ACM.48 Leveraging our naming conventions to permit customers to solely deploy and replace the suitable sources in a cloud account
I’m going to point out you how one can restrict the power for customers add and replace solely a subset of CloudFormation stacks and a few caveats with this strategy.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Interlude: Nonetheless ready for copyrighted supplies to be faraway from of those websites. I added info on the way to report copyright infringement to Google’s authorized group right here:
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
KMS code refactoring
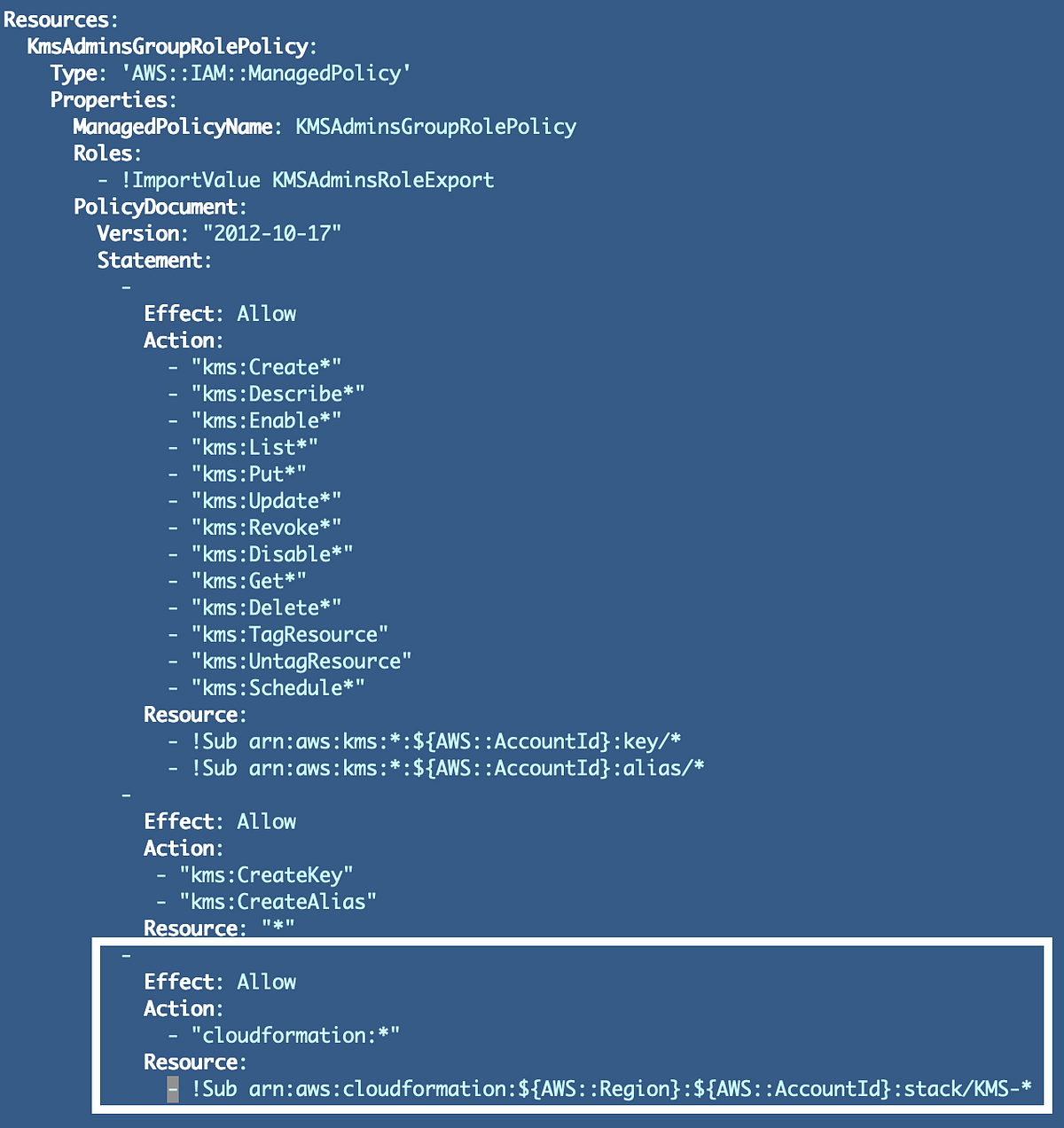
Simply as I did with customers and teams in earlier posts, I refactored the KMS to make use of features to persistently identify stacks. The code references the widespread features utilizing a supply command on the high. As soon as that supply command will get executed the features within the exterior file will be referred to as as if they’re in the identical file. Right here I’m together with the widespread features I wrote about within the final submit.
supply "../../Features/shared_functions.sh
Now what I need to do is barely permit the KMS directors to create and edit stacks for KMS keys. To begin with, I solely permit the KMS directors to create replace, and delete keys within the coverage I launched earlier and proven under. Now that we’ve a naming conference for our stacks, each stack that deploys a KMS key ought to begin with this prefix:
KMS-Key
Each stack that deploys a KMS Key Alias ought to appear like this:
KMS-KeyAlias
Some other KMS sources would additionally begin with “KMS-”. So what I can do is later the useful resource ARN for the CloudFormation permissions granted to our KMS person to finish with KMS-*. That means the KMS Admins can solely deploy or alter KMS stacks. As well as, the one permission the function has is to handle KMS keys. The one permissions the KMSAdmins group has is to imagine the KMSAdmins function.

Caveats with this strategy
Simply since you solely permit somebody to deploy a CloudFormation stack with KMS within the identify doesn’t imply the stack solely has KMS sources in it. That is solely proscribing them from naming sources one thing else. Nevertheless, on this coverage, the KMS admins solely have permission to handle KMS sources.
Considering this by way of, a KMS Administrator would wish to imagine this function to carry out KMS actions. Whereas assuming this function that person would solely be allowed to do no matter that function can do. If the person may also assume one other function, let’s say a task to add information to an S3 bucket, then the permission that function has wouldn’t be obtainable when the person assumes this function. I haven’t absolutely examined that — so that you may need to — however that’s the way it ought to work.
In the event you assigned this coverage on to a person or group, and then you definately assign a bunch of different insurance policies to that person or group, now it is advisable to take into consideration how all of the permissions work collectively. You additionally want to consider priority, which I wrote about on this submit:
Priority has to do with how all of the polices assigned to a principal in AWS work collectively and which guidelines will get evaluated and utilized in what order.
Though we’re proscribing the KMS directors to solely handle roles beginning with the identify KMS- whereas assuming this function and solely managing KMS sources by way of the opposite permissions the function has, this doesn’t have an effect on another customers within the account.
As acknowledged within the AWS documentation for CloudFormation:
By default, anybody with stack replace permissions can replace all the sources within the stack.
As defined within the above documentation additionally it is attainable to use insurance policies to stacks. That subject is past this submit and perhaps one thing I’ll discover later.
However the backside line is that if another person has no restrictions on the CloudFormation stack names they’ll deploy, they might create a stack with a reputation beginning with KMS that will or could not have KMS sources in it. Moreover if the person has permissions to function on the stack they might have an effect on any useful resource within the stack. Due to this fact, it is advisable to perceive how your entire useful resource, IAM, and belief insurance policies work collectively inside your cloud account.
And that, my buddies, is why I say it is best to have separate IAM directors:
As I defined earlier, safety structure isn’t a guidelines:
It has to do with the way you architect your permissions, entry, authentication, and all of your different safety controls and the way they work collectively. Inside IAM itself the best way you assemble all of your guidelines and insurance policies impacts what gaps you might have that permit folks to do one thing they shouldn’t. Past that IAM has to work together with networking, encryption and all of your different safety controls.
In an effort to implement the naming conference I’ve been writing about and notice the associated safety advantages we are going to want a holistic, complete and automatic strategy to safety insurance policies inside our cloud account. If you are able to do that, you’ll have sources which might be correctly named and it must be simpler to determine anomalies and deal with safety occasions and incidents.
Teri Radichel
In the event you appreciated this story please clap and comply with:
Medium: Teri Radichel or E-mail Listing: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests providers by way of LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2022
All of the posts on this sequence:
____________________________________________
Creator:
Cybersecurity for Executives within the Age of Cloud on Amazon

Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration take a look at or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Assets by Teri Radichel: Cybersecurity and Cloud safety lessons, articles, white papers, shows, and podcasts