Hook up with Cloud SQL situations with non-public IPs in minutes

In case you use the Google Cloud Platform (GCP), it’s widespread to entry Cloud SQL in your Cloud Run providers. That is alleged to be a simple activity as a result of each Cloud SQL and Cloud Run are in the identical community. Nevertheless, once you do it your self, chances are you’ll not be capable to do it efficiently in a short while as a result of many paperwork on-line are both outdated or over-complicated. After some trials and errors for a number of hours, I lastly bought it to work. I feel it’s well worth the effort to jot down down my answer so it might probably save others a while as nicely. It’s truly fairly easy in the event you do it appropriately.
Arrange Cloud SQL
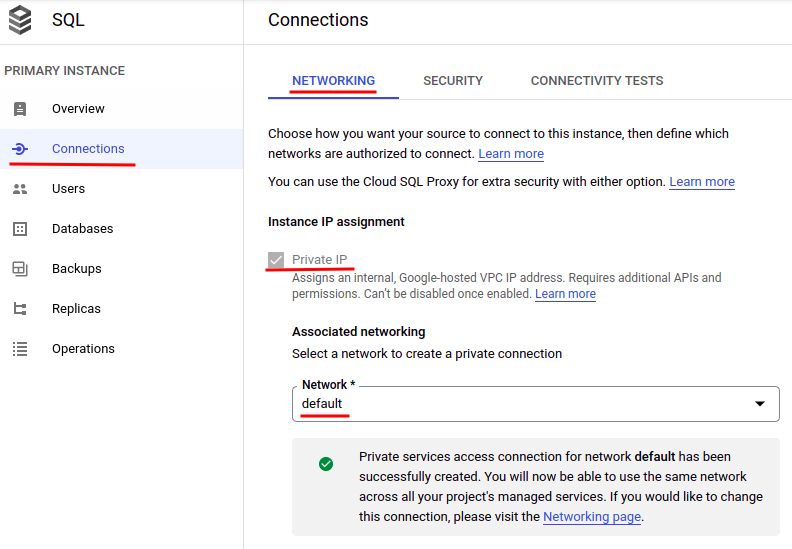
Since each Cloud SQL and Cloud Run are on the Google Cloud Platform, it’s higher to attach by non-public IP for minimal community latency. Allow the “Personal IP” choice if it’s not enabled but. Preserve be aware of the community and personal IP deal with which will likely be used later.

Create a VPC connector
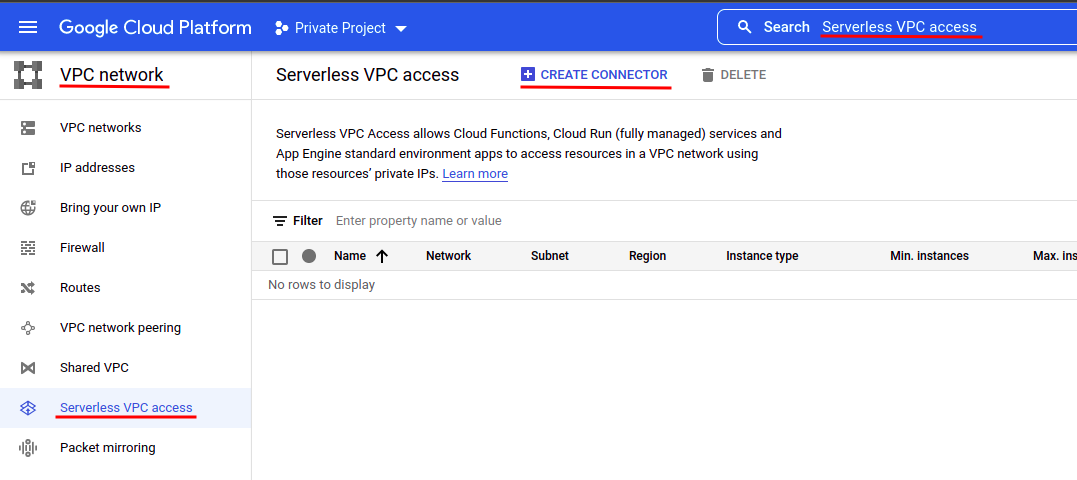
Digital Personal Cloud (VPC) is a digital model of a bodily community, carried out within Google’s manufacturing community which can be utilized to attach all forms of assets created on the platform. It’s truly a fairly complicated and summary idea. For now, you solely want to know that Serverless VPC Entry permits Cloud Capabilities, Cloud Run providers, and App Engine apps to entry assets in a VPC community utilizing their non-public IPs. Let’s create a VPC connector that can be utilized by our Cloud Run service to connect with our Cloud SQL situations.
Seek for “Serverless VPC entry” within the high search field and select “Serverless VPC entry (VPC community)”. Then click on “CREATE CONNECTOR” to create a brand new VPC connector:
Fill within the type as follows:
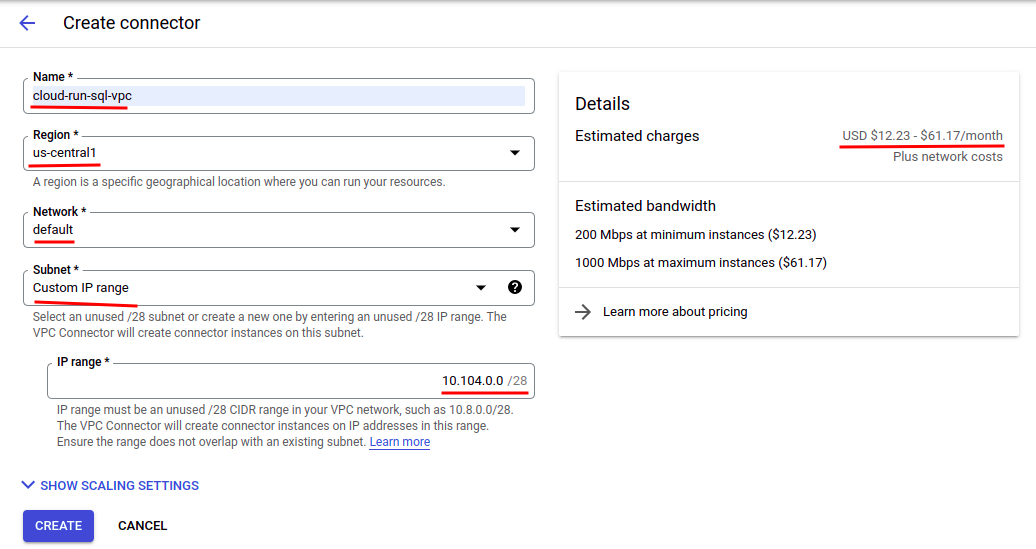
- Give it a singular title.
- Select the identical area as your Cloud SQL occasion and Cloud Run service. This is essential in any other case you can not connect with the Cloud SQL occasion with this connector.
- Select the identical community as your Cloud SQL occasion. That is additionally vital when you have a number of networks.
- Select “Customized IP vary” for “Subnet”.
- Specify the IP vary to cowl the non-public IP deal with of your Cloud SQL occasion. For this instance, it’s set to “10.104.0.0”. The IP vary can’t battle with present ones.
Now you may click on “CREATE” to create the VPC connector. It needs to be famous that VPC connectors will not be free. They’re truly fairly costly to make use of. Subsequently, do bear in mind to delete them when they don’t seem to be wanted anymore.
Configure a Cloud Run service account
The Cloud Run service account, which is Compute Engine default service account by default, ought to have the Cloud SQL Consumer position with permissions to connect with Cloud SQL.
On the IAM web page, seek for “Compute Engine default service account”, then click on the pencil button so as to add the Cloud SQL Consumer position for it:


Create a Cloud Run service
Lastly, let’s create a Cloud Run service and join it to our Cloud SQL occasion with the VPC connector simply created. Attempt to discover “Cloud Run” on the GCP platform and click on “CREATE SERVICE” to create a brand new one:
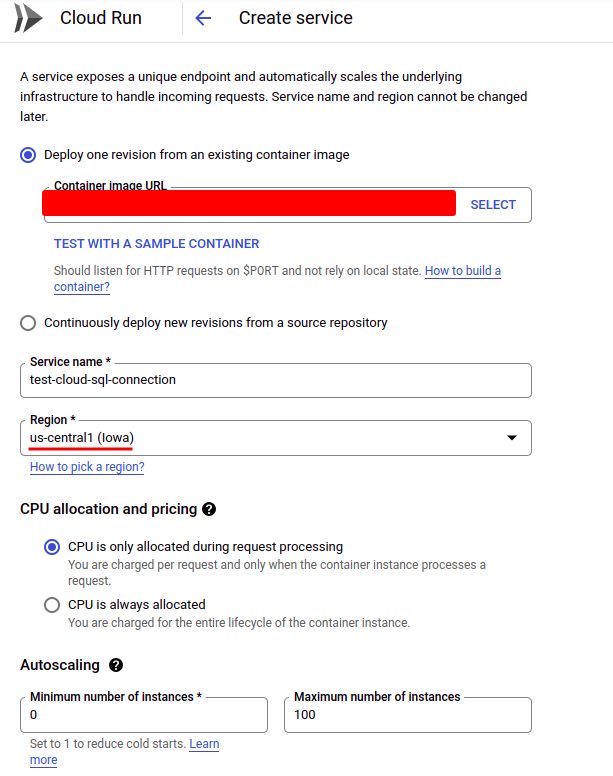
Importantly, select the identical area as your Cloud SQL occasion and VPC connector. For a extra detailed introduction to methods to deploy a Cloud Run service routinely, this put up could be useful.
For demonstration functions, we might usually choose “Permit all visitors” and “Permit unauthenticated invocations”. You possibly can add extra fine-grained authentication if wanted with IAM.

Now develop the “Container, Variables & Secrets and techniques, Connections, Safety” part and specify the connections and surroundings variables. Let’s set the connection first. Click on the “CONNECTIONS” tab, then click on “ADD CONNECTION” so as to add a brand new one. Choose the Cloud SQL occasion to which you wish to join. Then select the “VPC connector” created within the earlier step. Notice that the VPC connector gained’t be proven if the area of the connector is completely different from that of the Cloud Run service being created.
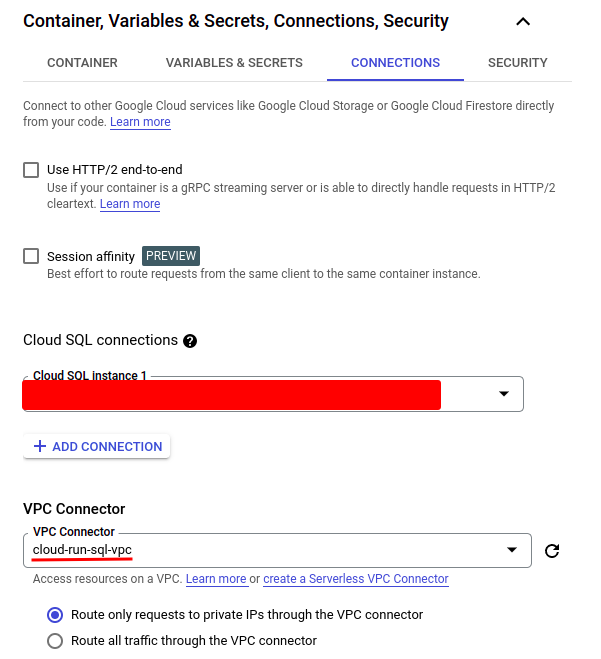
Then we have to create some surroundings variables for our DB connection which might be utilized in our Cloud Run service:
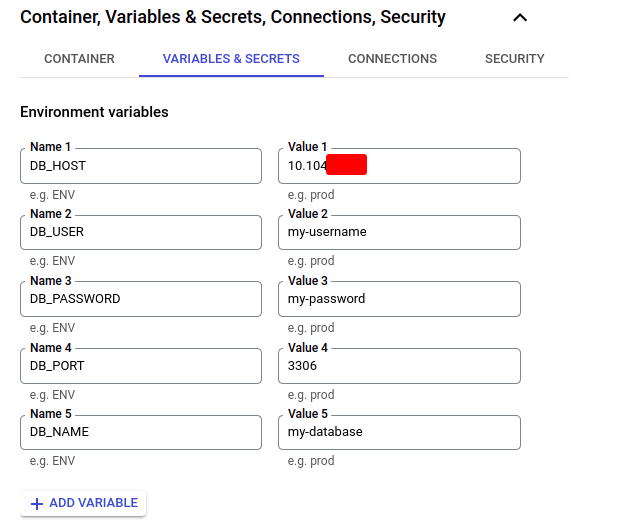
Very importantly! We have to specify the non-public IP deal with of our Cloud SQL occasion because the DB host, not “127.0.0.1” or “localhost”, as proven in some tutorials, in any other case, it gained’t work.
The surroundings variables will likely be used within the code of your Cloud Run service to connect with the Cloud SQL occasion. In case you use SQLAlchemy to connect with a MySQL database, the code could be like this:
If wanted, you may verify the corresponding articles for methods to use SQLAlchemy to execute plain SQL queries and create ORM fashions.
Now it is best to be capable to connect with your Cloud SQL situations out of your Cloud Run providers. Have a attempt!
Conclusion
It’s quite common that we have to connect with Cloud SQL if we host our backend code on Cloud Run. Nevertheless, trivial as it might appear, there are fairly just a few pitfalls that can make the connection fail. On this article, we’ve coated the final setup procedures and likewise highlighted the pitfalls that will incur hours of struggling time. The principle takeaway from this put up is as follows:
- The community of the SQL occasion and the VPC connector needs to be the identical.
- The areas of the SQL occasion, VPC connector, and Cloud Run service needs to be the identical.
- The non-public IP of the SQL occasion needs to be used within the Cloud Run service for connection.


