A risk actor related to the LockBit 3.0 ransomware-as-a-service (RaaS) operation has been noticed abusing the Home windows Defender command-line software to decrypt and cargo Cobalt Strike payloads.
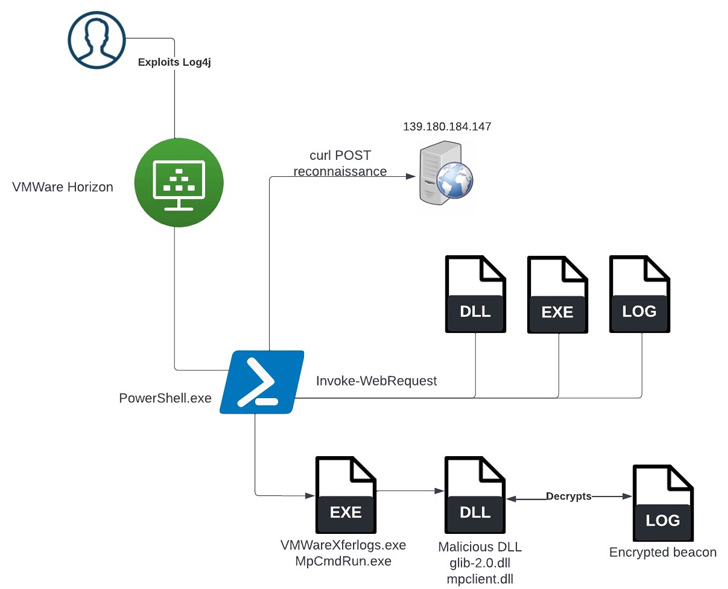
Based on a report revealed by SentinelOne final week, the incident occurred after acquiring preliminary entry by way of the Log4Shell vulnerability in opposition to an unpatched VMware Horizon Server.
“As soon as preliminary entry had been achieved, the risk actors carried out a collection of enumeration instructions and tried to run a number of post-exploitation instruments, together with Meterpreter, PowerShell Empire, and a brand new approach to side-load Cobalt Strike,” researchers Julio Dantas, James Haughom, and Julien Reisdorffer stated.
LockBit 3.0 (aka LockBit Black), which comes with the tagline “Make Ransomware Nice Once more!,” is the subsequent iteration of the prolific LockBit RaaS household that emerged in June 2022 to iron out important weaknesses found in its predecessor.
It is notable for instituting what is the first-ever bug bounty for a RaaS program. Apart from that includes a revamped leak web site to name-and-shame non-compliant targets and publish extracted information, it additionally features a new search software to make it simpler to seek out particular sufferer information.
The usage of living-off-the-land (LotL) strategies by cyber intruders, whereby reliable software program and features out there within the system are used for post-exploitation, shouldn’t be new and is often seen as an try to evade detection by safety software program.
Earlier this April, a LockBit affiliate was discovered to have leveraged a VMware command-line utility known as VMwareXferlogs.exe to drop Cobalt Strike. What’s totally different this time round is using MpCmdRun.exe to attain the identical objective.
MpCmdRun.exe is a command-line software for finishing up varied features in Microsoft Defender Antivirus, together with scanning for malicious software program, accumulating diagnostic information, and restoring the service to a earlier model, amongst others.
Within the incident analyzed by SentinelOne, the preliminary entry was adopted by downloading a Cobalt Strike payload from a distant server, which was subsequently decrypted and loaded utilizing the Home windows Defender utility.
“Instruments that ought to obtain cautious scrutiny are any that both the group or the group’s safety software program have made exceptions for,” the researchers stated.
“Merchandise like VMware and Home windows Defender have a excessive prevalence within the enterprise and a excessive utility to risk actors if they’re allowed to function outdoors of the put in safety controls.”
The findings come as preliminary entry brokers (IABs) are actively promoting entry to firm networks, together with managed service suppliers (MSPs), to fellow risk actors for revenue, in flip providing a approach to compromise downstream prospects.
In Might 2022, cybersecurity authorities from Australia, Canada, New Zealand, the U.Ok., and the U.S. warned of assaults weaponizing susceptible managed service suppliers (MSPs) as an “preliminary entry vector to a number of sufferer networks, with globally cascading results.”
“MSPs stay a lovely provide chain goal for attackers, significantly IABs,” Huntress researcher Harlan Carvey stated, urging corporations to safe their networks and implement multi-factor authentication (MFA).