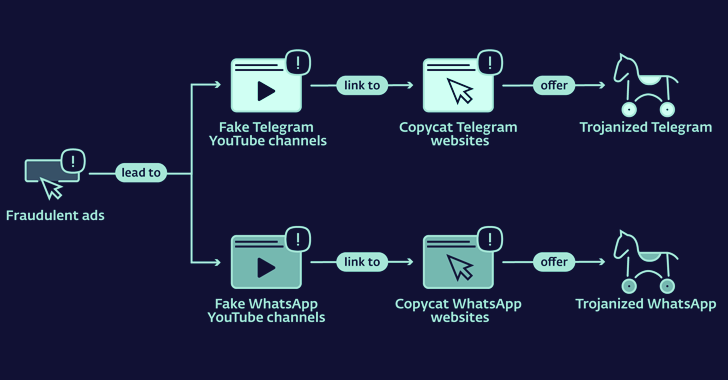
Copycat web sites for fast messaging apps like Telegram and WhatApp are getting used to distribute trojanized variations and infect Android and Home windows customers with cryptocurrency clipper malware.
“All of them are after victims’ cryptocurrency funds, with a number of focusing on cryptocurrency wallets,” ESET researchers Lukáš Štefanko and Peter Strýček mentioned in a brand new evaluation.
Whereas the first occasion of clipper malware on the Google Play Retailer dates again to 2019, the event marks the primary time Android-based clipper malware has been constructed into on the spot messaging apps.
“Furthermore, a few of these apps use optical character recognition (OCR) to acknowledge textual content from screenshots saved on the compromised units, which is one other first for Android malware,” the Slovak cybersecurity agency added.
The assault chain begins with unsuspecting customers clicking on fraudulent advertisements on Google search outcomes that result in a whole bunch of sketchy YouTube channels, which then direct them to lookalike Telegram and WhatsApp web sites.
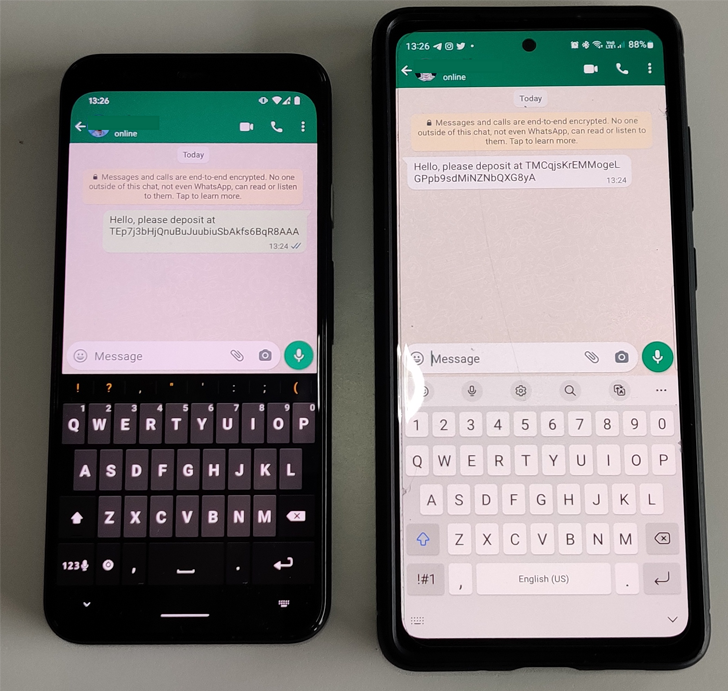
What’s novel concerning the newest batch of clipper malware is that it is able to intercepting a sufferer’s chats and changing any despatched and obtained cryptocurrency pockets addresses with addresses managed by the menace actors.
One other cluster of clipper malware makes use of OCR to search out and steal seed phrases by leveraging a authentic machine studying plugin referred to as ML Package on Android, thereby making it attainable to empty the wallets.
A 3rd cluster is designed to maintain tabs on Telegram conversations for sure Chinese language key phrases associated to cryptocurrencies, each hard-coded and obtained from a server, and if that’s the case, exfiltrate the whole message, together with the username, group or channel title, to a distant server.
Lastly, a fourth set of Android clippers include capabilities to change the pockets tackle in addition to harvest gadget data and Telegram information resembling messages and contacts.
The rogue Android APK bundle names are listed under –
- org.telegram.messenger
- org.telegram.messenger.web2
- org.tgplus.messenger
- io.busniess.va.whatsapp
- com.whatsapp
ESET mentioned it additionally discovered two Home windows-based clusters, one which is engineered to swap pockets addresses and a second group that distributes distant entry trojans (RATs) instead of clippers to realize management of contaminated hosts and perpetrate crypto theft.
Uncover the Hidden Risks of Third-Occasion SaaS Apps
Are you conscious of the dangers related to third-party app entry to your organization’s SaaS apps? Be a part of our webinar to study concerning the varieties of permissions being granted and how one can reduce threat.
All of the analyzed RAT samples are based mostly on the publicly obtainable Gh0st RAT, barring one, which employs extra anti-analysis runtime checks throughout its execution and makes use of the HP-socket library to speak with its server.
It is also value stating that these clusters, regardless of following an similar modus operandi, symbolize disparate units of exercise probably developed by totally different menace actors.
The marketing campaign, like a related malicious cyber operation that got here to gentle final yr, is geared in direction of Chinese language-speaking customers, primarily motivated by the truth that each Telegram and WhatsApp are blocked within the nation.
“Individuals who want to use these companies should resort to oblique technique of acquiring them,” the researchers mentioned. “Unsurprisingly, this constitutes a ripe alternative for cybercriminals to abuse the scenario.”