A menace actor working to additional Iranian objectives is alleged to have been behind a set of disruptive cyberattacks in opposition to Albanian authorities companies in mid-July 2022.
Cybersecurity agency Mandiant mentioned the malicious exercise in opposition to a NATO state represented a “geographic growth of Iranian disruptive cyber operations.”
The July 17 assaults, in line with Albania’s Nationwide Company of Data Society, compelled the federal government to “briefly shut entry to on-line public companies and different authorities web sites” due to a “synchronized and complicated cybercriminal assault from exterior Albania.”
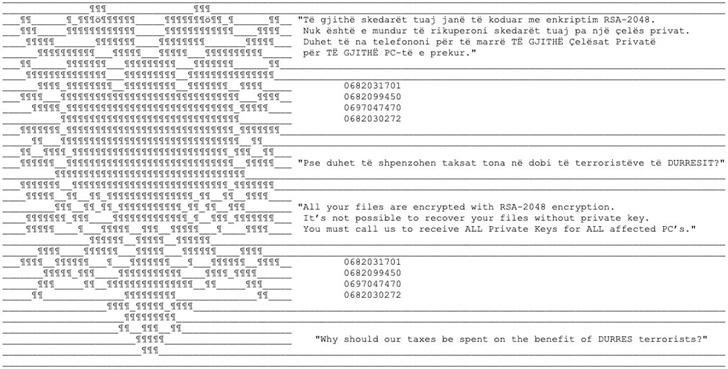
The politically motivated disruptive operation, per Mandiant, entailed the deployment of a brand new ransomware household referred to as ROADSWEEP that included a ransom word with the textual content: “Why ought to our taxes be spent on the good thing about DURRES terrorists?”
A entrance named HomeLand Justice has since claimed credit score for the cyber offensive, with the group additionally allegedly claiming to have used a wiper malware within the assaults. Though the precise nature of the wiper is unclear as but, Mandiant mentioned an Albanian person submitted a pattern for what’s referred to as ZeroCleare on July 19, coinciding with the assaults.
ZeroCleare, first documented by IBM in December 2019 as a part of a marketing campaign focusing on the economic and power sectors within the Center East, is designed to wipe the grasp boot report (MBR) and disk partitions on Home windows-based machines. It is believed to be a collaborative effort between completely different Iranian nation-state actors, together with OilRig (aka APT34, ITG13, or Helix Kitten).
Additionally deployed within the Albanian assaults was a beforehand unknown backdoor dubbed CHIMNEYSWEEP that is able to taking screenshots, itemizing and amassing recordsdata, spawning a reverse shell, and supporting keylogging performance.
The implant, moreover sharing quite a few code overlaps with ROADSWEEP, is delivered to the system by way of a self-extracting archive alongside decoy Microsoft Phrase paperwork that comprise pictures of Massoud Rajavi, the erstwhile chief of Individuals’s Mojahedin Group of Iran (MEK).
The earliest iterations of CHIMNEYSWEEP date again to 2012 and indications are that the malware might have been utilized in assaults aimed toward Farsi and Arabic audio system.
The cybersecurity agency, which was acquired by Google earlier this 12 months, mentioned it did not have sufficient proof linking the intrusions to a named adversarial collective, however famous with reasonable confidence that a number of unhealthy actors working in help of Iran’s goals are concerned.
The connections to Iran stem from the truth that the assaults happened lower than every week previous to the World Summit of Free Iran convention on July 23-24 close to the port metropolis of Durres by entities opposing the Iranian authorities, notably the members of the MEK.
“Using ransomware to conduct a politically motivated disruptive operation in opposition to the federal government web sites and citizen companies of a NATO member state in the identical week an Iranian opposition teams’ convention was set to happen could be a notably brazen operation by Iran-nexus menace actors,” the researchers mentioned.
The findings additionally come two months after the Iranian superior persistent menace (APT) group tracked as Charming Kitten (aka Phosphorus) was linked to an assault directed in opposition to an unnamed development firm within the southern U.S.