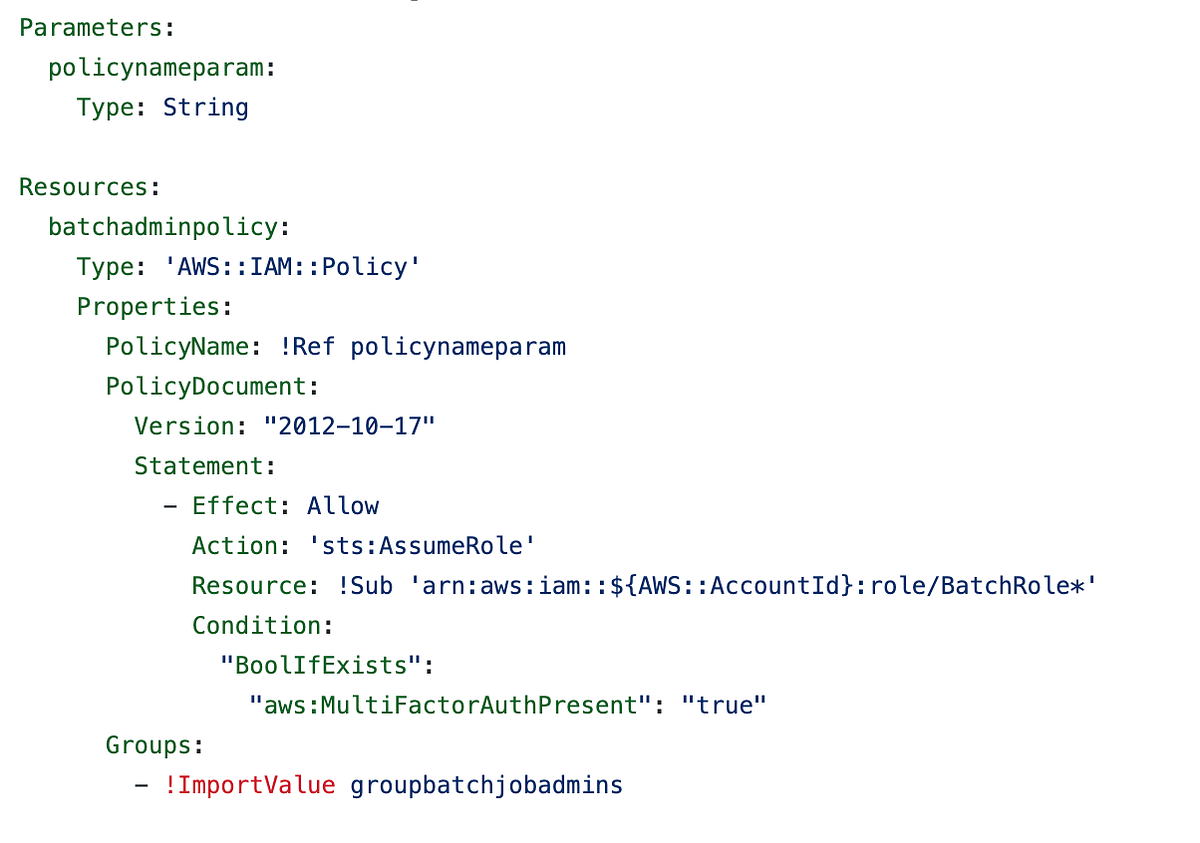
Particulars of coverage analysis and including MFA to our batch job insurance policies
It is a continuation of my collection on Automating Cybersecurity Metrics.
On this submit we’re going so as to add the MFA situation to our IAM insurance policies created within the final two posts on this collection. I already defined the reasoning behind our architectural and coverage selections within the prior posts on this collection so please learn these first should you haven’t already. There are two locations the place we must always have the ability to add an efficient MFA situation — in our person coverage and the belief coverage related to our batch job position.
AWS IAM Coverage Circumstances
We will add a Situation component to our AWS IAM insurance policies to solely enable actions when sure circumstances are met. The next documentation has some particulars about Situation operators.
Basically if you write your coverage with a situation operator, you’re checking {that a} explicit key within the request to the AWS API has a selected worth.
Solely carry out the requested motion if key = worth
What keys and values can we test? We’ll must seek the advice of the AWS documentation for which keys exist by which sort of requests and what their values ought to be.
International Situation Keys
The primary sort of keys we will use in a situation assertion are these current globally in each request. Meaning should you add situation logic for these keys in an IAM coverage of any sort you may moderately ensure they are going to exist and will be evaluated — however that doesn’t imply they are going to be set the best way you would possibly anticipate as was coated in prior posts the place I wrote about how MFA applies to IAM roles.
Discover that considered one of these keys is aws:MultiFactorAuthPresent. We may additionally restrict the age of the MFA session. We’ll begin with the merely checking MFA is current to start out. We could add different circumstances later if wanted.
IAM and STS Situation Keys
Along with world keys, you may leverage different forms of keys particular to completely different providers in AWS requests. For instance, there are a selection of keys associated to IAM and STS:
What you’ll want to know right here is which situation keys are relevant to the authentication technique these utilized in your cloud surroundings. If you’re making an attempt to make use of IAM circumstances and your customers are logging in by way of SAML, these circumstances could not apply. Contemplate that AWS SSO (now AWS Id Heart) leverages SAML.
Service Situation Keys
Every AWS Service could have extra keys that you need to use in AWS IAM circumstances to create fine-grained insurance policies for the precise providers you’re utilizing in your AWS account.
Situation Keys in Useful resource Insurance policies
You may also use situation keys in useful resource insurance policies similar to S3 bucket insurance policies:
As all the time, don’t assume issues are working as you anticipate — check every IAM Coverage you implement.
And that is the purpose the place I remind my readers that there’s no simple button for multi-cloud as I focus on at IANS occasions. You want to perceive the fine-grained particulars of every cloud supplier. I will be presenting on multi-cloud safety at an IANS Analysis occasion in LA in October if all goes in accordance with plan and also you need to study extra:https://www.iansresearch.com/what-we-do/occasions/boards/particulars/2022/10/4/2022-forums/2022-los-angeles
Writing our Situation Logic
The world situation context keys documentation recommends that you just write your situation logic as follows and warns in opposition to different approaches that will fail.

I’ve transformed this to yaml since that’s what we’re utilizing for our CloudFormation templates.
Situation:
"BoolIfExists":
"aws:MultiFactorAuthPresent": "false"
Let’s have a look at the situation line with the important thing and worth:
"aws:MultiFactorAuthPresent": "false"
Observe that this situation is checking if MFA is *not* current, so we might want to affiliate this with a deny assertion.
If aws:MultiFactorAuthPresent equals false then the situation evaluates to TRUE, so apply the related DENY assertion to the request.
Deny Assertion Logic
If we wished so as to add a deny assertion to our coverage it could appear to be this:
- Impact: Deny
Motion: '*'
Useful resource: '*'
Situation:
"BoolIfExists":
"aws:MultiFactorAuthPresent":"false"
This results in the necessity to understanding priority and the way a number of statements work collectively in an IAM Coverage which you’ll be able to examine right here on this documentation on IAM Coverage Analysis logic:
What if we’ve got one assertion that permits an motion however one other assertion that denies actions in an IAM Coverage? We will check out this coverage resolution stream doc from the above documentation:

Within the very first column, the choice logic checks for an express deny. Cease. Sport over. Go to Jail. Don’t not move Go. Don’t gather $200. (For many who don’t perceive that reference it’s from the sport of Monopoly which hopefully no less than a few of my readers performed as a child like I did.)
BoolIfExists
Earlier than you learn this part… I’m solely pondering by way of BoolIfExists right here. I haven’t truly examined this as a result of I made a decision to not use it. It might work completely effective as documented I simply discovered the wording of the documentation and/or the title of the variable complicated in comparison with what I’m used to seeing an “if exists” assemble do in a programming language.
What does the BoolIfExists operator within the assertion above do precisely? To reply that query you’ll want to know how BoolIfExists works.

"If the key is just not current, consider the situation component as TRUE."
So for the needs of our coverage and if I perceive that assertion accurately, it interprets to:
"If [MFAAuthPresent = false] is just not current, consider the situation component as TRUE." Deny the request.
As a result of the “factor” handed into boolifexists is just not MFAAuthPresent, it’s no matter “MFAAuthPresent =false” evaluates to in a standard programming language.
So what if the important thing MFAAuthPresent key is just not within the request in any respect. Does that imply that MFAAuthPresent = false is just not current? I assume it should. So in accordance with the documentation the worth doesn’t exist and the results of the if exists test interprets to true. Deny the request.
However right here’s the factor that appears odd to me. The title of this situation logic operator is BoolIfExists and so I learn the interpretation of the title of the operator along side the assertion within the documentation like this:
If the boolean worth doesn’t exist then “if the boolean worth exists” returns true.
That doesn’t actually make sense does it? Maybe the logic utilized in AWS behind the scenes the place this assertion will get evaluated is completely different than different programming languages or the best way I’m studying this operator title.
Based mostly on a few years of programming, an “if exists” assemble in most languages often interprets to “if the referenced merchandise exists, then return true”.
So I’d learn BoolIfExists if it have been a normal programming language assemble as follows:
If the merchandise exists and it's a boolean, return true, in any other case return false.
To me, if our referenced merchandise is [MFAAuthPresent=false] that interprets to:
If the results of [MFAAuthPresent = false] exists and it's a boolean, then return the results of [MFAAuthPresent = false]. Within the case MFAAuthPresent = true it would not match the situation and the result's false, so the situation fails. The deny assertion won't apply. If MFAAuthPresent = false then it matches the situation requirement and the result's true. The situation succeeds and the DENY assertion will apply.In any other case the worth of [MFAAuthPresent=false] is just not a boolean or it would not exist so return false. The Deny assertion won't apply.
With the above interpretation (which doesn’t match what the AWS documentation states so shouldn’t be right) the “in any other case” portion of the logic signifies that if somebody may take away the MFAAuthPresent key in a request to the API or move in one thing apart from true or false, then the deny assertion would not apply. The request would succeed. Somebody may bypass our MFA requirement with a type of choices.
However the documentation says it really works in any other case, and I’m not utilizing this type of the logic so I am not going to check it additional proper now. If you’re utilizing the above double adverse logic, you would possibly need to check it out with no key or a key that evaluates to one thing apart from true or false affirm it really works the best way the documentation states.
For my functions, plainly it could be a lot less complicated so as to add the next situation to the enable assertion in our coverage.
Situation:
"Bool":
"aws:MultiFactorAuthPresent" : "True"
Observe that I’ve eliminated the “if exists” altogether. The important thing should exist and it should be true. I presume on this case if the important thing doesn’t exist, the logic will consider such that the situation fails. The documentation appears to help this but it surely’s all the time good to check and validate your IAM insurance policies work the best way you anticipate.
Let’s revisit why the documentation is not recommending this strategy over the others and see if any caveats apply to our use case.
This mix of the
Permit,Bool, andtruepermits solely MFA-authenticated requests. This is applicable solely to momentary credentials that help utilizing MFA. This assertion doesn’t enable entry to requests that have been made utilizing long-term entry keys, or to requests made utilizing momentary credentials with out MFA.
I believe the assertion above relating to “long run entry keys” is a bit deceptive or no less than complicated. You should use entry keys to make CLI requests with MFA and the above coverage situation will work as a result of I’ve used it earlier than as I wrote about right here.
I need to get my code executed so I’ll keep on with the less complicated strategy if it really works as anticipated. I’m not involved with different actions that received’t work with MFA as a result of presently the one factor in my coverage is STS:AssumeRole. If I would like so as to add something that doesn’t work with MFA, I may add a separate assertion for that, however to date I don’t anticipate that I’ll want to take action.
Add the MFA situation the person coverage
The primary place we’ll add an MFA situation is in our person coverage. Add the situation logic to our assertion that permits the sts:AssumeRole motion.
batch_job_admins/cfn/policy_batch_job_admins.yaml
https://github.com/tradichel/SecurityMetricsAutomation/blob/important/batch_job_admins/cfn/policy_batch_job_admins.yaml

After making that change navigate to the batch_job_admins listing and run the deploy script to redeploy the coverage we deployed within the final weblog submit on this collection.
Navigate to the folder with the deploy script for the batch admins
https://github.com/tradichel/SecurityMetricsAutomation/blob/important/batch_job_admins/deploy.sh
Run the deploy script to redeploy the coverage with the brand new MFA situation.
./deploy.sh
Add the MFA situation to the batch job position belief coverage
Subsequent add the MFA situation to the batch job belief coverage or AssumeRolePolicyDocument as it’s referred to as in CloudFormation.
batch_job_role/cfn/role_batch_job.yaml
https://github.com/tradichel/SecurityMetricsAutomation/blob/important/batch_job_role/cfn/role_batch_job.yaml

Navigate to the folder with the deploy script for the batch job position:
https://github.com/tradichel/SecurityMetricsAutomation/blob/important/batch_job_role/deploy.sh
Run the next command to redeploy the position we created in our final weblog submit with this new situation.
./deploy.sh POC
Now, hopefully, we’ve got created the situation the place solely our batch job administrator can assume the batch job position and provided that authenticated with MFA. We’ll check this all out in future posts.
Teri Radichel
In the event you preferred this story please clap and observe:
Medium: Teri Radichel or E mail Checklist: Teri Radichel
Twitter: @teriradichel or @2ndSightLab
Requests providers by way of LinkedIn: Teri Radichel or IANS Analysis
© 2nd Sight Lab 2022
All of the posts on this collection:
____________________________________________
Creator:
Cybersecurity for Executives within the Age of Cloud on Amazon

Want Cloud Safety Coaching? 2nd Sight Lab Cloud Safety Coaching
Is your cloud safe? Rent 2nd Sight Lab for a penetration check or safety evaluation.
Have a Cybersecurity or Cloud Safety Query? Ask Teri Radichel by scheduling a name with IANS Analysis.
Cybersecurity & Cloud Safety Sources by Teri Radichel: Cybersecurity and Cloud safety courses, articles, white papers, displays, and podcasts