The botnet behind the biggest HTTPS distributed denial-of-service (DDoS) assault in June 2022 has been linked to a spate of assaults geared toward almost 1,000 Cloudflare prospects.
Calling the highly effective botnet Mantis, the net efficiency and safety firm attributed it to greater than 3,000 HTTP DDoS assaults in opposition to its customers.
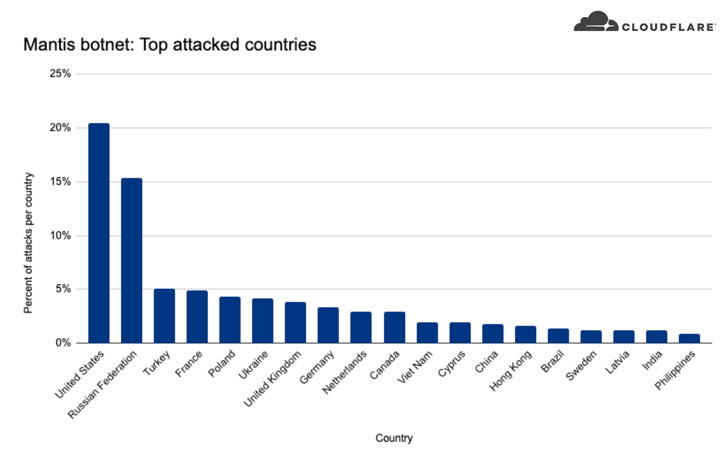
Probably the most attacked business verticals embrace web and telecom, media, gaming, finance, enterprise, and purchasing, of which over 20% of the assaults focused U.S.-based corporations, adopted by Russia, Turkey, France, Poland, Ukraine, the U.Ok., Germany, the Netherlands, and Canada.
Final month, the corporate mentioned it mitigated a record-breaking DDoS assault geared toward an unnamed buyer web site utilizing its Free plan that peaked at 26 million requests per second (RPS), with every node producing roughly 5,200 RPS.
The tsunami of junk visitors lasted lower than 30 seconds and generated greater than 212 million HTTPS requests from greater than 1,500 networks in 121 nations, topped by Indonesia, the U.S., Brazil, Russia, and India.
“The Mantis botnet operates a small fleet of roughly 5,000 bots, however with them can generate a large drive — answerable for the biggest HTTP DDoS assaults now we have ever noticed,” Cloudflare’s Omer Yoachimik mentioned.
Mantis stands out for various causes. The primary is its means to hold out HTTPS DDoS assaults, that are costly in nature as a result of computational assets required to determine a safe TLS encrypted connection.
Secondly, not like different conventional botnets that depend on IoT units akin to DVRs and routers, Mantis leverages hijacked digital machines and highly effective servers, equipping it with extra assets.
These volumetric assaults goal to generate extra visitors than the goal can course of, inflicting the sufferer to exhaust its assets. Whereas adversaries have historically utilized UDP to launch amplification assaults, there was a shift to newer TCP mirrored amplification vectors that make use of middleboxes.
Microsoft, in Could 2022, disclosed that it prevented about 175,000 UDP mirrored amplification assaults over the previous 12 months that have been geared toward its Azure infrastructure. It additionally noticed a TCP mirrored amplification assault on an Azure useful resource in Asia that reached 30 million packets per second (pps) and lasted quarter-hour.
“Mirrored amplification assaults are right here to remain and pose a severe problem for the web group,” the Azure Networking Group famous. “They proceed to evolve and exploit new vulnerabilities in protocols and software program implementations to bypass typical countermeasures.”