Microsoft on Thursday attributed the current spate of ransomware incidents concentrating on transportation and logistics sectors in Ukraine and Poland to a menace cluster that shares overlaps with the Russian state-sponsored Sandworm group.
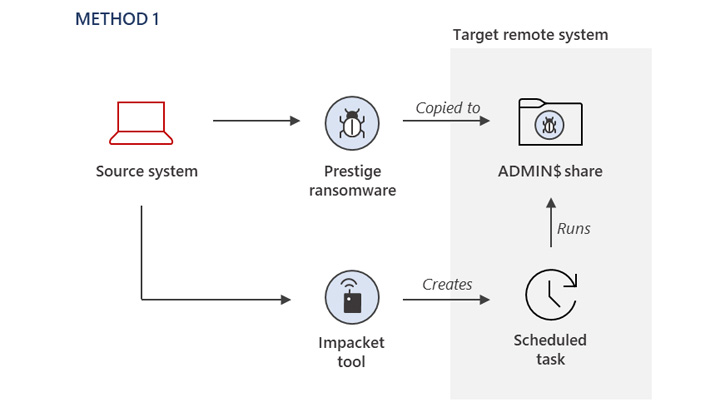
The assaults, which have been disclosed by the tech big final month, concerned a pressure of beforehand undocumented malware referred to as Status and is alleged to have taken place inside an hour of one another throughout all victims.
The Microsoft Risk Intelligence Heart (MSTIC) is now monitoring the menace actor below its element-themed moniker Iridium (née DEV-0960), citing overlaps with Sandworm (aka Iron Viking, TeleBots, and Voodoo Bear).
“This attribution evaluation is predicated on forensic artifacts, in addition to overlaps in victimology, tradecraft, capabilities, and infrastructure, with recognized Iridium exercise,” MSTIC mentioned in an replace.
The corporate additionally additional assessed the group to have orchestrated compromise exercise concentrating on most of the Status victims way back to March 2022, earlier than culminating within the deployment of the ransomware on October 11.
The tactic of preliminary compromise nonetheless stays unknown, though it is suspected that it concerned getting access to extremely privileged credentials essential to activate the killchain.
“The Status marketing campaign might spotlight a measured shift in Iridium’s damaging assault calculus, signaling elevated threat to organizations straight supplying or transporting humanitarian or navy help to Ukraine,” the corporate mentioned.
The findings come over a month after Recorded Future linked one other exercise group (UAC-0113) with ties to the Sandworm actor as having singled out Ukrainian customers by masquerading as telecom suppliers within the nation to ship backdoors onto compromised machines.
Microsoft, in its Digital Protection Report revealed final week, additional referred to as out Iridium for its sample of concentrating on vital infrastructure and operational know-how entities.
“Iridium deployed the Industroyer2 malware in a failed effort to go away tens of millions of individuals in Ukraine with out energy,” Redmond mentioned, including the menace actor used “phishing campaigns to realize preliminary entry to desired accounts and networks in organizations inside and out of doors Ukraine.”
The event additionally arrives amid sustained ransomware assaults geared toward industrial organizations worldwide in the course of the third quarter of 2022, with Dragos reporting 128 such incidents in the course of the time interval in comparison with 125 within the earlier quarter.
“The LockBit ransomware household account for 33% and 35% respectively of the full ransomware incidents that concentrate on industrial organizations and infrastructures within the final two quarters, because the teams added new capabilities of their new LockBit 3.0 pressure,” the economic safety agency mentioned.
Different outstanding strains noticed in Q3 2022 embody Cl0p, MedusaLocker, Sparta, BianLian, Donuts, Onyx, REvil, and Yanluowang.