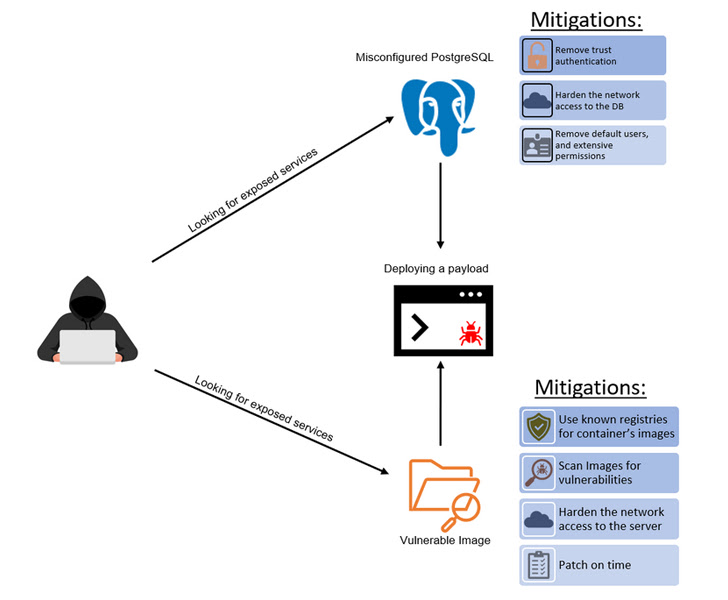
The risk actors behind the Kinsing cryptojacking operation have been noticed exploiting misconfigured and uncovered PostgreSQL servers to acquire preliminary entry to Kubernetes environments.
A second preliminary entry vector method entails using susceptible photos, Sunders Bruskin, safety researcher at Microsoft Defender for Cloud, mentioned in a report final week.
Kinsing has a storied historical past of concentrating on containerized environments, usually leveraging misconfigured open Docker daemon API ports in addition to abusing newly disclosed exploits to drop cryptocurrency mining software program.
The risk actor, up to now, has additionally been found using a rootkit to cover its presence, along with terminating and uninstalling competing resource-intensive companies and processes.
Now in keeping with Microsoft, misconfigurations in PostgreSQL servers have been co-opted by the Kinsing actor to realize an preliminary foothold, with the corporate observing a “great amount of clusters” contaminated on this method.
The misconfiguration pertains to a belief authentication setting, which might be abused to connect with the servers sans any authentication and obtain code execution ought to the choice be set as much as settle for connections from any IP deal with.
“Typically, permitting entry to a broad vary of IP addresses is exposing the PostgreSQL container to a possible risk,” Bruskin defined.
The choice assault vector targets servers with susceptible variations of PHPUnit, Liferay, WebLogic, and WordPress which can be inclined to distant code execution with the intention to run malicious payloads.
What’s extra, a latest “widespread marketing campaign” concerned the attackers scanning for open default WebLogic port 7001, and if discovered, executing a shell command to launch the malware.
“Exposing the cluster to the Web with out correct safety measures can go away it open to assault from exterior sources,” Bruskin mentioned. “As well as, attackers can acquire entry to the cluster by benefiting from recognized vulnerabilities in photos.”