 Utilizing a easy e mail containing a voice mail attachment, an ingenious phishing assault captures credentials whereas maintaining monitor of the domains being attacked.
Utilizing a easy e mail containing a voice mail attachment, an ingenious phishing assault captures credentials whereas maintaining monitor of the domains being attacked.
It’s no shock that Microsoft continues to be a model used as a part of credential-harvesting assaults, because the accounts compromised present risk actors with entry to a respectable e mail deal with. So, this newest phishing rip-off recognized by safety researchers at Zscaler’s ThreatLabz first makes use of Zscaler themselves because the preliminary model impersonated, after which spoofs a Microsoft 365 logon web page to seize credentials.
However what makes this assault attention-grabbing is using a number of model impersonation efforts, a faux voice mail message, and a novel monitoring methodology utilized by the cybercriminals.
The phishing e mail first makes use of a “From” e mail deal with that aligns with the sufferer group. The voice mail attachment makes use of a music be aware icon to throw off the recipient sufferer, however really is an HTML attachment.
The HTML doc serves as a URL redirector that factors the sufferer to a malicious URL distinctive to the sufferer group. In accordance with Zscaler, the redirection URL consists of the next components:
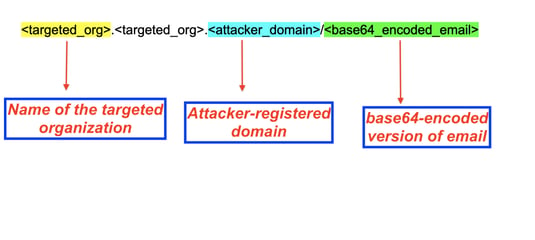
Supply: Zscaler
A CAPTCHA verify is used to evade URL evaluation advised, with the ultimate a part of the assault being the spoofed Microsoft 365 logon web page.
This assault demonstrates the delicate efforts cybercriminals take to maintain assaults from being detected and to trick customers into falling sufferer to such scams. Safety Consciousness Coaching is an efficient device that helps customers perceive the strategies these assaults use to idiot them, empowering the person to stay vigilant when interacting with suspicious emails just like the one recognized by Zscaler.


