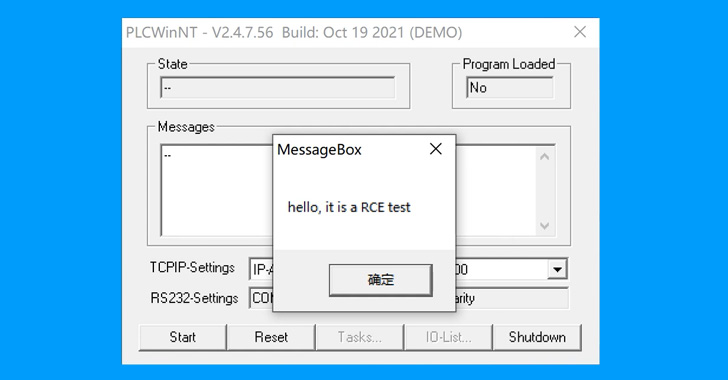
CODESYS has launched patches to deal with as many as 11 safety flaws that, if efficiently exploited, might lead to data disclosure and a denial-of-service (DoS) situation, amongst others.
“These vulnerabilities are easy to use, and they are often efficiently exploited to trigger penalties reminiscent of delicate data leakage, PLCs getting into a extreme fault state, and arbitrary code execution,” Chinese language cybersecurity agency NSFOCUS mentioned. “Together with industrial eventualities on the sphere, these vulnerabilities might expose industrial manufacturing to stagnation, gear injury, and many others.”
CODESYS is a software program suite utilized by automation specialists as a growth surroundings for programmable logic controller purposes (PLCs).
Following accountable disclosure between September 2021 and January 2022, fixes had been shipped by the German software program firm final week on June 23, 2022. Two of the bugs are rated as Important, seven as Excessive, and two as Medium in severity. The problems collectively have an effect on the next merchandise –
- CODESYS Improvement System previous to model V2.3.9.69
- CODESYS Gateway Shopper previous to model V2.3.9.38
- CODESYS Gateway Server previous to model V2.3.9.38
- CODESYS Net server previous to model V1.1.9.23
- CODESYS SP Realtime NT previous to model V2.3.7.30
- CODESYS PLCWinNT previous to model V2.4.7.57, and
- CODESYS Runtime Toolkit 32 bit full previous to model V2.4.7.57
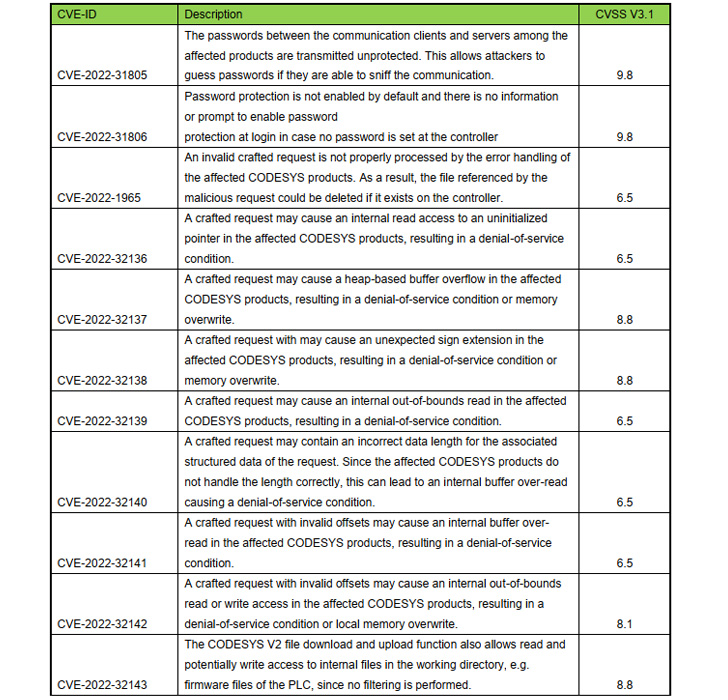
Chief among the many flaws are CVE-2022-31805 and CVE-2022-31806 (CVSS scores: 9.8), which relate to the cleartext use of passwords used to authenticate earlier than finishing up operations on the PLCs and a failure to allow password safety by default within the CODESYS Management runtime system respectively.
Exploiting the weaknesses couldn’t solely enable a malicious actor to grab management of the goal PLC gadget, but in addition obtain a rogue challenge to a PLC and execute arbitrary code.
A majority of the opposite vulnerabilities (from CVE-2022-32136 to CVE-2022-32142) could possibly be weaponized by a beforehand authenticated attacker on the controller to result in a denial-of-service situation.
In a separate advisory revealed on June 23, CODESYS mentioned it additionally remediated three different flaws in CODESYS Gateway Server (CVE-2022-31802, CVE-2022-31803, and CVE-2022-31804) that could possibly be leveraged to ship crafted requests to bypass authentication and crash the server.
Apart from making use of patches in a well timed style, it is advisable to “find the affected merchandise behind the safety safety units and carry out a defense-in-depth technique for community safety.”