Three restaurant ordering platforms MenuDrive, Harbortouch, and InTouchPOS have been the goal of two Magecart skimming campaigns that resulted within the compromise of a minimum of 311 eating places.
The trio of breaches has led to the theft of greater than 50,000 fee card data from these contaminated eating places and posted on the market on the darkish net.
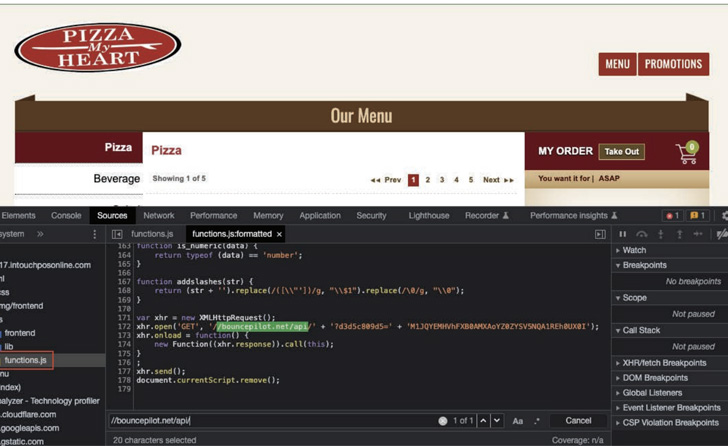
“The web ordering platforms MenuDrive and Harbortouch have been focused by the identical Magecart marketing campaign, leading to e-skimmer infections on 80 eating places utilizing MenuDrive and 74 utilizing Harbortouch,” cybersecurity agency Recorded Future revealed in a report.
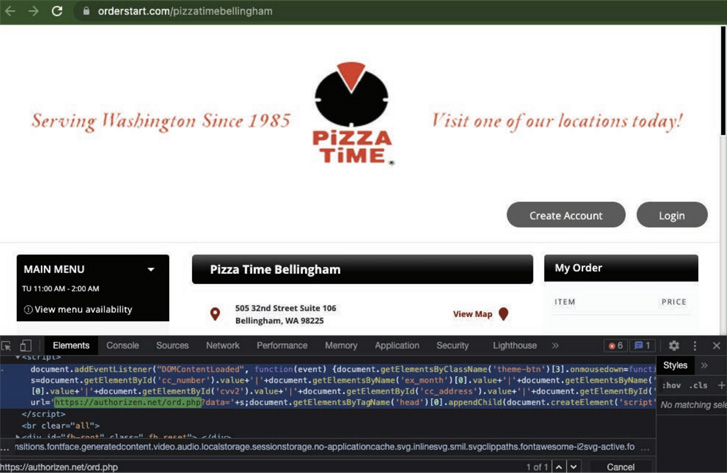
“InTouchPOS was focused by a separate, unrelated Magecart marketing campaign, leading to e-skimmer infections on 157 eating places utilizing the platform.”
Magecart actors have a historical past of infecting e-commerce web sites with JavaScript skimmers to steal web shoppers’ fee card knowledge, billing data, and different personally identifiable data (PII).
The primary set of actions is believed to have began round January 18, 2022, and continued till the malicious area used within the marketing campaign was blocked on Could 26. The InTouchPOS marketing campaign, then again, has remained energetic since November 12, 2021.
It is price noting that the info exfiltration area used within the infections of MenuDrive and Harbortouch has additionally been recognized by the U.S. Federal Bureau of Investigation (FBI) in a Could 2022 flash alert.
The assaults entail inserting malicious PHP code into the companies’ on-line checkout pages by profiting from recognized safety flaws within the companies to scrape and transmit the shopper knowledge to a server underneath the attacker’s management.
The thought is that by focusing on on-line ordering platforms, it might probably result in a state of affairs the place when even a single platform is attacked, dozens and even a whole lot of eating places can have their transactions compromised, which permits “cybercriminals to steal huge quantities of buyer fee card knowledge disproportionate to the variety of techniques they really hack.”
The event is critical for quite a few causes. First, the intrusions are a departure from the risk actor’s conventional focusing on of the Magento e-commerce platform, a truth exemplified by the uptick in skimmer assaults geared toward a WordPress plugin named WooCommerce.
Moreover, it serves to focus on how Magecart campaigns are actually singling out small, native eating places that depend on third-party software program from lesser-known on-line ordering companies in lieu of designing their very own checkout net pages, successfully widening the pool of assault vectors.
“Centralized ordering platforms servicing a number of retailers provide a novel alternative for Magecart risk actors to gather buyer PII and fee card knowledge,” the researchers stated. “Cybercriminals’ growing curiosity in focusing on on-line ordering platforms represents a brand new dimension of danger for eating places.”