Safety vulnerabilities have been disclosed in Netcomm and TP-Hyperlink routers, a few of which might be weaponized to attain distant code execution.
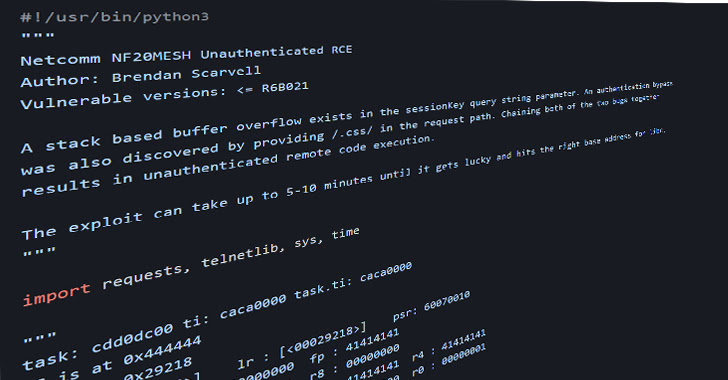
The issues, tracked as CVE-2022-4873 and CVE-2022-4874, concern a case of stack-based buffer overflow and authentication bypass and impression Netcomm router fashions NF20MESH, NF20, and NL1902 working software program variations sooner than R6B035.
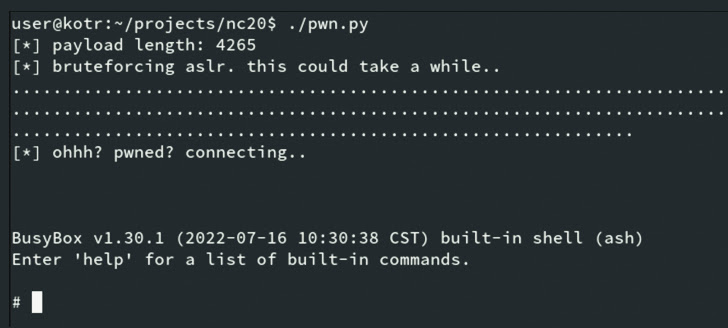
“The 2 vulnerabilities, when chained collectively, allow a distant, unauthenticated attacker to execute arbitrary code,” the CERT Coordination Middle (CERT/CC) stated in an advisory revealed Tuesday.
“The attacker can first achieve unauthorized entry to affected units, after which use these entry factors to realize entry to different networks or compromise the supply, integrity, or confidentiality of knowledge being transmitted from the interior community.”
Safety researcher Brendan Scarvell has been credited with discovering and reporting the problems in October 2022.
In a associated growth, CERT/CC additionally detailed two unpatched safety vulnerabilities affecting TP-Hyperlink routers WR710N-V1-151022 and Archer-C5-V2-160201 that might result in info disclosure (CVE-2022-4499) and distant code execution (CVE-2022-4498).
CVE-2022-4499 can be a side-channel assault concentrating on a operate used to validate the entered credentials. “By measuring the response time of the susceptible course of, every byte of the username and password strings could also be simpler to guess,” CERT/CC stated.
Microsoft researcher James Hull has been acknowledged for disclosing the 2 bugs. The Hacker Information has reached out to TP-Hyperlink for a remark, and we are going to replace the story if we hear again.