Cryptocurrency funding firms are the goal of a creating menace cluster that makes use of Telegram teams to hunt out potential victims.
Microsoft’s Safety Risk Intelligence Middle (MSTIC) is monitoring the exercise underneath the identify DEV-0139, and builds upon a current report from Volexity that attributed the identical set of assaults to North Korea’s Lazarus Group.
“DEV-0139 joined Telegram teams used to facilitate communication between VIP purchasers and cryptocurrency change platforms and recognized their goal from among the many members,” the tech big stated.
The adversary subsequently impersonated one other cryptocurrency funding firm and invited the sufferer to affix a distinct Telegram chat group underneath the pretext of asking for suggestions on the buying and selling payment construction utilized by change platforms throughout VIP tiers.
It is value declaring that the VIP program is designed to reward high-volume merchants with unique buying and selling payment incentives and reductions primarily based on the 30-day buying and selling quantity.
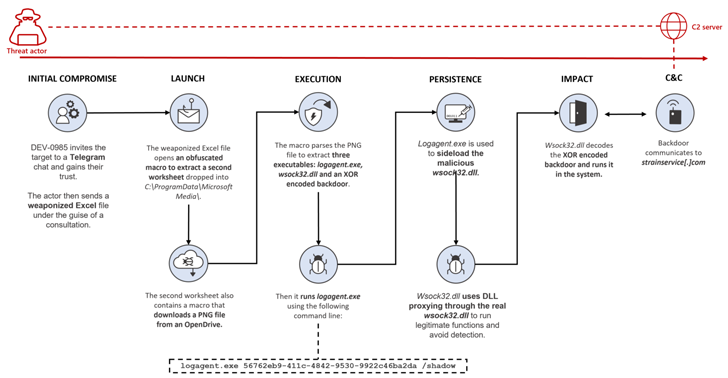
This assault chain notably dovetails with Volexity’s evaluation of an October 2022 marketing campaign, whereby the menace actor pivoted from utilizing MSI installer information to a weaponized Microsoft Excel doc displaying the supposed cryptocurrency coin charges.
Microsoft described the doc as containing possible correct information to extend the chance of success of the marketing campaign, suggesting that DEV-0139 is nicely versed within the inside workings of the crypto trade.
The malware-laced Excel file, for its half, is tasked with executing a malicious macro that is used to stealthily drop and execute a second Excel worksheet, which, in flip, features a macro that downloads a PNG picture file hosted on OpenDrive.
This picture file accommodates three executables, every of which is used to launch the next-stage payload, finally paving the best way for a backdoor that lets the menace actor remotely entry the contaminated system.
Moreover, the payment construction spreadsheet is password-protected in a bid to persuade the goal into enabling macros, thereby initiating malicious actions. A metadata evaluation of the file exhibits that it was created on October 14, 2022 by a person named Wolf.
DEV-0139 has additionally been linked to an alternate assault sequence by which an MSI bundle for a pretend utility named “CryptoDashboardV2” is delivered instead of a malicious Excel doc to deploy the identical implant.
The backdoor primarily permits distant entry to the host by gathering info from the focused system and connecting to a command-and-control (C2) server to obtain extra instructions.
“The cryptocurrency market stays a subject of curiosity for menace actors,” Microsoft stated. “Focused customers are recognized via trusted channels to extend the prospect of success.”
In recent times, Telegram has not solely witnessed widespread adoption within the cryptocurrency trade, but in addition been co-opted by menace actors trying to talk about zero-day vulnerabilities, provide stolen information, and market their providers via the favored messaging platform.
“With customers dropping confidence within the anonymity provided by boards, illicit marketplaces are more and more turning to Telegram,” Optimistic Applied sciences disclosed in a brand new examine of 323 public Telegram channels and teams with over a million subscribers in complete.
“The variety of distinctive cyberattacks is continually rising, and the marketplace for cybercriminal providers is increasing and transferring into odd social media and messaging apps, thereby considerably reducing the entry threshold for cybercriminals.”