KrebsOnSecurity lately reviewed a duplicate of the non-public chat messages between members of the LAPSUS$ cybercrime group within the week main as much as the arrest of its most lively members final month. The logs present LAPSUS$ breached T-Cellular a number of occasions in March, stealing supply code for a variety of firm initiatives. T-Cellular says no buyer or authorities data was stolen within the intrusion.
LAPSUS$ is thought for stealing knowledge after which demanding a ransom to not publish or promote it. However the leaked chats point out this mercenary exercise was of little curiosity to the tyrannical teenage chief of LAPSUS$, whose obsession with stealing and leaking proprietary laptop supply code from the world’s largest tech corporations finally led to the group’s undoing.
From its inception in December 2021 till its implosion late final month, LAPSUS$ operated brazenly on its Telegram chat channel, which rapidly grew to greater than 40,000 followers after the group began utilizing it to leak enormous volumes of delicate knowledge stolen from sufferer firms.
However LAPSUS$ additionally used non-public Telegram channels that had been restricted to the core seven members of the group. KrebsOnSecurity lately obtained every week’s price of those non-public conversations between LAPSUS$ members as they plotted their ultimate assaults late final month.
The candid conversations present LAPSUS$ incessantly obtained the preliminary entry to focused organizations by buying it from websites like Russian Market, which promote entry to remotely compromised programs, in addition to any credentials saved on these programs.
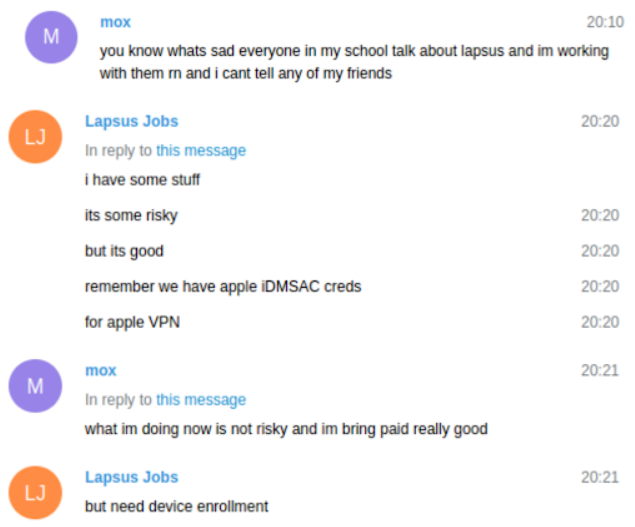
The logs point out LAPSUS$ had precisely zero issues shopping for, stealing or sweet-talking their means into worker accounts at corporations they wished to hack. The larger problem for LAPSUS$ was the topic talked about by “Lapsus Jobs” within the screenshot above: Machine enrollment. Generally, this concerned social engineering staff on the focused agency into including certainly one of their computer systems or mobiles to the listing of gadgets allowed to authenticate with the corporate’s digital non-public community (VPN).
The messages present LAPSUS$ members constantly focused T-Cellular staff, whose entry to inner firm instruments may give them the whole lot they wanted to conduct hassle-free “SIM swaps” — reassigning a goal’s cell phone quantity to a tool they managed. These unauthorized sim swaps enable an attacker to intercept a goal’s textual content messages and telephone calls, together with any hyperlinks despatched by way of SMS for password resets, or one-time codes despatched for multi-factor authentication.

The LAPSUS$ group had fun at this screenshot posted by their chief, White, which reveals him studying a T-Cellular information alert about their hack into Samsung. White is viewing the web page by way of a T-Cellular worker’s digital machine.
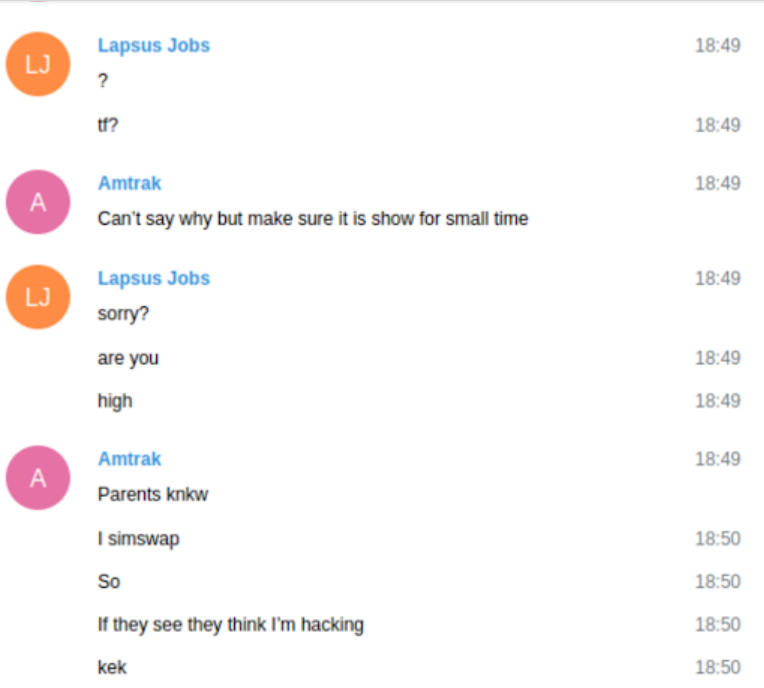
In a single chat, the LAPSUS$ chief — a 17-year-old from the U.Okay. who goes by the nicknames “White,” “WhiteDoxbin” and “Oklaqq” — is sharing his display screen with one other LAPSUS$ member who used the handles “Amtrak” and “Asyntax.”
The 2 had been exploring T-Cellular’s inner programs, and Amtrak requested White to obscure the T-Cellular brand on his display screen. In these chats, the consumer “Lapsus Jobs” is White. Amtrak explains this odd request by saying their dad and mom are conscious Amtrak was beforehand concerned in SIM swapping.
“Dad and mom know I simswap,” Amtrak stated. “So, in the event that they see [that] they suppose I’m hacking.”
The messages reveal that every time LAPSUS$ was lower off from a T-Cellular worker’s account — both as a result of the worker tried to log in or change their password — they might simply discover or purchase one other set of T-Cellular VPN credentials. T-Cellular presently has roughly 75,000 staff worldwide.
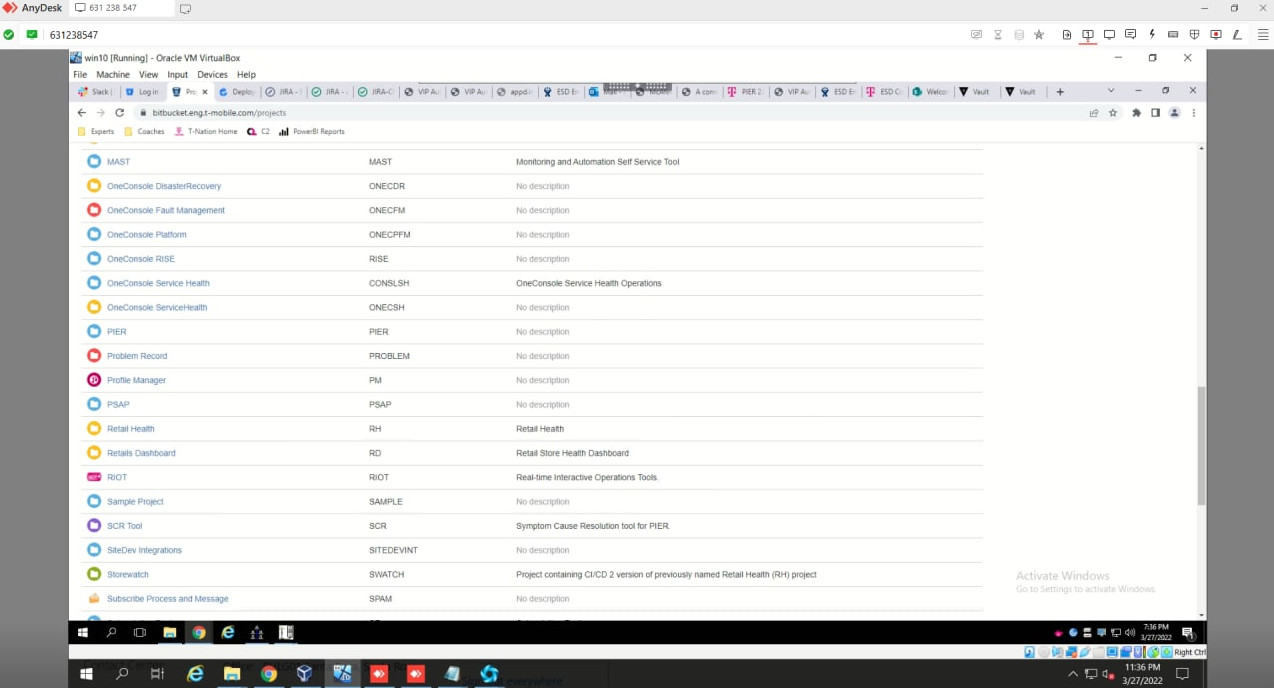
On March 19, 2022, the logs and accompanying screenshots present LAPSUS$ had gained entry to Atlas, a strong inner T-Cellular software for managing buyer accounts.
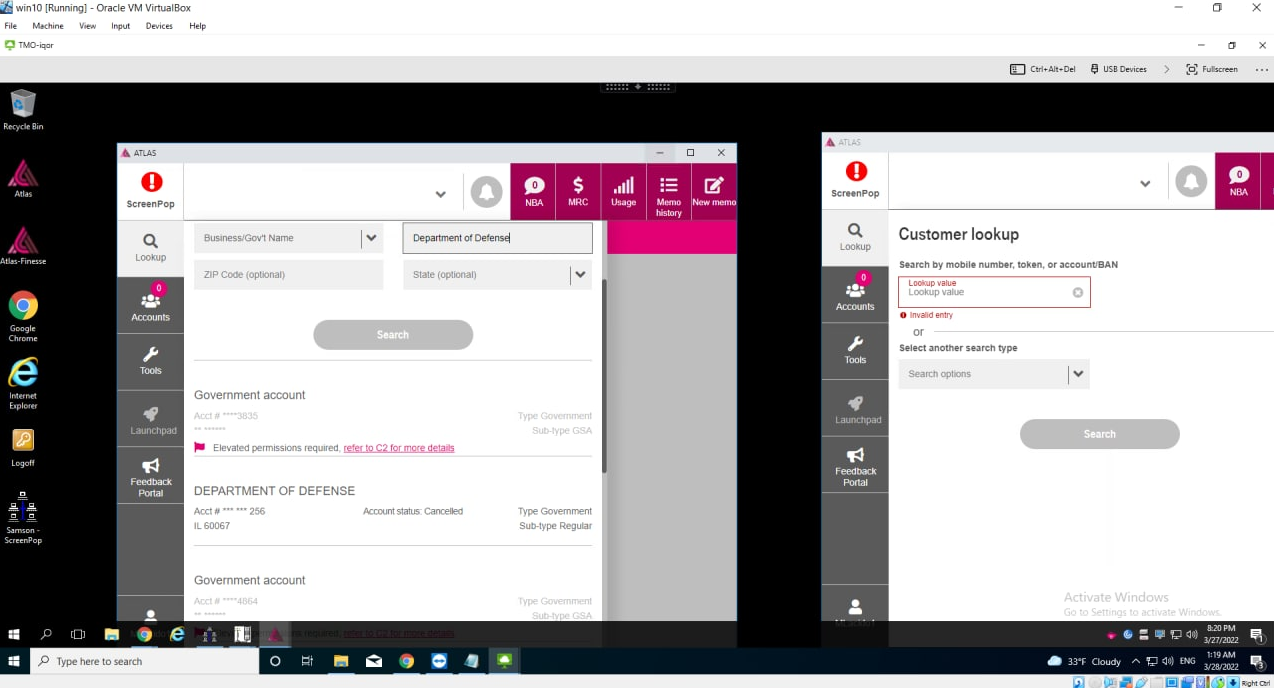
LAPSUS$ chief White/Lapsus Jobs wanting up the Division of Protection in T-Cellular’s inner Atlas system.
After getting access to Atlas, White proceeded to lookup T-Cellular accounts related to the FBI and Division of Protection (see picture above). Thankfully, these accounts had been listed as requiring further verification procedures earlier than any modifications could possibly be processed.
Confronted with more and more vocal pleadings from different LAPSUS$ members to not burn their entry to Atlas and different instruments by attempting to SIM swap authorities accounts, White unilaterally determined to terminate the VPN connection allowing entry to T-Cellular’s community.
The opposite LAPSUS$ members desperately wished to SIM swap some rich targets for cash. Amtrak throws a match, saying “I labored actually laborious for this!” White calls the Atlas entry trash after which kills the VPN connection anyway, saying he wished to concentrate on utilizing their illicit T-Cellular entry to steal supply code.
Maybe to mollify his livid teammates, White modified the topic and instructed them he’d gained entry to T-Cellular’s Slack and Bitbucket accounts. He stated he’d discovered the way to add recordsdata to the digital machine he had entry to at T-Cellular.
Roughly 12 hours later, White posts a screenshot of their non-public chat exhibiting his automated script had downloaded greater than 30,000 supply code repositories from T-Cellular.
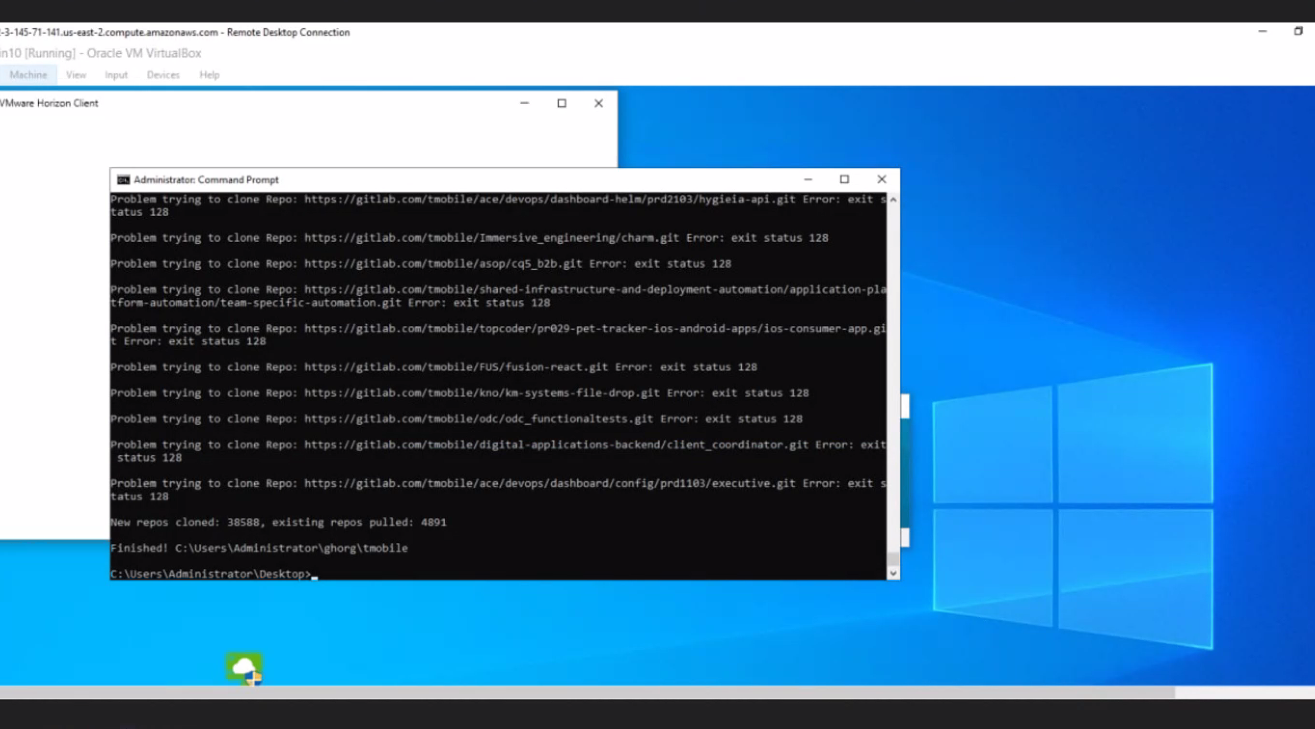
White exhibiting a screenshot of a script that he stated downloaded all obtainable T-Cellular supply code.
In response to questions from KrebsOnSecurity, T-Cellular issued the next assertion:
“A number of weeks in the past, our monitoring instruments detected a foul actor utilizing stolen credentials to entry inner programs that home operational instruments software program. The programs accessed contained no buyer or authorities data or different equally delicate data, and we now have no proof that the intruder was in a position to receive something of worth. Our programs and processes labored as designed, the intrusion was quickly shut down and closed off, and the compromised credentials used had been rendered out of date.”
CONSIDER THE SOURCE
It isn’t clear why LAPSUS$ was so fixated on stealing supply code. Maybe LAPSUS$ thought they may discover within the supply clues about safety weaknesses that could possibly be used to additional hack these corporations and their clients. Possibly the group already had patrons lined up for particular supply code that they had been then employed to obtain. Or possibly it was all one massive Seize the Flag competitors, with supply code being the flag. The leaked chats don’t precisely clarify this fixation.
However it appears probably that the group routinely tried to steal after which delete any supply code it may discover on sufferer programs. That means, it may flip round and demand a cost to revive the deleted knowledge.
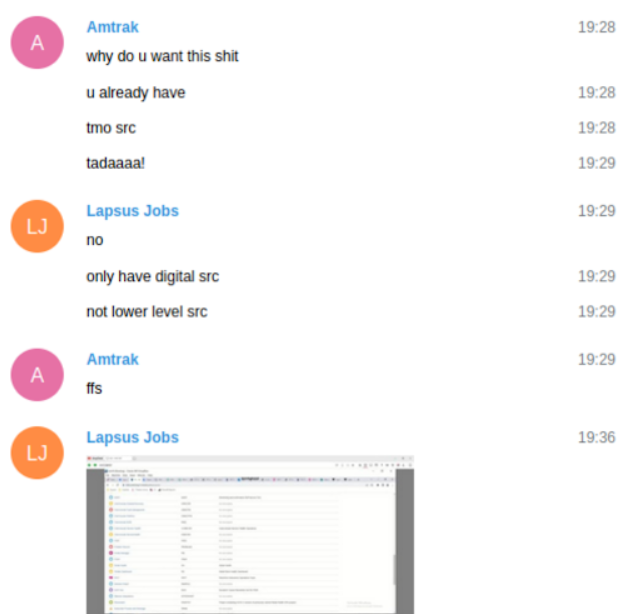
In a single dialog in late March, a LAPSUS$ member posts screenshots and different knowledge indicating they’d gained distant administrative entry to a multi-billion greenback firm. However White is seemingly unimpressed, dismissing the illicit entry as not well worth the group’s time as a result of there was no supply code available.
LAPSUS$ first surfaced in December 2021, when it hacked into Brazil’s Ministry of Well being and deleted greater than 50 terabytes of knowledge saved on the ministry’s hacked servers. The deleted knowledge included data associated to the ministry’s efforts to trace and battle the COVID-19 pandemic in Brazil, which has suffered a disproportionate 13 p.c of the world’s COVID-19 fatalities. LAPSUS$’s subsequent 15 victims had been primarily based both in Latin America or Portugal, based on cyber risk intelligence agency Flashpoint.
By February 2022, LAPSUS$ had pivoted to focusing on high-tech corporations primarily based in the USA. On Feb. 26, LAPSUS$ broke into graphics and computing chip maker NVIDIA. The group stated it stole greater than a terabyte of NVIDIA knowledge, together with supply code and worker credentials.
Dan Goodin at Ars Technica wrote about LAPSUS$’s uncommon extortion demand towards NVIDIA: The group pledged to publish the stolen code until NVIDIA agreed to make the drivers for its video playing cards open-source. In accordance with these chats, NVIDIA responded by connecting to the pc the attackers had been utilizing, after which encrypting the stolen knowledge.
Like many high-tech corporations whose worth is intently tied to their mental property, NVIDIA depends on quite a few applied sciences designed to forestall knowledge leaks or theft. In accordance with LAPSUS$, amongst these is a requirement that solely gadgets which have been accepted or issued by the corporate can be utilized to entry its digital non-public community (VPN).
 These so-called Cellular Machine Administration (MDM) programs retrieve details about the underlying {hardware} and software program powering the system requesting entry, after which relay that data together with any login credentials.
These so-called Cellular Machine Administration (MDM) programs retrieve details about the underlying {hardware} and software program powering the system requesting entry, after which relay that data together with any login credentials.
In a typical MDM setup, an organization will subject staff a laptop computer or smartphone that has been pre-programmed with an information profile, VPN and different software program that permits the employer to trace, monitor, troubleshoot and even wipe gadget knowledge within the occasion of theft, loss, or a detected breach.
MDM instruments additionally can be utilized to encrypt or retrieve knowledge from linked programs, and this was purportedly the performance NVIDIA used to claw again the data stolen by LAPSUS$.
“Entry to NVIDIA worker VPN requires the PC to be enrolled in MDM,” LAPSUS$ wrote in a publish on their public Telegram channel. “With this they had been ready to hook up with a [virtual machine] that we use. Sure, they efficiently encrypted the info. Nevertheless, we now have a backup and it’s protected from scum!!!”
NVIDIA declined to remark for this story.
On March 7, shopper electronics large Samsung confirmed what LAPSUS$ had bragged on its Telegram channel: That the group had stolen and leaked practically 200 GB of supply code and different inner firm knowledge.
The chats reveal that LAPSUS$ stole an important deal extra supply code than they bragged about on-line. Certainly one of White’s curious fascinations was SASCAR, Brazil’s main fleet administration and freight safety firm. White had purchased and talked his means into SASCAR’s programs, and had stolen many gigabytes price of supply code for the corporate’s fleet monitoring software program.
It was dangerous sufficient that LAPSUS$ had simply relieved this firm of invaluable mental property: The chats present that for a number of days White taunted SASCAR staff who had been responding to the then-unfolding breach, at first by defacing the corporate’s web site with porn.
The messages present White maintained entry to the corporate’s inner programs for not less than 24 hours after that, even sitting in on the corporate’s incident response communications the place the safety group mentioned the way to evict their tormentors.
SASCAR is owned by tire trade large Michelin, which didn’t reply to requests for remark.
ENROLLMENT
The leaked LAPSUS$ inner chats present the group spent a substantial amount of time attempting to bypass multi-factor authentication for the credentials they’d stolen. By the point these leaked chat logs had been recorded, LAPSUS$ had spent days relentlessly choosing on one other goal that relied on MDM to limit worker logins: Iqor, a buyer help outsourcing firm primarily based in St. Petersburg, Fla.
LAPSUS$ apparently had no bother utilizing Russian Market to buy entry to Iqor worker programs. “I’ll purchase login when on sale, Russians inventory it each 3-4 days,” Amtrak wrote concerning Iqor credentials on the market within the bot retailers.
The true bother for LAPSUS$ got here when the group tried to evade Iqor’s MDM programs by social engineering Iqor staff into eradicating multi-factor authentication on Iqor accounts they’d bought beforehand. The chats present that again and again Iqor’s staff merely refused requests to switch multi-factor authentication settings on the focused accounts, or make any modifications until the requests had been coming from approved gadgets.
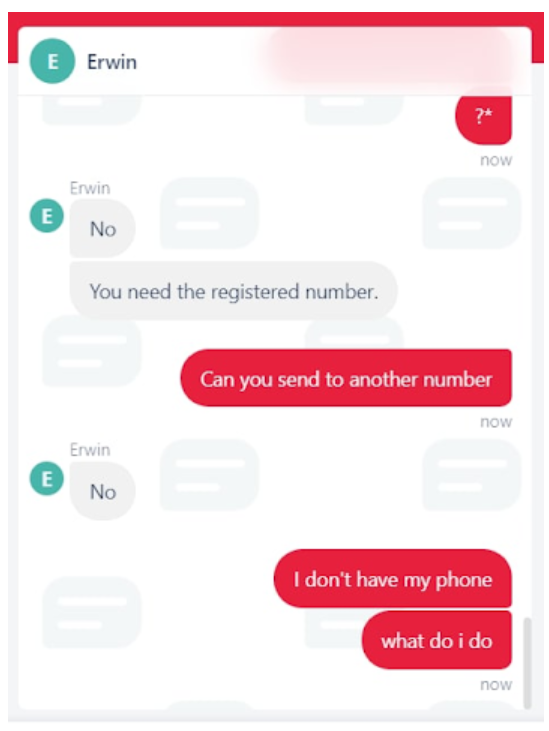
Certainly one of a number of IQOR help engineers who instructed LAPSUS$ no again and again.
After many days of attempting, LAPSUS$ finally gave up on Iqor. On Mar. 22, LAPSUS$ introduced it hacked Microsoft, and commenced leaking 37 gigabytes price of Microsoft supply code.
Like NVIDIA, Microsoft was in a position to stanch a number of the bleeding, reducing off LAPSUS$’s illicit entry whereas the group was within the technique of downloading the entire obtainable supply code repositories alphabetically (the group publicized their entry to Microsoft on the similar time they had been downloading the software program large’s supply code). Because of this, LAPSUS$ was solely in a position to leak the supply for Microsoft merchandise at first of the code repository, together with Azure, Bing and Cortana.
BETRAYAL
LAPSUS$ chief White drew consideration to himself previous to the creation of LAPSUS$ final yr when he bought an internet site known as Doxbin, a long-running and extremely poisonous on-line neighborhood that’s used to “dox” or publish deeply private data on individuals.
Based mostly on the suggestions posted by Doxbin members, White was not a very attentive administrator. Longtime members quickly took to harassing him about numerous parts of the positioning falling into disrepair. That pestering ultimately prompted White to promote Doxbin again to its earlier proprietor at a substantial loss. However earlier than doing so, White leaked the Doxbin consumer database.
White’s leak triggered a swift counterpunch from Doxbin’s workers, which naturally responded by posting on White maybe probably the most thorough dox the discussion board had ever produced — together with movies filmed simply outdoors his residence the place he lives along with his dad and mom in the UK.
The previous and present proprietor of the Doxbin — a longtime cybercriminal who goes by the deal with “KT” — is identical one that leaked these non-public LAPSUS$ Telegram chat logs to KrebsOnSecurity.
In early April, a number of information retailers reported that U.Okay. police had arrested seven individuals aged 15-21 in reference to the LAPSUS$ investigation. However it appears clear from studying these leaked Telegram chats that particular person members of LAPSUS$ had been detained and questioned at totally different occasions over the course of a number of months.
In his chats with different LAPSUS$ members over the last week in March, White maintained that he was arrested 1-2 months prior in reference to an intrusion towards a sufferer referred to solely by the initials “BT.” White additionally appeared unconcerned when Amtrak admits that the Metropolis of London police discovered LAPSUS$ Telegram chat conversations on his cell phone.
Maybe to show his indifference (or possibly simply to screw with Amtrak), White responds by leaking Amtrak’s actual title and telephone quantity to the group’s public Telegram channel. In an ALL CAPS invective of disbelief on the sudden betrayal, Amtrak relates how numerous individuals began calling their residence and threatening their dad and mom in consequence, and the way White successfully outed them to regulation enforcement and the remainder of the world as a LAPSUS$ member.
The overwhelming majority of noteworthy exercise documented in these non-public chats takes place between White and Amtrak, nevertheless it doesn’t appear that White counted Amtrak or any of his fellow LAPSUS$ members as associates or confidants. Quite the opposite, White typically behaved horribly towards everybody within the group, and he notably appeared to take pleasure in abusing Amtrak (who one way or the other all the time got here again for extra).
“Mox,” one of many LAPSUS$ members who reveals up all through these leaked chats, helped the group of their unsuccessful makes an attempt to enroll their cell gadgets with an airline within the Center East to which that they had bought entry. Audio recordings leaked from the group’s non-public Telegram channel embrace a name whereby Mox may be heard talking fluently in Arabic and impersonating an airline worker.
At one level, Mox’s first title briefly reveals up in a video he made and shared with the group, and Mox mentions that he lives in the USA. White then begins looking for and leak Mox’s real-life identification.
When Mox declares he’s so scared he needs to delete his iCloud account, White suggests he can get Mox’s actual title, exact location and different data by making a fraudulent “emergency knowledge request” (EDR) to Apple, by which they use a hacked police division e mail account to request emergency entry to subscriber data beneath the declare that the request can’t await a warrant as a result of somebody’s life is on the road.

White was no stranger to pretend EDRs. White was a founding member of a cybercriminal group known as “Recursion Crew,” which existed between 2020 and 2021. This group principally specialised in SIM swapping targets of curiosity and taking part in “swatting” assaults, whereby pretend bomb threats, hostage conditions and different violent situations are phoned in to police as a part of a scheme to trick them into visiting doubtlessly lethal drive on a goal’s handle.
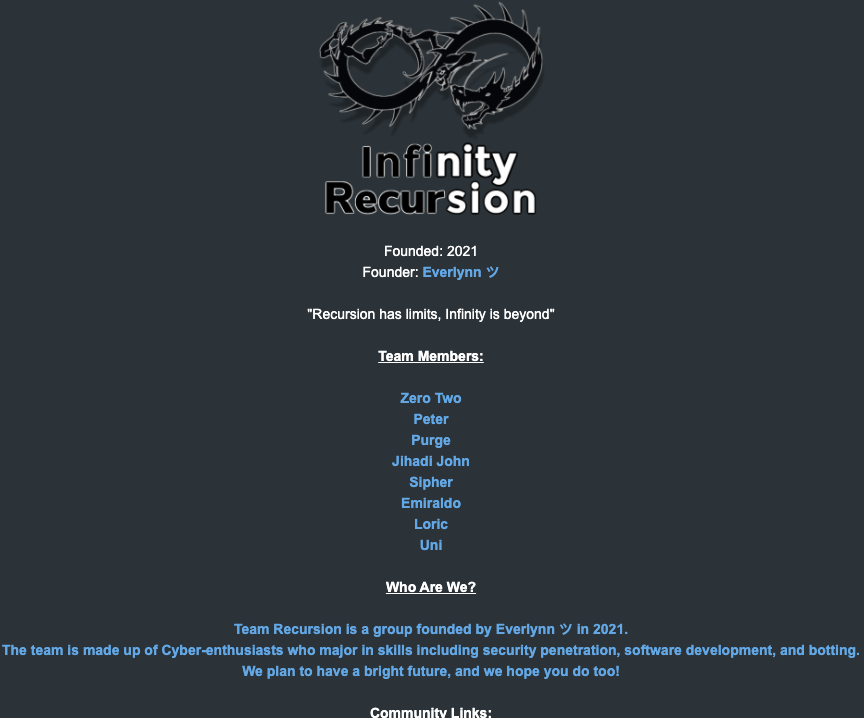
The roster of the now-defunct “Infinity Recursion” hacking group, from which some members of LAPSUS$ hail.
The Recursion Crew was based by a then 14-year-old from the UK who used the deal with “Everlynn.” On April 5, 2021, Everlynn posted a brand new gross sales thread to the cybercrime discussion board cracked[.]to titled, “Warrant/subpoena service (get regulation enforcement knowledge from any service).” The worth: $100 to $250 per request.
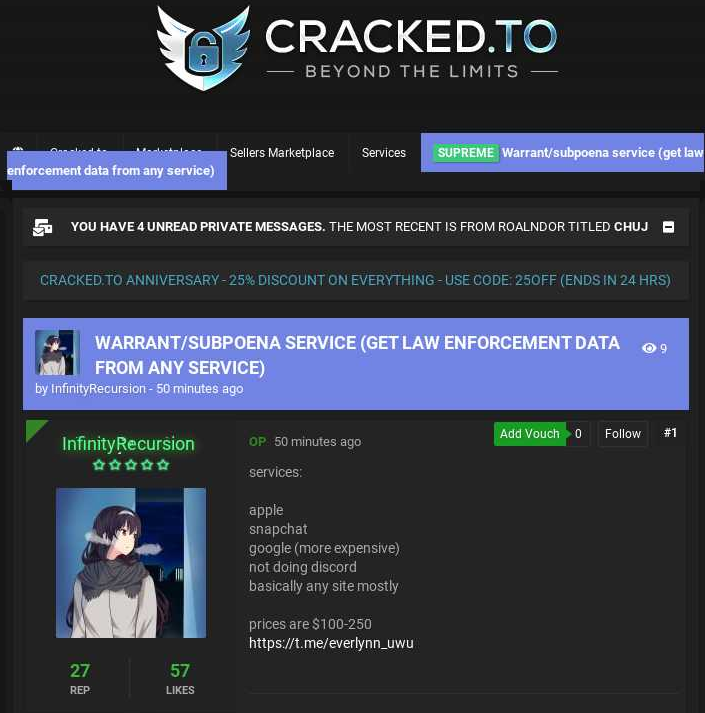
Everlynn promoting a warrant/subpoena service primarily based on pretend EDRs.
Bringing this full circle, it seems Amtrak/Asyntax is identical particular person as Everlynn. As a part of the Recursion Crew, White used the alias “Peter.” A number of LAPSUS$ members quizzed White and Amtrak about whether or not authorities requested about Recursion Crew throughout questioning. In a number of dialogue threads, White’s “Lapsus Jobs” alias on Telegram solutions “sure?” or “I’m right here” when one other member addresses him by Peter.
White dismissed his public doxing of each Amtrak and Mox as their fault for being sloppy with operational safety, or by claiming that everybody already knew their actual identities. Extremely, only a few minutes after doxing Amtrak, White nonchalantly asks them for assist in stealing supply code from one more sufferer agency — as if nothing had simply occurred between them. Amtrak appears soothed by this invitation, and agrees to assist.
On Mar. 30, software program consultancy large Globant was compelled to acknowledge a hack after LAPSUS$ printed 70 gigabytes of knowledge stolen from the corporate, together with clients’ supply code. Whereas the Globant hack has been broadly reported for weeks, the reason for the breach remained hidden in these chat logs: A stolen five-year-old entry token for Globant’s community that also labored.
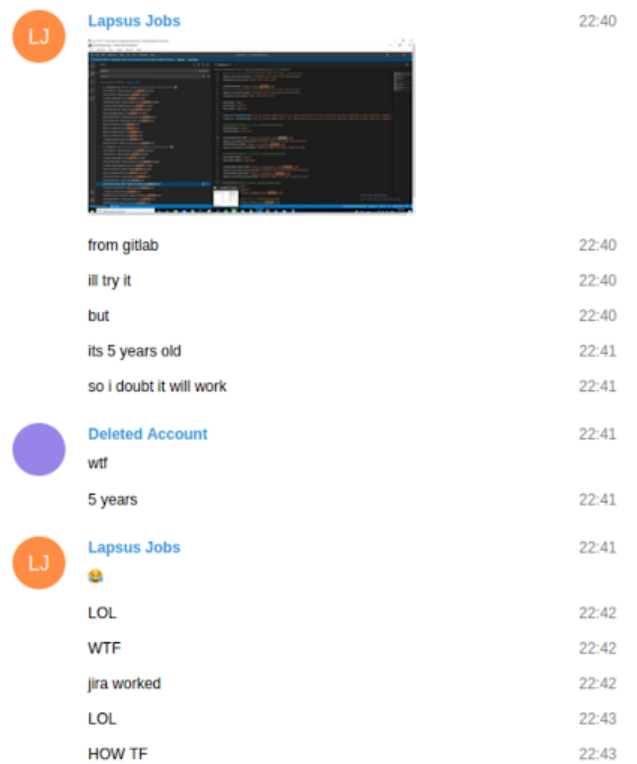
LAPSUS$ members marvel at a 5-year-old stolen authentication cookie nonetheless working once they use it towards Globant to steal supply code.
Globant lists quite a few high-profile clients on its web site, together with the U.Okay. Metropolitan Police, software program home Autodesk and gaming large Digital Arts. In March, KrebsOnSecurity confirmed how White was linked to the theft of 780 GB price of supply code from Digital Arts final summer time.
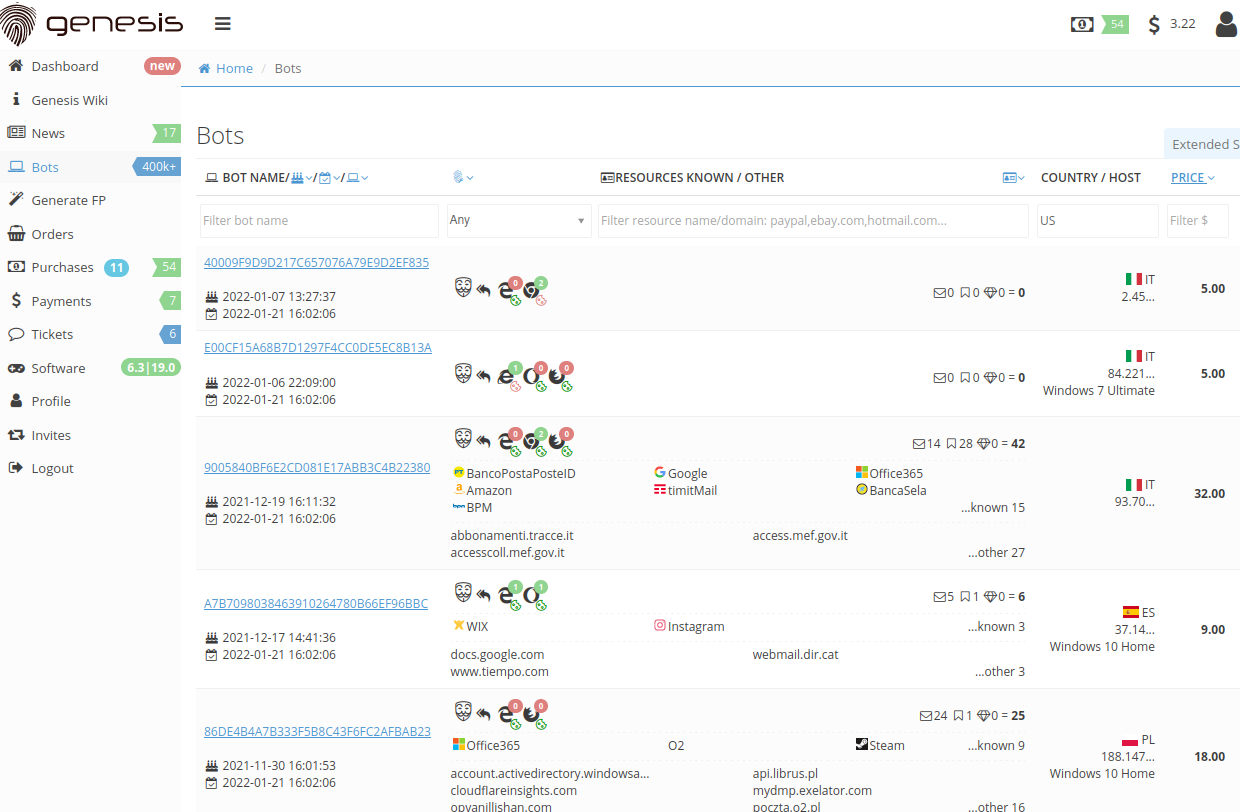
In that assault, the intruders reportedly gained entry to EA’s knowledge after buying authentication cookies for an EA Slack channel from the darkish net market “Genesis,” which gives kind of the identical wares because the Russian Market.
One outstanding side of LAPSUS$ was that its members apparently determined to not personally obtain or retailer any knowledge they stole from corporations they hacked. They had been all so paranoid of police raiding their houses that they assiduously saved the whole lot “within the cloud.” That means, when investigators searched their gadgets, they might discover no traces of the stolen data.
However this technique finally backfired: Shortly earlier than the non-public LAPSUS$ chat was terminated, the group realized it had simply misplaced entry to the Amazon AWS server it was utilizing to retailer months of supply code booty and different stolen knowledge.
“RIP FBI seized my server,” Amtrak wrote. “A lot unlawful shit. It’s crammed with unlawful shit.”
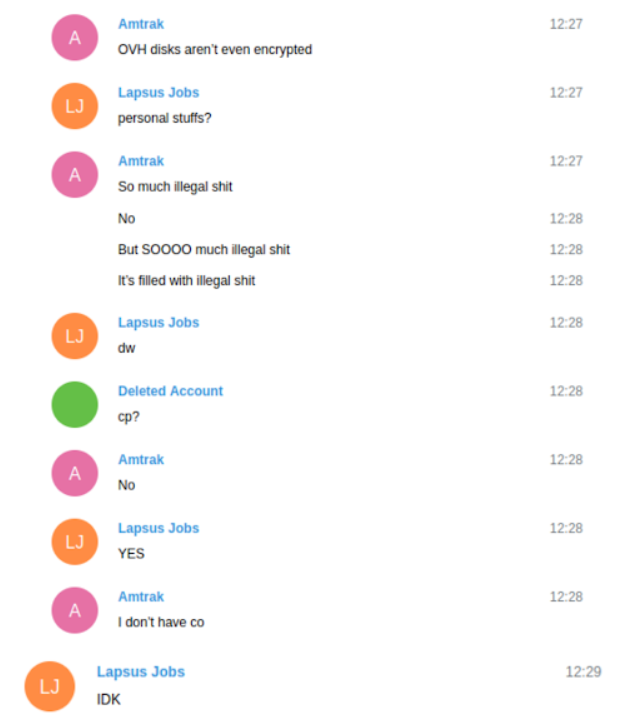
White shrugs it off with the dismissive remark, “U can’t do something about ur server seized.” Then Amtrak replies that they by no means made a backup of the server.
“FFS, THAT AWS HAD TMO SRC [T-Mobile source] code!” White yelled again.
The 2 then make a mad scramble to hack again into T-Cellular and re-download the stolen supply code. However that effort finally failed after T-Cellular’s programs revoked the entry token they had been utilizing to raid the corporate’s supply code stash.
“How they seen?” Amtrak requested White.
“Gitlab auto-revoked, probably,” White replied. “Cloning 30k repos 4 occasions in 24 hours isn’t very regular.”
Ah, the irony of a felony hacking group that makes a speciality of stealing and deleting knowledge having their stolen knowledge deleted.
It’s outstanding how typically LAPSUS$ was in a position to pay just a few {dollars} to purchase entry to some hacked machine at an organization they wished to interrupt into, after which efficiently parlay that into the theft of supply code and different delicate data.
What’s much more outstanding is that anybody can entry darkish net bot retailers like Russian Market and Genesis, which implies bigger corporations in all probability needs to be paying somebody to usually scrape these felony bot companies, even shopping for again their very own worker credentials to take these susceptible programs off the market. As a result of that’s in all probability the only and most cost-effective incident response cash should buy.