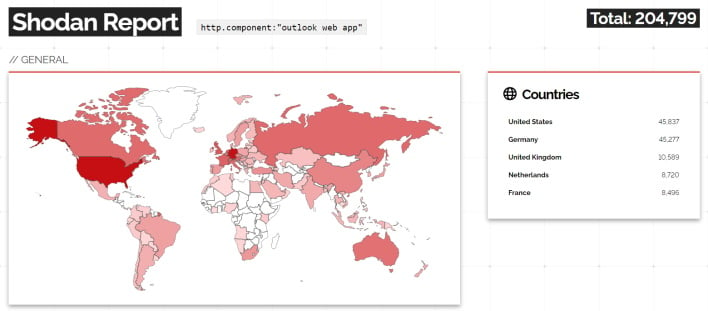
Cybersecurity researcher and purveyor of vulnerability names and logos Kevin Beaumont shortly dubbed this problem “ProxyNotShell” as a result of “it’s the similar path and SSRF/RCE pair from [ProxyShell in 2021]… however with authentication.” He additional defined that this drawback solely impacts those that run Microsoft Alternate on-premise and don’t have the Outlook Internet App (OWA) going through the web. Nonetheless, utilizing Shodan, an internet-connected gadget search engine, it’s reported that there are doubtlessly 204,000 uncovered OWA pages that means these organizations ought to assess their publicity and doubtlessly mitigate the difficulty.
To this finish, Microsoft offers three choices for mitigation on its weblog, the primary of which is successfully “sit tight,” as prospects with the Alternate Server Emergency Mitigation Service enabled may have mitigations pushed mechanically. Past this, Microsoft has created a script that prospects can deploy, or directors can create URL rewrite guidelines themselves. Microsoft additionally notes that Alternate On-line prospects needn’t take any motion, however Beaumont counters this and explains that Alternate Hybrid servers are doubtlessly weak and ought to be up to date and secured.
It must also be famous that there’s info out there that may assist admins uncover if both vulnerability has been deployed towards their infrastructure. Hopefully, with all this protection and mitigations now rolling out, this drawback is not going to spiral uncontrolled over the weekend. In any other case, if you happen to or a beloved admin has been affected by ProxyNotShell linked to Alternate publicity, chances are you’ll be entitled to monetary compensation.