An open supply command-and-control (C2) framework referred to as Havoc is being adopted by menace actors as a substitute for different well-known reputable toolkits like Cobalt Strike, Sliver, and Brute Ratel.
Cybersecurity agency Zscaler mentioned it noticed a brand new marketing campaign at first of January 2023 focusing on an unnamed authorities group that utilized Havoc.
“Whereas C2 frameworks are prolific, the open-source Havoc framework is a sophisticated post-exploitation command-and-control framework able to bypassing essentially the most present and up to date model of Home windows 11 defender as a result of implementation of superior evasion strategies similar to oblique syscalls and sleep obfuscation,” researchers Niraj Shivtarkar and Niraj Shivtarkar mentioned.
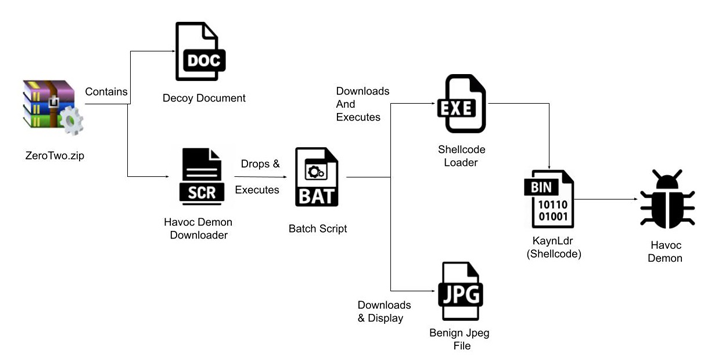
The assault sequence documented by Zscaler begins with a ZIP archive that embeds a decoy doc and a screen-saver file that is designed to obtain and launch the Havoc Demon agent on the contaminated host.
Demon is the implant generated by way of the Havoc Framework and is analogous to the Beacon delivered by way of Cobalt Strike to realize persistent entry and distribute malicious payloads.
It additionally comes with all kinds of options that makes it troublesome to detect, turning it right into a profitable software within the fingers of menace actors whilst cybersecurity distributors are pushing again towards the abuse of such reputable pink group software program.
“After the demon is deployed efficiently on the goal’s machine, the server is ready to execute numerous instructions on the goal system,” the researchers mentioned, stating that the server logs the command and its response upon execution. The outcomes are subsequently encrypted and transmitted again to the C2 server.
Havoc has additionally been employed in reference to a fraudulent npm module dubbed aabquerys that, as soon as put in, triggers a three-stage course of to retrieve the Demon implant. The package deal has since been taken down.