WordPress is without doubt one of the hottest and thus generally used content material administration programs (CMS) on the internet. Nonetheless, it has a specific downside with add-on, extension, and plug-in authors abandoning their initiatives, and subsequently leaving gaping holes in web site safety. A working example has been highlighted by the Wordfence weblog this week, which discusses a extreme vulnerability that customers of the Kaswara Fashionable WPBakery Web page Builder Addons at the moment are prey to.
The Kaswara Addon was deserted by its writer earlier than an arbitrary file add vulnerability, tracked as CVE-2021-24284, got here to mild—and due to this fact it has by no means been patched. WordPress customers who should not vigilant, or don’t pay anybody or for any service to be vigilant for them, can simply fall behind on core and extension updates. Furthermore, some plugins grow to be out of date, or might be changed by new inbuilt performance or significantly better options as time and expertise strikes ahead. Kaswara Fashionable WPBakery Web page Builder Addons have a vulnerability that permits for one thing very unhealthy—it may be used as a route “to add malicious PHP recordsdata to an affected web site, resulting in code execution and full web site takeover.” In fact that may be only the start of a really slippery downward slope on your web site’s content material, rating, and repute.
It’s endorsed that any customers of Kaswara Fashionable WPBakery Web page Builder Addons deactivate after which purge them ASAP. An alternate trendy and usually up to date addon with comparable performance might be sought whether it is wanted. Even when you have this addon and it’s not activated in your web site, it ought to nonetheless be deleted.
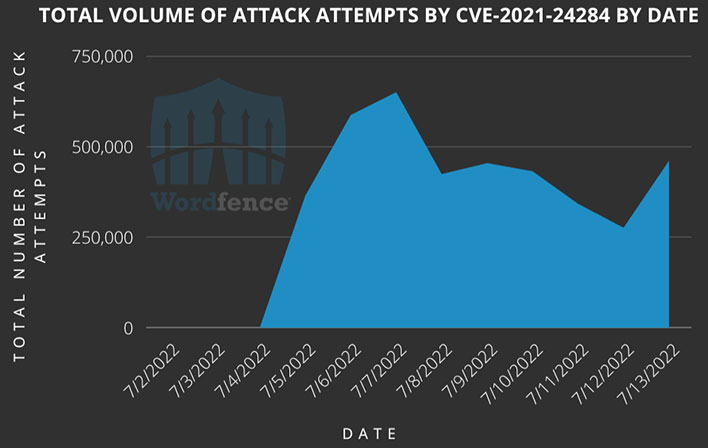
Whereas websites like HotHardware at the moment are making the information about this addon vulnerability mainstream, it has been well-known by menace actors for 10 or 11 days. Wordfence notes that it has blocked almost half one million assault makes an attempt a day since early July, assaults which unprotected websites with this addon would fall sufferer to. The makers of Wordfence say that roughly 1.6M websites underneath its safety have been focused repeatedly by attackers searching for out this vulnerability.
In fact, Wordfence promotes its plugin within the weblog submit concerning Kaswara Fashionable WPBakery Web page Builder Addons and CVE-2021-24284. Nonetheless, it’s fairly justified in doing so, on condition that customers of the Wordfence plugin for WordPress, even the free tier, have had safety in opposition to the CVE-2021-24284 vulnerability since mid-Could.
You’ll be able to learn extra concerning the Kaswara Fashionable WPBakery Web page Builder Addons, CVE-2021-24284, and Wordfence through the supply weblog submit. Additionally, the weblog lists the highest 10 IP addresses from the place exploits for CVE-2021-24284 are tried, which is helpful if you happen to want to blacklist them from entry to your WordPress web site.


