Over the previous decade, we have seen a dramatic uptick in cloud migrations. On-premises options have gotten a factor of the previous, and the cloud is turning into the default within the current. However why cloud, and why now?
Many organizations are at the moment present process a digital transformation. A lot of that is expedited, on account of the COVID-19 pandemic. Shifting to the cloud provides quite a few advantages—scalability, agility, and price discount being a few of the most important. Legacy options require organising extra bodily servers, which will increase complexity and operational effort, resulting in increased prices. In the meantime, cloud lets us do the whole lot—and extra—with only a few clicks.
The transfer to the cloud poses new challenges. One of many easiest methods attackers can get to a corporation’s crown jewels within the cloud is by clearing assault paths by means of a mix of community entry and permissions. In what’s rapidly turning into a go-to technique, many attackers use cloud-native privilege escalation methods like PassRole to achieve privileged entry. The smallest drift in an atmosphere can open up these assault paths in seconds, creating utter insanity for a enterprise. With the precise privileges, knowledge exfiltration takes mere moments and is nearly unimaginable to detect.
To show a majority of these assault paths, DevOps and safety groups can use machine-learning capabilities embedded in a cloud-native software safety platform (CNAPP) answer to detect irregular permissions, correlate all of the indicators, and seek for privileges that collide with public exposures and vulnerabilities.
One of many issues we have seen most steadily, and one which’s tough to trace and catch, is additional permissions being granted to many customers inside a tenant. In these instances, most permissions are unused, and attackers can take benefit. A CNAPP answer can detect irregular permissions of identities inside a tenant utilizing particular machine studying methodologies.
Our definition for “irregular” is straightforward: actionable + most dangerous = irregular. As an example, when customers in a given group every have roughly the identical set of permissions in an atmosphere, however one consumer has additional permissions in one other atmosphere, we think about the additional permissions irregular.
In case of outliers over knowledge that consists of a lot of options, the native machine studying fashions would often be PCA, DBSCAN, LOF, or Isolation Forest. Nonetheless, we found that the proper mannequin is a genetic algorithm. Genetic algorithms purpose to detect mutations inside a collection of genes.
How precisely can we try this? Let’s take a look at a selected instance.
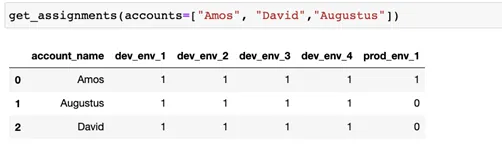
Within the desk above, we are able to see that Amos has some additional permission within the manufacturing atmosphere, which we think about irregular. Let’s now convert that graph to a DNA vector (DNA project).
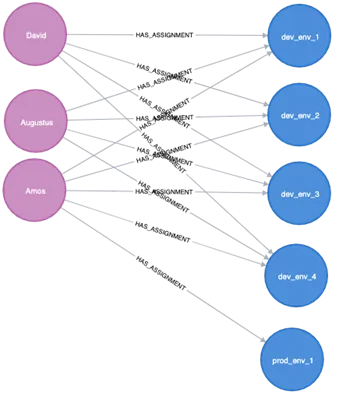
We see right here that Amos has mutations. The purpose is to seek for shut communities which have additional essential permissions—solely then might it’s thought of an anomaly. Additionally, if the communities are removed from one another, it is not essentially anomalous.
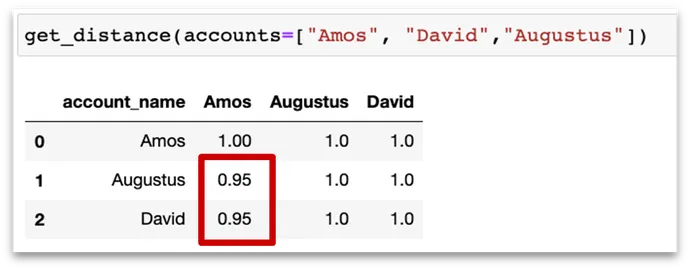
After extra in-depth ML calculations to eradicate false positives, you may find yourself with a genetic algorithm that may assist detect outliers with irregular permissions. It is quick, easy, and efficient. Attempting to carry out this sort of evaluation with a legacy strategy would require a large handbook effort to first perceive the enterprise affect of every permission, after which detect the extreme permissions. Alternatively, an ML-based strategy suggests a self-learning technique with out the necessity to perceive each permission, serving to to expedite the method.
With cloud threats continually evolving, machine/deep-learning detection-based strategies are going to turn out to be a necessity when evaluating CNAPP options. Do not anticipate that subsequent drift to activate a series of catastrophic occasions—get forward of the curve of detecting your subsequent breach with the ability of machine studying.
Learn extra Associate Views from Zscaler.


