The assault infrastructure used to goal Cisco within the Could 2022 incident was additionally employed in opposition to an tried compromise of an unnamed workforce administration options holding firm a month earlier in April 2022.
Cybersecurity agency Sentire, which disclosed the findings, raised the likelihood that the intrusions might be the work of a legal actor often called mx1r, who is claimed to be a member of the Evil Corp affiliate cluster dubbed UNC2165.
Evil Corp, the progenitors of the notorious Dridex banking trojan, have, through the years, refined their modus operandi to run a collection of ransomware operations to sidestep sanctions imposed by the U.S. Treasury in December 2019.
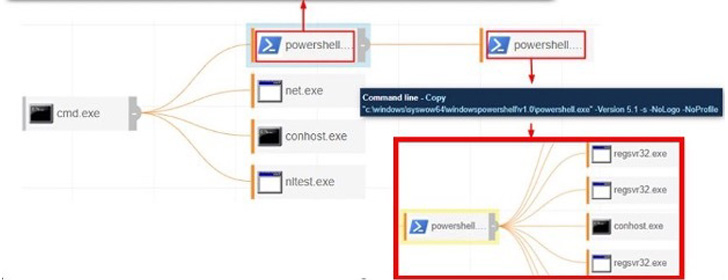
Preliminary entry to the corporate’s IT community was made potential by utilizing stolen Digital Personal Community (VPN) credentials, adopted by leveraging off-the-shelf instruments for lateral motion and gaining deeper entry into the sufferer’s atmosphere.
“Utilizing Cobalt Strike, the attackers have been in a position to achieve an preliminary foothold and hands-on-actions have been instant and swift from the time of preliminary entry to when the attacker was in a position to register their very own Digital Machine on the sufferer’s VPN community,” eSentire famous.
mx1r’s ties to UNC2165 stems from overlaps in ways and strategies with that of UNC2165, together with staging a Kerberoasting assault in opposition to the Energetic Listing service and the usage of Distant Desktop Protocol (RDP) entry for propagating inside the firm’s community.
The connections however, the Cobalt Strike “HiveStrike” infrastructure used to mount the assault is claimed to match that of a Conti ransomware affiliate beforehand recognized to deploy Hive and Yanluowang strains, the latter of which has since posted recordsdata stolen from the Cisco breach in late Could 2022 to its information leak website.
The networking gear maker attributed the incident to an preliminary entry dealer (IAB) with hyperlinks to 3 totally different collectives: UNC2447, LAPSUS$, and Yanluowang ransomware.
“It appears unlikely — however not unimaginable — that Conti would lend its infrastructure to Evil Corp,” eSentire stated. In mild of UNC2165’s latest pivot to LockBit ransomware, the corporate stated “it’s extra believable that the Evil Corp affiliate/UNC2165 could also be working with considered one of Conti’s new subsidiaries.”
“It is also potential that preliminary entry was brokered by an Evil Corp affiliate however in the end offered off to Hive operators and its associates,” it additional added.