A number of campaigns that distributed trojanized and typosquatted packages on the NPM open supply repository have been recognized because the work of a single menace actor dubbed LofyGang.
Checkmarx mentioned it found 199 rogue packages totaling 1000’s of installations, with the group working for over a 12 months with the purpose of stealing bank card knowledge in addition to person accounts related to Discord Nitro, gaming, and streaming companies.
“LofyGang operators are seen selling their hacking instruments in hacking boards, whereas among the instruments are shipped with a hidden backdoor,” the software program safety firm mentioned in a report shared with The Hacker Information previous to its publication.
Numerous items of the assault puzzle have already been reported by JFrog, Sonatype, and Kaspersky (which referred to as it LofyLife), however the newest evaluation pulls the varied operations collectively underneath one organizational umbrella that Checkmarx is referring to as LofyGang.
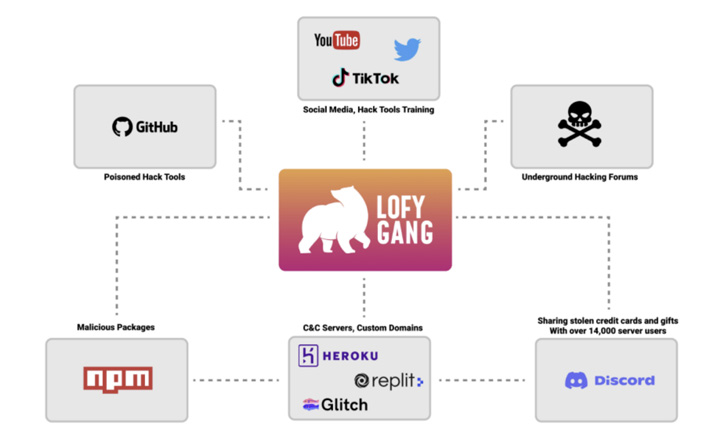
Believed to be an organized crime group of Brazilian origin, the attackers have a monitor report of utilizing sock puppet accounts to promote their instruments and companies on GitHub, YouTube, and leaking 1000’s of Disney+ and Minecraft accounts on underground hacking boards.
It is also identified to make use of a Discord server created almost a 12 months in the past on October 31, 2021, to offer technical help and talk with their members. One in every of its fundamental choices is a service that sells faux Instagram followers.
“Discord, Repl.it, glitch, GitHub, and Heroku are just some companies LofyGang is utilizing as [command-and-control] servers for his or her operation,” the researchers famous.
What’s extra, the fraudulent packages traced again to the group have been discovered to embed password stealers and Discord-specific malware, a few of that are designed to steal bank cards.
To hide the size of the provision chain assault, the packages are deliberately revealed by means of completely different person accounts in order that different weaponized libraries stay unaffected on the repositories even when one in every of them is noticed and eliminated by the maintainers.
Moreover, the adversary has been discovered utilizing a sneaky approach whereby the top-level bundle is stored freed from malware however have it rely upon one other bundle that introduces the malicious capabilities.
That is not all. Even the hacking instruments shared by LofyGang on GitHub rely upon malicious packages, successfully performing as a conduit to deploy persistent backdoors on the operator’s machines.
The findings are one more indication that menace actors are more and more setting their sights on the open supply ecosystem as a stepping level to widen the scope and effectiveness of the assaults.
“Communities are being shaped round using open-source software program for malicious functions,” the researchers concluded. “We imagine that is the beginning of a development that may improve within the coming months.”