How the Information Mesh safety sample ensures that an enterprise Information Mesh and its Information Merchandise are secure and safe

Information is the foundational constructing block of a contemporary enterprise. However far too usually we see headlines highlighting the catastrophic penalties brought on by gaps in safety practices. These safety gaps are available in many flavours from leaky perimeters to errant workers and all the things in between.
Information safety is the observe of addressing these gaps to guard digital info from unauthorized entry, corruption, or theft all through its whole lifecycle. Information Mesh provides a novel alternative to guard knowledge.
This text will discover how the Information Mesh Safety Sample:
- Secures boundaries for Information Merchandise, the structure quantum of Information Mesh.
- Offers granular safety for knowledge inside Information Merchandise.
- Ensures communication between Information Merchandise in an enterprise Information Mesh are secure, safe, and monitored.
- Architects a safe run-time surroundings for every Information product in an enterprise Information Mesh.
- Transforms safety violations into persistently formatted and properly outlined “safety occasions”.
- Integrates into an enterprise safety regime by publishes safety occasions to enterprise operational and safety administration instruments.
This text assumes that you’ve got a high-level understanding of Information Mesh. Should you want some background info on Information Mesh, there are a variety of nice articles can be found right here (patterns), right here (structure), right here (rules) and right here (classes discovered). For readers, a full set of Information Mesh patterns can be found right here and right here.
Information Mesh provides distinctive alternatives to guard knowledge. First, it gives Information Merchandise which supply well-defined knowledge boundaries the place safety may be utilized. Second, these Information Merchandise have house owners which guarantee there may be clear accountability and duty for the safety of information throughout the area. Third, Information Mesh provides a self-service entry mannequin which gives clear contracts that describes how knowledge is consumed who can, or tries, to devour it. And, lastly, it provides a federated governance method that facilitates monitoring knowledge safety.
The Information Mesh / Information Product Safety Sample illustrates a constant methodology to use safety for an Enterprise Information Mesh and the Information Merchandise that it manages.
Security and safety of an enterprise knowledge is constructed upon a basis of safety insurance policies applied in knowledge merchandise and knowledge mesh elements. At this time, these insurance policies fluctuate by:
- Product (for instance, Oracle vs SQL Server)
- Run-time surroundings (for instance, AWS vs Google)
- Location (for instance, Information Middle vs Cloud)
So, it’s not stunning that knowledge and safety professions lack essential details about their Information Mesh operational, safety, and governance traits, together with:
- Unclear Entry Rights, making it obscure the credentials, roles, and/or permissions required to devour knowledge.
- Inconsistent Safety Insurance policies, making it expensive to stick to regulatory and privateness necessities for knowledge.
- Lack of Utilization Info, making it troublesome to control entry rights to delicate knowledge.
- Delays in Surfacing Safety Violations, inflicting delays in addressing safety points.
- Gaps in Safety Context, making it troublesome and time consuming to analysis safety violations.
The Information Mesh / Information Product Safety Sample addresses every of those points.
Recognizing Information Merchandise are the structure “quantum” of a Information Mesh (ie. a Information Mesh is an amalgam of a number of knowledge merchandise), Information Mesh Safety Sample defines entry safety controls factors for Information Merchandise:
- On the perimeter of Information Merchandise,
- Inside Information Merchandise, and,
- Between Information Merchandise.

On the perimeter of Information Merchandise, this sample acknowledges the next safety insurance policies:
- Run-time Setting Safety: Whereas these insurance policies are closely dependent upon the run-time surroundings for the Information Product, a number of of the various distributors supply safety for containers (Docker), pods (Kubernetes), VMs, throughout on-premises and cloud environments.
- API Entry Management: OpenAPI specs, the preferred API contract definition, permits safety schemas and “scopes” (use with OAUTH2) to be outlined which dictate credentials to entry a Information Product.
Inside Information Merchandise, this sample acknowledges a number of safety insurance policies:
- Position-Primarily based Entry Management: Entry to Information Merchandise could also be restricted to those who have a specific function or group.
- Row-Primarily based Entry Management: Safety insurance policies enable particular person rows are protected; This can be necessary the place elevated privileges are required to entry subsets of a given desk inside a Information Product.
- Attribute-Primarily based Entry Management: Safety insurance policies enable particular person columns to be protected; Elevated privileges could also be required to entry delicate fields inside a Information Product.
- Information Encryption and Tokenization: Information at-rest is encrypted or tokenized based mostly upon the sensitivity of the info inside a Information Product.
Between Information Merchandise, this sample acknowledges the next safety insurance policies:
- Normal Community Safety Controls: these are insurance policies that an enterprise establishes to control entry to community and join elements.
- Subject / Stream-Primarily based Safety Controls: Safety between matters / streams on an Occasion Spine are functionally similar to API safety (i.e. required “scopes” and roles).
There are a number of supporting capabilities for this sample:
- An Enterprise Id E-book of File: The grasp repository for identification and maintains relationships to assigned teams and roles (Lively listing, cloud listing, mainframe listing and so on.).
- A Schema / Specification Registry: Maintains “scopes” and knowledge / occasion constructions required to help versatile safety insurance policies for APIs and occasions
- Governance Controls: Insurance policies outline regulatory and privateness constraints for an information product
The Information Mesh Safety Sample additionally captures safety violations at these management factors and fashions all safety violations Safety Occasions. Since every Information Product could also be applied utilizing completely different applied sciences, this sample normalizes of uncooked safety violations into persistently formatted safety occasions.
This sample additionally gives the potential to help the wants of varied shoppers:
- Builders use this sample to assist design purposes with strategies of securely consuming Information Merchandise.
- Information Engineers use this sample to construct and implement safe Information Merchandise and Information Mesh elements and working environments.
- Information Scientists use this sample to grasp safety credentials required to entry and devour Information Merchandise.
- Safety Workers use this sample to seize and diagnose safety violations to make sure an enterprise Information Mesh runs in a secure and safe method.
- Information Governance Workers use this sample to grasp utilization patterns and guarantee regulatory and privateness constraints are adhered to.
The Information Mesh / Information Product Safety Sample gives entry controls to make sure Information Merchandise are entry solely by licensed entities or individuals. It additionally devices Information Merchandise in an enterprise Information Mesh to seize and emit safety violations that are reworked into “Safety Occasions” that present a concise and detailed safety info consumable by operations and safety workers.
This sample is illustrated in three sections, every outlines key steps in a typical utilization state of affairs describing safety flows inside an information product (Determine 2), between knowledge merchandise in a Information Mesh (Determine 3), and the way various kinds of customers work together within the Information Mesh Safety Sample (Determine 4).

Safety flows inside a Information Product happens as proven in Determine 2 (above). In step 1 and a pair of a person or utility generates a safety violation (for instance, by making an attempt entry knowledge for which the person has inadequate privileges). In step 3 uncooked safety occasions are captured and reworked into “Safety Occasions”. These safety occasions are then filtered and logged (step 4) and saved in an immutable change/audit log for additional evaluation or historic evaluate. Every safety occasion is subsequently made accessible (step 5) in a easy person interface (a “knowledge product catalog”) that makes it simple to view safety points. Lastly, safety occasions are additionally propagated by way of APIs or occasions (step 6) to permit them to be ingested in enterprise manufacturing monitoring and safety options.
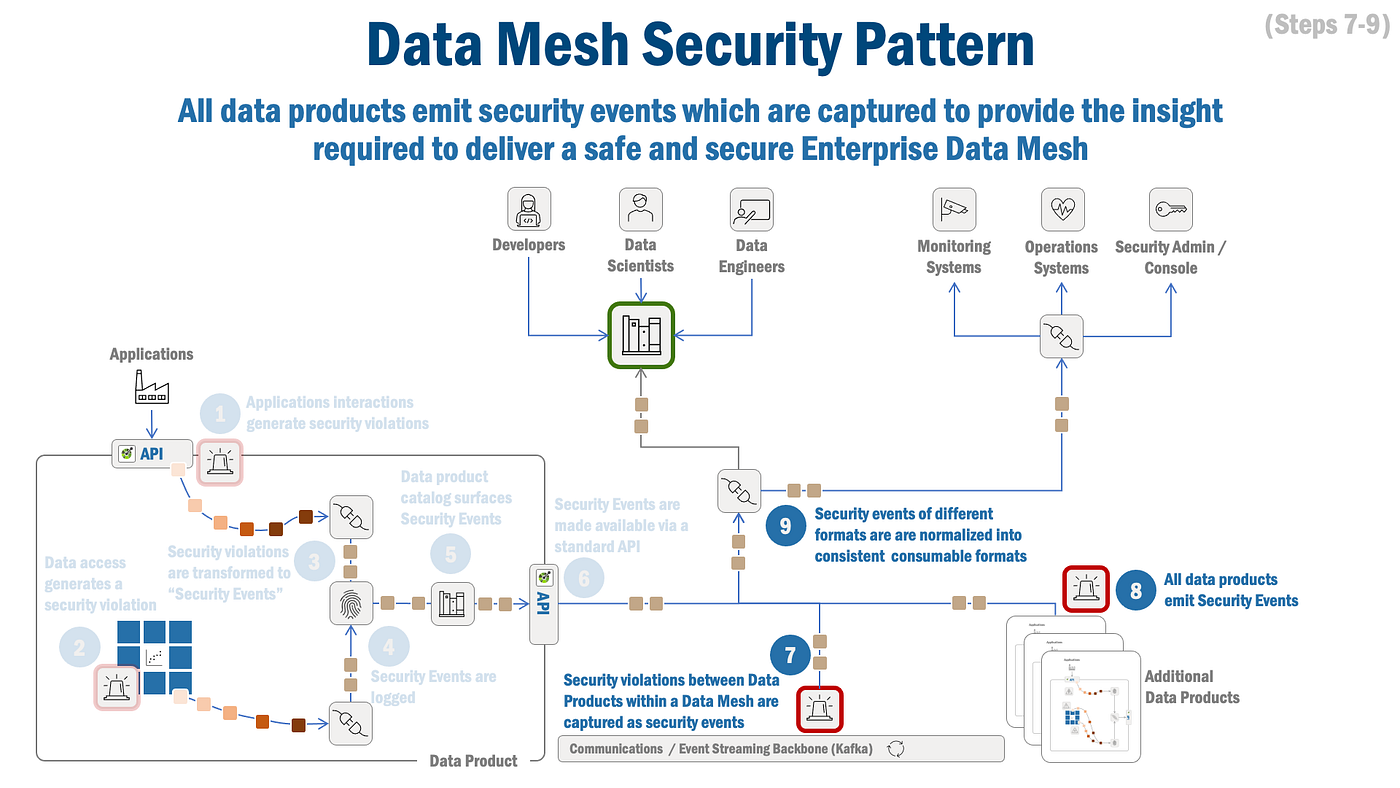
In Determine 3 above, we are able to see that safety violations between Information Merchandise — for instance, when an information product has inadequate permissions so as to add to a subject — are captured and reworked (step 7) into Safety Occasions. As said earlier, all knowledge merchandise emit safety occasions (step 8) that happen between Information Merchandise throughout the enterprise Information Mesh. Every safety occasion is then formatted for ingestion by enterprise operations and safety methods (step 9).

In Determine 4, above, safety occasions are retailer in an Enterprise Information Product Catalog (step 10). This enables varied customers — builders, knowledge scientists, and knowledge engineers — to view safety points (step 11), whereas additionally permitting safety occasions to be emitted to straightforward enterprise consoles (monitoring, operations administration, and safety purposes.
Earlier within the article we posed a number of challenges that an applicable safety functionality should tackle. Let’s revisit them to see how the Information Mesh / Information Product Safety Sample addresses them:
- Unclear Entry Rights: Information Mesh and Information Product safety surfaces role-based-access management (RBAC) and, the place wanted, attribute-based-access-control in a Information Product Catalog making it simple to grasp the credentials, roles, and/or permissions required to devour knowledge.
- Inconsistent Safety Insurance policies: Information Mesh and Information Product safety introduces a constant role-based-access management (RBAC) and, the place wanted, Attribute-based-access-control making it simple to grasp the credentials, roles, and/or permissions required to devour knowledge.
- Lack of Utilization Info: Information Mesh and Information Product safety surfaces utilization knowledge in a Information Product Catalog in addition to safety entry violations making it simple to control entry rights to delicate knowledge.
- Delays in Surfacing Safety Violations: Information Mesh and Information Product safety captures safety violations and emits them instantly to a safety or operations console permitting well timed analysis and determination of safety issues.
- Gaps in Safety Context: Information Mesh and Information Product safety present wealthy context (who, what, when and so on.) about safety violations making it simple and well timed to analysis and resolve safety violations.
Current headlines have clearly proven that insecure knowledge surroundings may have a catastrophic affect to a corporation. By capturing safety violations and instantly surfacing the safety violation and its context, a complete Information Mesh and Information Product safety method permits safety points to be rapidly recognized, recognized, and resolved. And by utilizing this info, it gives the required perception to safe your personal Enterprise Information Mesh and supply the protection wanted by data-intensive organizations.
***
All photographs on this doc besides the place in any other case famous have been created by Eric Broda (the creator of this text). All icons used within the photographs are inventory PowerPoint icons and are free from copyrights.
The opinions expressed on this article are mine alone and don’t essentially mirror the views of my purchasers.


